Pentagon report reveals Hegseth jeopardized US troops’ mission by using Signal app for sensitive discussions
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pentagon watchdog finds Hegseth put US troops mission at risk with Signal group chat on Houthi bombing
1. BLUF (Bottom Line Up Front)
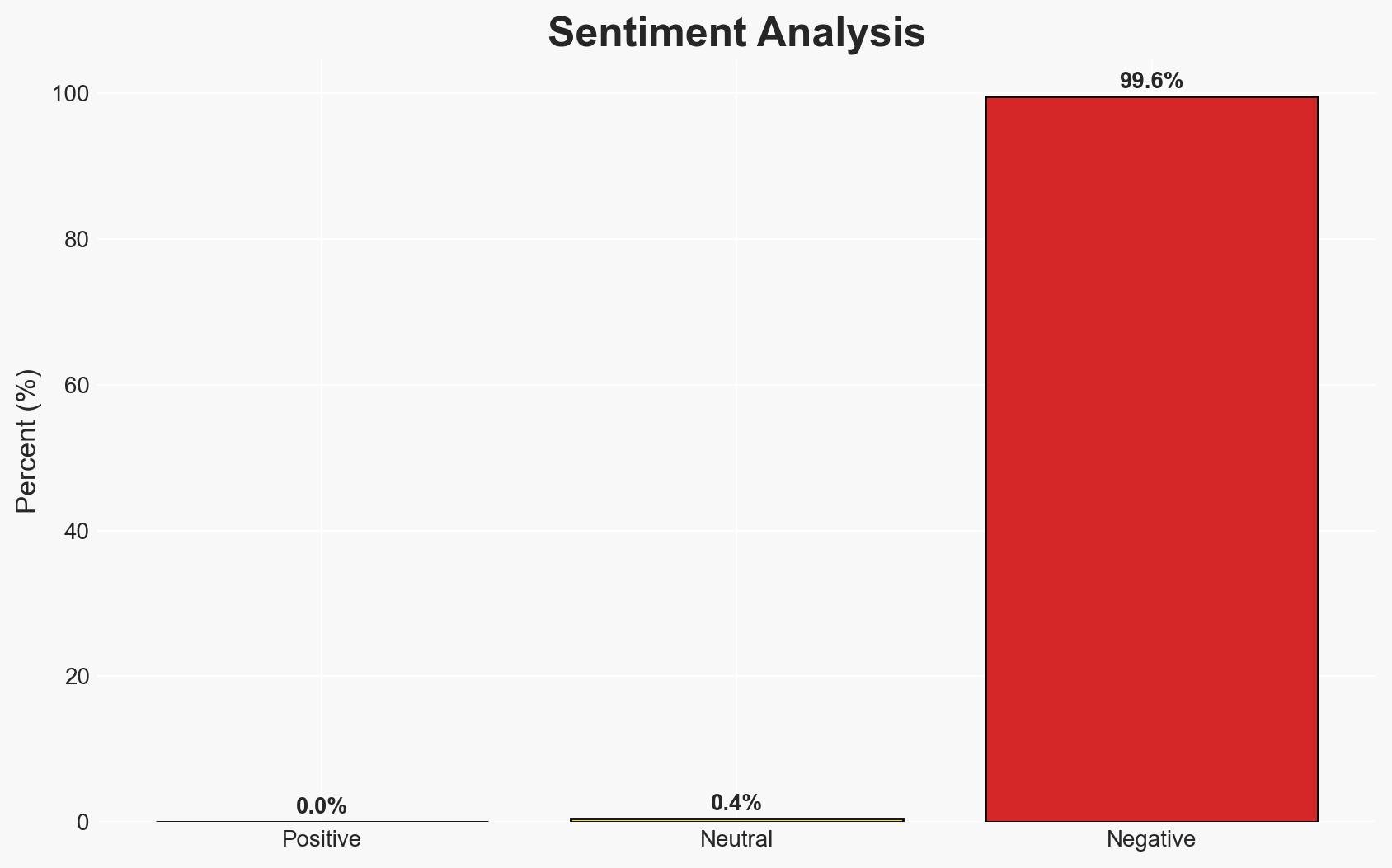
The Pentagon Inspector General’s report indicates that War Secretary Pete Hegseth compromised operational security by using an unsecured messaging app to discuss sensitive military operations. This action potentially endangered U.S. personnel and mission success in Yemen. The report underscores a pattern of poor judgment, raising concerns about leadership efficacy. Overall, the confidence level in this assessment is moderate due to incomplete information on the full extent of the security breach.
2. Competing Hypotheses
- Hypothesis A: Hegseth’s use of Signal for operational details was a significant breach of security protocol, posing a real threat to U.S. military operations. Evidence includes the Inspector General’s findings and the Senate Intelligence Committee’s reaction. However, uncertainties remain about the exact content shared and its potential impact.
- Hypothesis B: Hegseth’s actions, while technically a breach, did not materially compromise operational security. Supporting this is the lack of evidence that classified information was improperly disclosed. Contradicting evidence includes the pattern of behavior noted by the Inspector General.
- Assessment: Hypothesis A is currently better supported due to the Inspector General’s findings and the broader pattern of behavior. Indicators that could shift this judgment include further details on the content shared and any subsequent operational impacts.
3. Key Assumptions and Red Flags
- Assumptions: Hegseth’s actions were not an isolated incident; the information shared was sensitive enough to pose a risk; the Inspector General’s report is accurate and comprehensive.
- Information Gaps: The specific content of the Signal messages and their direct impact on operations remain unclear.
- Bias & Deception Risks: Potential bias in the Senate Intelligence Committee’s response; Hegseth’s public statements may downplay the severity of the breach.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of leadership practices within the Department of Defense and impact U.S. military credibility. If not addressed, it may erode trust in leadership and operational security protocols.
- Political / Geopolitical: Potential for political fallout and calls for leadership changes, affecting U.S. defense policy continuity.
- Security / Counter-Terrorism: Increased risk to ongoing operations and personnel safety if similar breaches occur.
- Cyber / Information Space: Highlighting vulnerabilities in communication practices, potentially inviting adversarial exploitation.
- Economic / Social: Limited direct economic impact, but potential social implications if public trust in military leadership is diminished.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of communication practices within the Department of Defense; implement immediate training on secure communication protocols.
- Medium-Term Posture (1–12 months): Develop and enforce stricter guidelines for the use of personal devices in official capacities; enhance oversight mechanisms.
- Scenario Outlook:
- Best: Improved communication security protocols prevent future breaches.
- Worst: Continued breaches lead to significant operational failures and loss of life.
- Most-Likely: Incremental improvements in security practices with ongoing political scrutiny.
6. Key Individuals and Entities
- Pete Hegseth, War Secretary
- Senate Intelligence Committee
- Pentagon Inspector General
- Mark Warner, Senate Intelligence Committee Vice Chairman
7. Thematic Tags
Counter-Terrorism, operational security, military leadership, communication protocols, Yemen conflict, Pentagon oversight, Signal app, information security
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us