Persistent Security Flaws Allow Attackers to Exploit Common Vulnerabilities in Identity and Access Systems
Published on: 2026-02-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Attackers keep finding the same gaps in security programs
1. BLUF (Bottom Line Up Front)
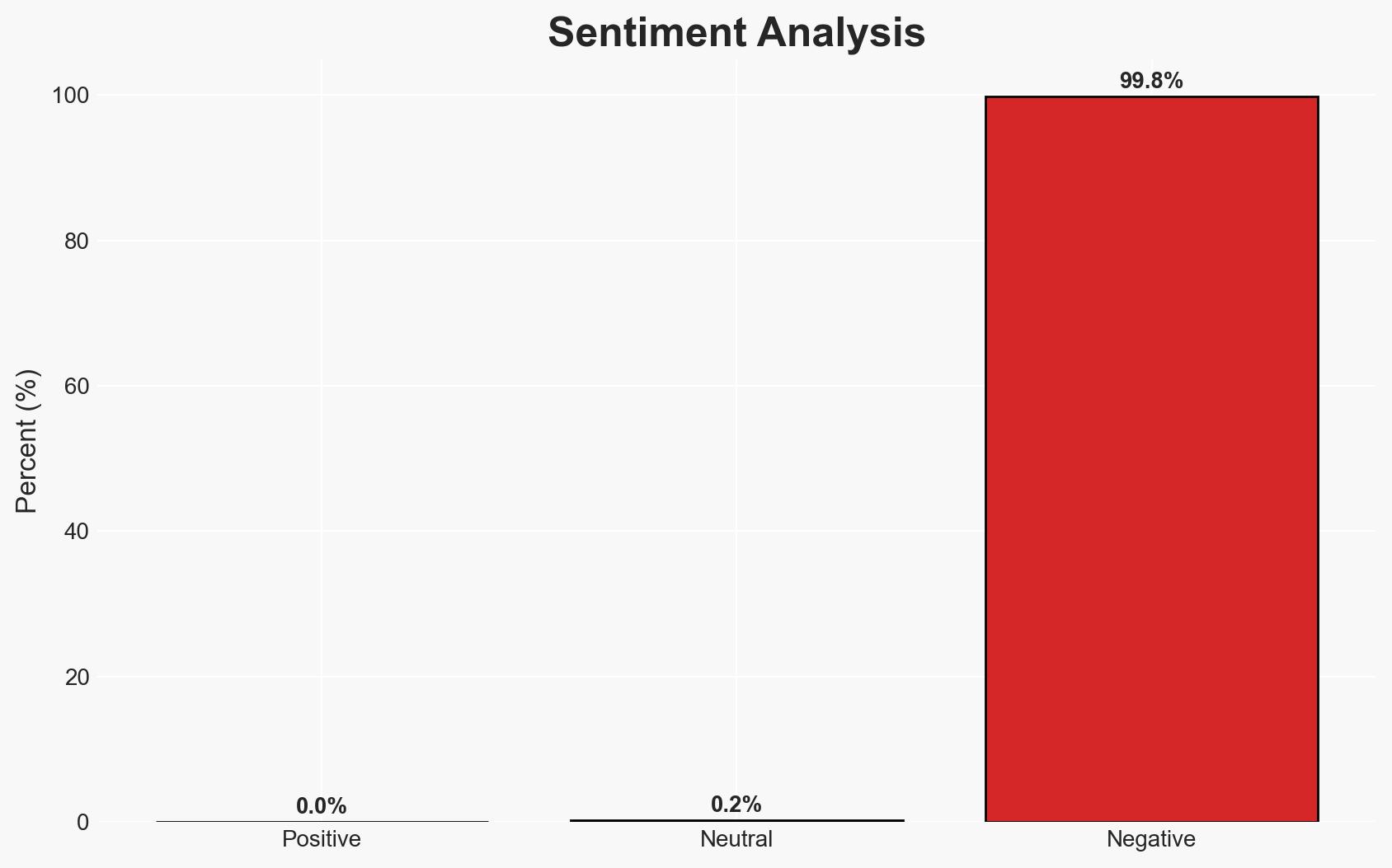
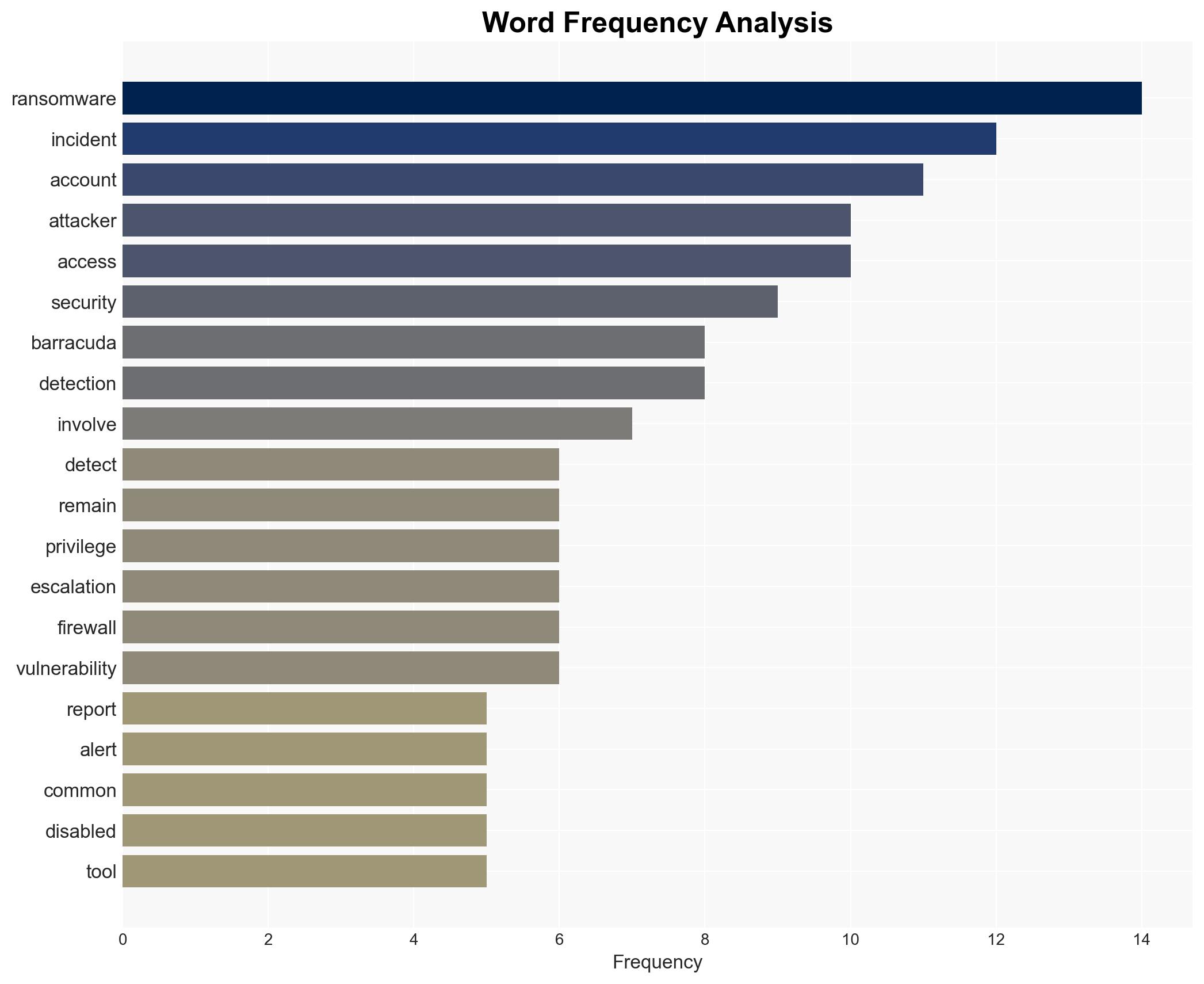
Attackers continue to exploit predictable weaknesses in identity systems, third-party access, and perimeter devices, with identity-based compromises being particularly prevalent. The reliance on basic access and configuration failures rather than advanced malware suggests a persistent vulnerability in enterprise environments. This situation affects organizations using Microsoft 365 and other common IT infrastructure. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Attackers are primarily exploiting identity and access management (IAM) weaknesses due to inadequate security practices. This is supported by the high frequency of identity alerts and suspicious logins. However, the exact contribution of IAM failures versus other factors remains uncertain.
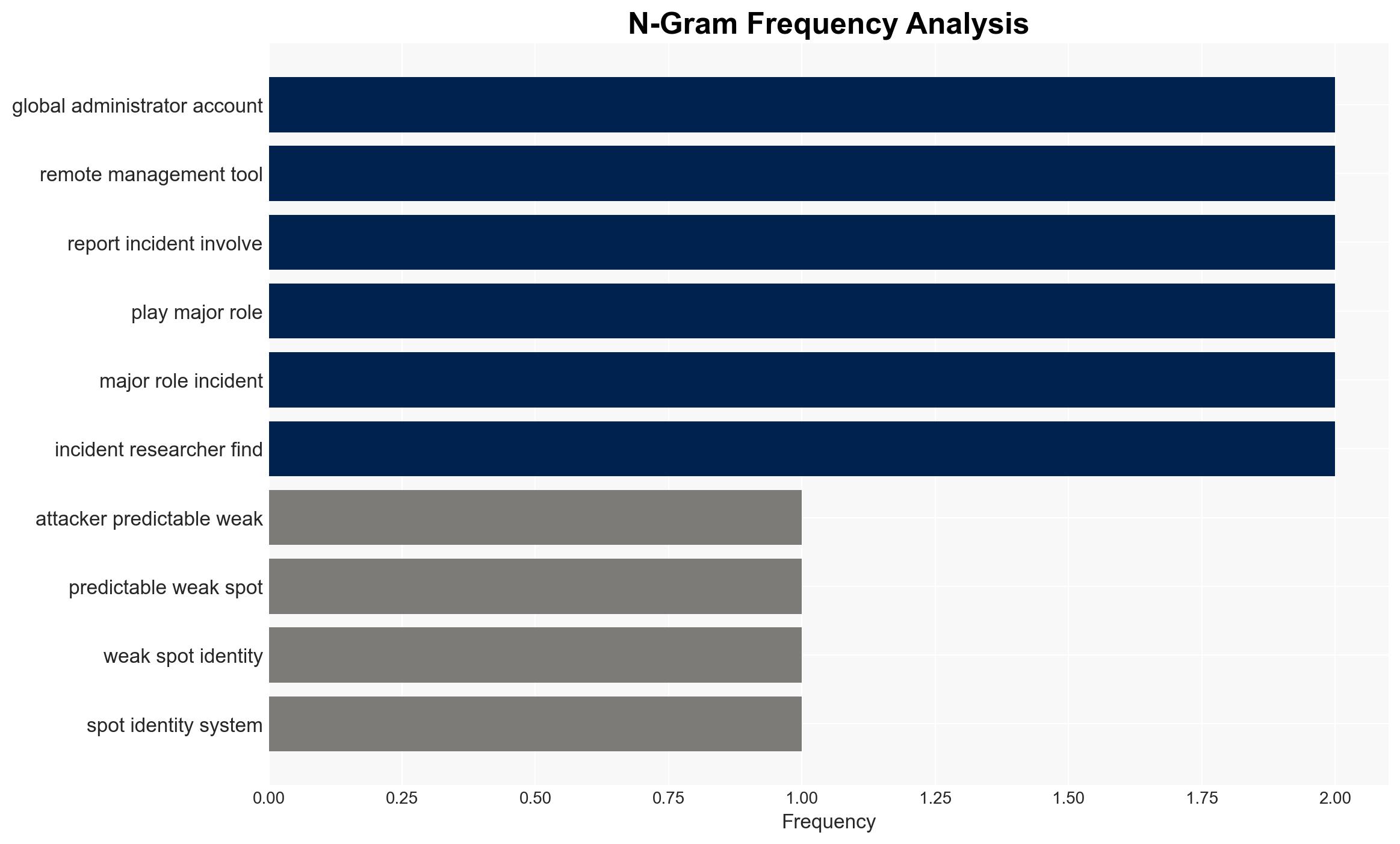
- Hypothesis B: Attackers are leveraging legitimate tools and standard workflows to mask their activities, making detection difficult. This is evidenced by the use of remote management tools and privilege escalation activities that mimic normal IT operations. The extent to which this tactic is more effective than exploiting IAM weaknesses is less clear.
- Assessment: Hypothesis A is currently better supported due to the high volume of identity-based detections. Indicators such as a significant shift in the types of tools used or a decrease in identity alerts could alter this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have not significantly improved IAM practices; attackers prefer low-effort, high-reward tactics; remote management tools remain inadequately secured.
- Information Gaps: Detailed data on the effectiveness of current IAM improvements; comparative analysis of attack success rates across different security practices.
- Bias & Deception Risks: Potential bias in data from Barracuda due to its vested interest in promoting its security solutions; attackers may be intentionally using varied tactics to obscure primary methods.
4. Implications and Strategic Risks
The persistence of these vulnerabilities could lead to increased cyber incidents, affecting organizational trust and operational integrity. Over time, this may necessitate regulatory changes and increased investment in cybersecurity.
- Political / Geopolitical: Potential for increased international tensions if state actors are implicated in exploiting these vulnerabilities.
- Security / Counter-Terrorism: Heightened risk of cyber-attacks on critical infrastructure, potentially impacting national security.
- Cyber / Information Space: Increased sophistication in cyber operations, with a focus on exploiting common IT systems and tools.
- Economic / Social: Potential economic impact due to data breaches and loss of consumer confidence in digital services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of identity systems and third-party access; conduct security audits focusing on IAM and remote management tools.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in IAM improvements and employee training on security best practices.
- Scenario Outlook: Best: Significant reduction in identity-based compromises due to improved practices. Worst: Escalation in successful attacks leading to major breaches. Most-Likely: Continued exploitation of IAM weaknesses with incremental improvements in detection and response.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, identity management, remote access, privilege escalation, cyber threats, IT infrastructure, security vulnerabilities
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us