Pete Hegseth Linked to Yet Another Serious Security Breach – Gizmodo.com
Published on: 2025-04-21
Intelligence Report: Pete Hegseth Linked to Yet Another Serious Security Breach – Gizmodo.com
1. BLUF (Bottom Line Up Front)
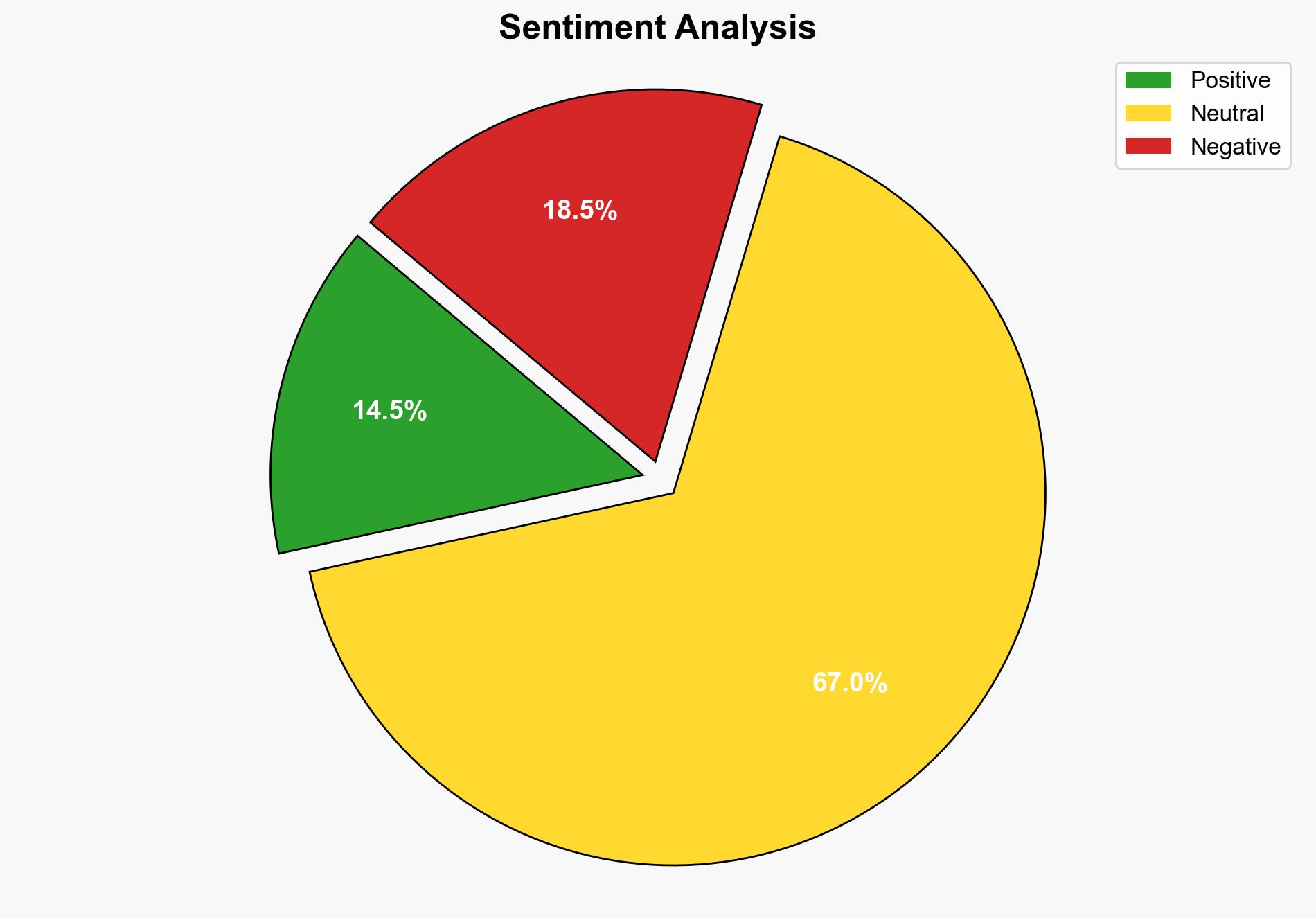
The report highlights a potential security breach involving Pete Hegseth, linked to the unauthorized sharing of sensitive information via unsecured communication channels. This incident raises significant concerns about operational security and the potential for increased vulnerability to cyber threats. Immediate actions are recommended to address these security lapses and prevent further breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
SWOT Analysis
Strengths: Utilization of encrypted messaging apps for secure communication.
Weaknesses: Potential misuse of secure channels for unauthorized information sharing.
Opportunities: Implementing stricter communication protocols and oversight mechanisms.
Threats: Increased risk of cyber attacks targeting government officials.
Cross-Impact Matrix
The interaction between unsecured communication practices and geopolitical tensions in regions like Yemen could exacerbate security risks. The potential for sensitive information leaks may influence regional stability and international relations.
Scenario Generation
Best Case: Immediate corrective measures are implemented, enhancing communication security and restoring trust.
Worst Case: Continued breaches lead to significant intelligence leaks, compromising national security.
Most Likely: Incremental improvements in security protocols with ongoing monitoring and adjustments.
3. Implications and Strategic Risks
The incident underscores vulnerabilities in communication security, highlighting the need for robust cyber defense strategies. Potential cascading effects include compromised military operations and strained diplomatic relations, particularly in conflict-prone regions.
4. Recommendations and Outlook
- Implement comprehensive training for officials on secure communication practices.
- Enhance monitoring and auditing of communication channels to detect unauthorized activities.
- Develop contingency plans to address potential information leaks swiftly.
- Scenario-based projections suggest prioritizing immediate corrective actions to mitigate risks.
5. Key Individuals and Entities
Pete Hegseth, Anna Kelly, Sean Parnell
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)