PhD candidate denied bail over alleged Australia Day terror plot following Bondi Beach shooting incident
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Australia Day terror plot foiled as PhD candidate Sepehr Saryazdi denied bail amid heightened security after Bondi terror attack
1. BLUF (Bottom Line Up Front)
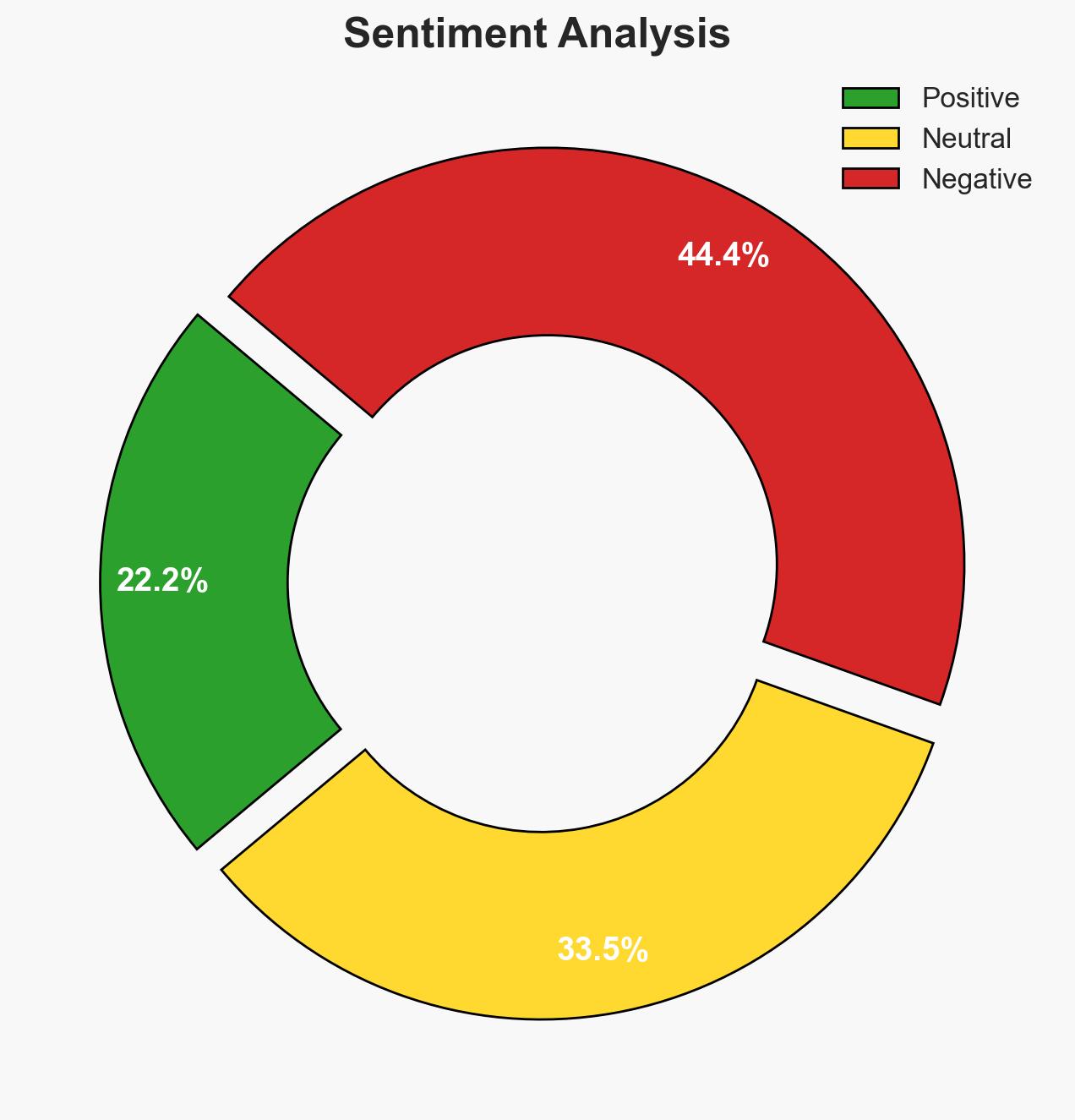
The arrest and denial of bail for Sepehr Saryazdi, accused of planning a terrorist attack on Australia Day, underscores Australia’s heightened counter-terrorism posture following the Bondi Beach attack. The situation highlights potential domestic radicalization and the need for enhanced monitoring of extremist communications. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Saryazdi was actively planning a terrorist attack inspired by extremist ideologies, as evidenced by his online communications and preparations. However, the extent of his operational capability remains uncertain.
- Hypothesis B: Saryazdi’s actions were more aspirational than operational, with limited capability or intent to execute the attack, potentially exaggerated by social isolation and influence from extremist peers.
- Assessment: Hypothesis A is currently better supported due to the concrete evidence of planning and procurement of materials. However, further intelligence on his network and capability could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: Saryazdi’s communications accurately reflect his intentions; the Bondi attack has increased the risk of copycat incidents; current intelligence on Saryazdi’s network is comprehensive.
- Information Gaps: Details on Saryazdi’s connections to broader extremist networks; his actual capability to execute the planned attack; potential external influences or handlers.
- Bias & Deception Risks: Potential over-reliance on digital communications as evidence; risk of misinterpretation of intent due to lack of context; possible exaggeration of threat by authorities to justify heightened security measures.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of domestic extremist networks and influence counter-terrorism policies. The situation may also affect public perception and trust in security measures.
- Political / Geopolitical: Potential for increased political pressure to enhance counter-terrorism legislation and resources.
- Security / Counter-Terrorism: Heightened alert and resource allocation to prevent similar plots; potential strain on intelligence and law enforcement agencies.
- Cyber / Information Space: Increased monitoring of online extremist communications; potential for cyber operations targeting extremist networks.
- Economic / Social: Possible public unrest or fear affecting social cohesion; economic implications from increased security spending.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of extremist communications; conduct thorough investigation into Saryazdi’s network; increase public awareness and reporting mechanisms.
- Medium-Term Posture (1–12 months): Develop resilience measures against domestic radicalization; strengthen partnerships with community leaders to counter extremism; invest in intelligence capabilities.
- Scenario Outlook: Best: Disruption of further plots and increased public confidence. Worst: Successful attack leading to significant casualties. Most-Likely: Continued thwarting of plots with occasional public concern.
6. Key Individuals and Entities
- Sepehr Saryazdi – Accused PhD candidate
- Sajid Akram – Deceased Bondi Beach attacker
- Naveed Akram – Injured Bondi Beach attacker
- CSIRO – Former employer of Saryazdi
- ASIO – Potential target for infiltration
7. Thematic Tags
Counter-Terrorism, domestic extremism, radicalization, intelligence operations, security posture, online communications, public safety
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us