Philippines Visit of Bondi Attack Suspects Under Investigation Amid Links to Violent Extremism
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Mysterious Philippines trip becomes focus of probe into Bondi attack suspects
1. BLUF (Bottom Line Up Front)
The investigation into the Bondi attack suspects’ trip to the Philippines is focused on potential extremist connections, with current evidence suggesting a possible link to Islamist groups in the region. The most likely hypothesis is that the trip was for reconnaissance or contact with extremist elements, although this remains unconfirmed. This assessment is made with moderate confidence, acknowledging significant information gaps and potential biases.
2. Competing Hypotheses
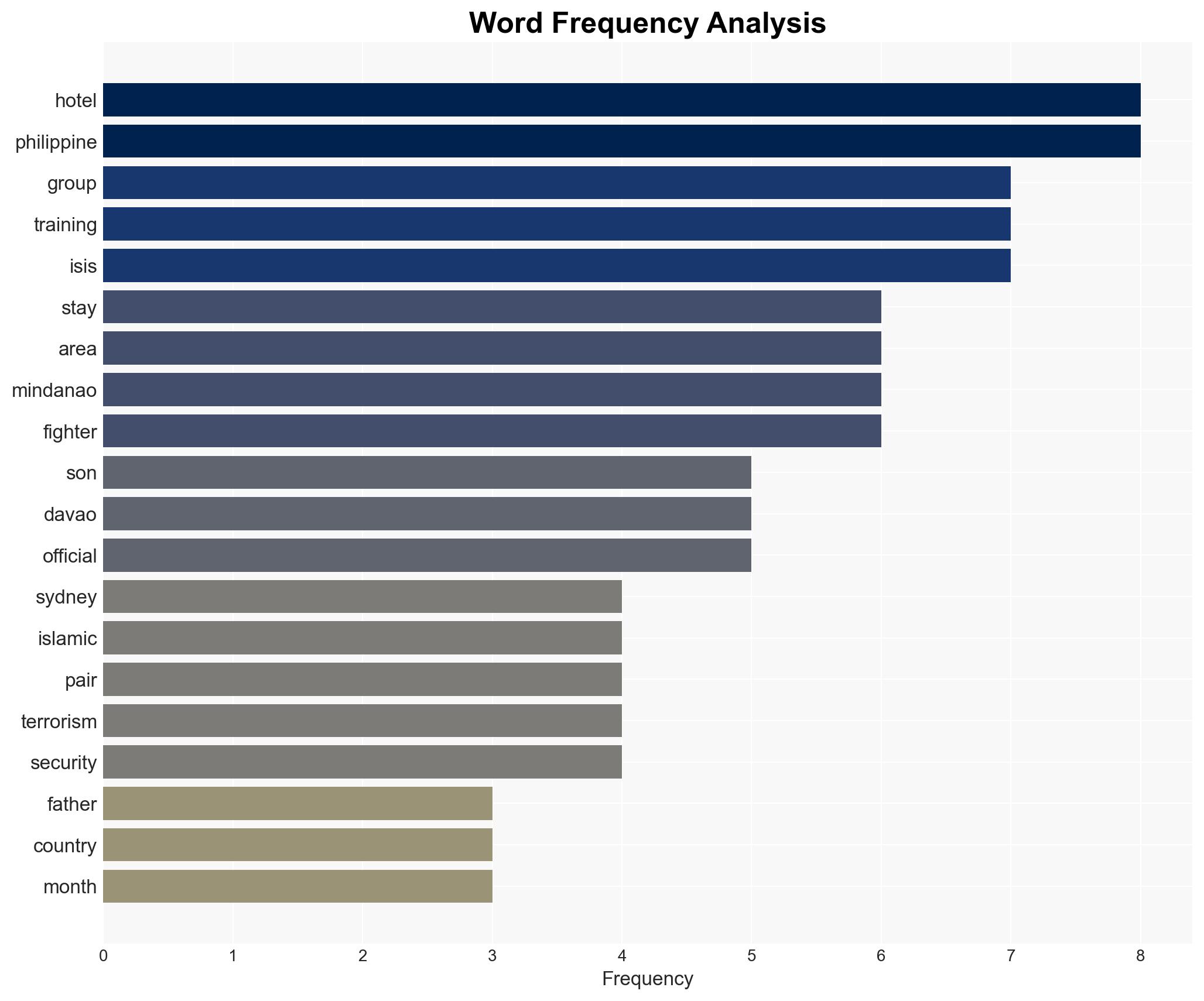
- Hypothesis A: The trip to the Philippines was intended for the suspects to receive training or establish connections with extremist groups. Supporting evidence includes the region’s history of Islamist insurgency and the suspects’ extended stay in a low-profile hotel. Contradicting evidence includes the lack of direct claims of responsibility by any group and the Philippine government’s dismissal of the training theory. Key uncertainties involve the activities and contacts of the suspects during their stay.
- Hypothesis B: The trip was unrelated to extremist activities and was instead a personal or unrelated business trip. Supporting evidence includes the lack of suspicious behavior reported by hotel staff and no security alerts triggered by their travel. However, the timing and location of the trip, along with the suspects’ history, contradict this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the strategic significance of the location and the suspects’ background. Indicators that could shift this judgment include new intelligence on their activities in Davao or credible claims by extremist groups.
3. Key Assumptions and Red Flags
- Assumptions: The suspects’ trip was strategically planned; the region still harbors active extremist elements; the suspects had prior extremist inclinations.
- Information Gaps: Detailed itinerary and contacts of the suspects in the Philippines; any communications between the suspects and extremist groups; motivations behind the trip.
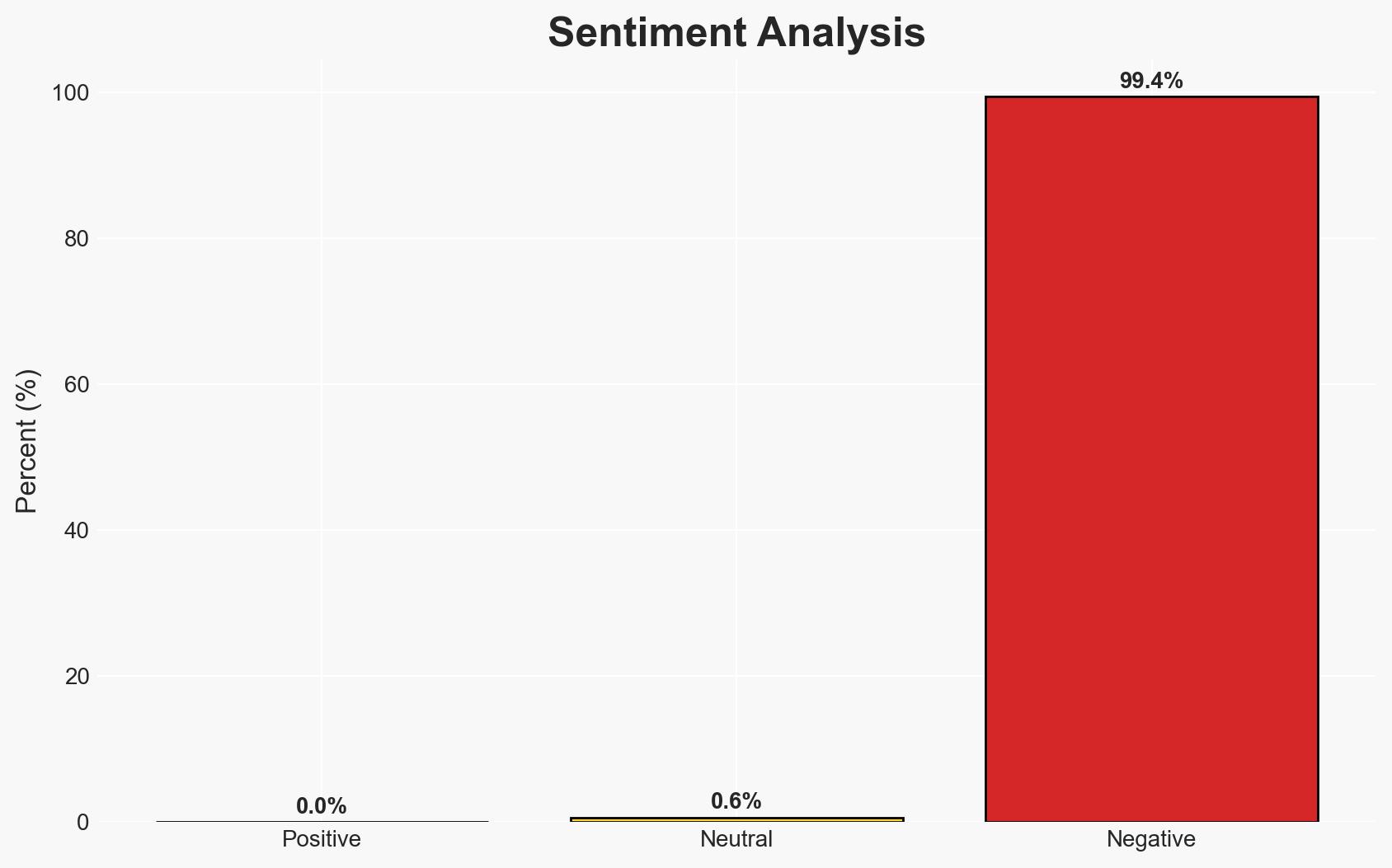
- Bias & Deception Risks: Potential bias in Philippine government statements downplaying extremist presence; reliance on hotel staff reports which may lack depth; possible misinformation from extremist groups claiming influence.
4. Implications and Strategic Risks
The investigation could influence regional security dynamics and international counter-terrorism cooperation. It may also affect perceptions of the Philippines as a safe destination.
- Political / Geopolitical: Strained relations between Australia and the Philippines if training links are confirmed; increased scrutiny on Southeast Asian counter-terrorism efforts.
- Security / Counter-Terrorism: Potential for heightened security measures in Australia and the Philippines; increased monitoring of travel to known extremist regions.
- Cyber / Information Space: Possible exploitation of the incident by extremist groups for propaganda; increased cyber monitoring for extremist communications.
- Economic / Social: Potential impact on tourism in the Philippines; heightened community tensions in Australia.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence sharing between Australia and the Philippines; conduct thorough analysis of suspects’ digital communications.
- Medium-Term Posture (1–12 months): Strengthen counter-terrorism partnerships in Southeast Asia; develop community outreach programs to counter radicalization.
- Scenario Outlook:
- Best: No extremist links are found, reducing regional tensions.
- Worst: Confirmation of training leads to increased attacks and geopolitical strain.
- Most-Likely: Partial links are identified, leading to increased security measures and regional cooperation.
6. Key Individuals and Entities
- Naveed Akram (suspect)
- Sajid Akram (suspect, deceased)
- GV Hotel (location of stay)
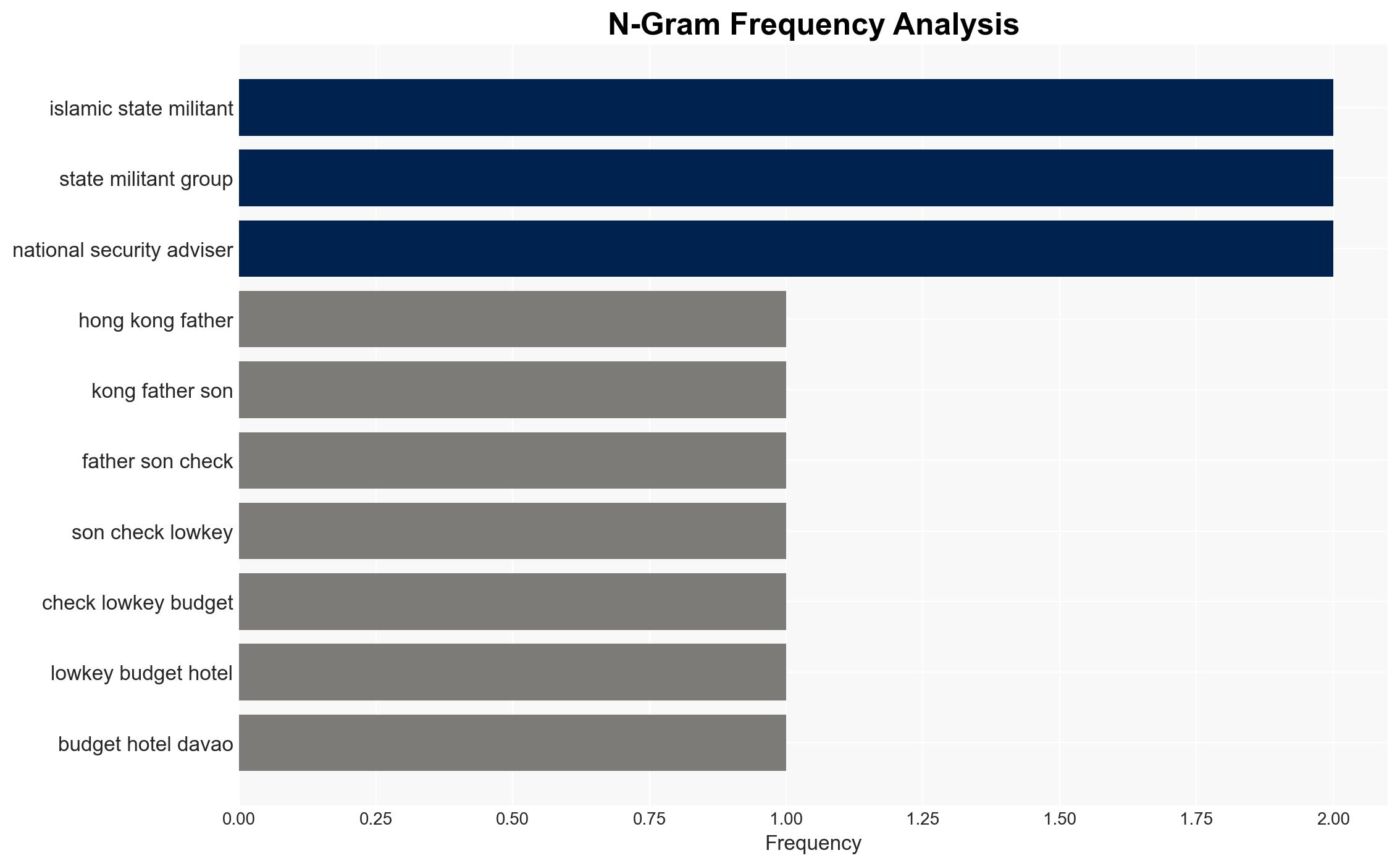
- Islamic State (alleged inspiration)
- New South Wales Police (investigating authority)
7. Thematic Tags
Counter-Terrorism, extremist networks, Southeast Asia security, intelligence sharing, radicalization, geopolitical tensions
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us