Phishing and BEC Campaign Exploits SharePoint to Target Energy Sector Organizations
Published on: 2026-01-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Energy sector targeted in multi-stage phishing and BEC campaign using SharePoint
1. BLUF (Bottom Line Up Front)
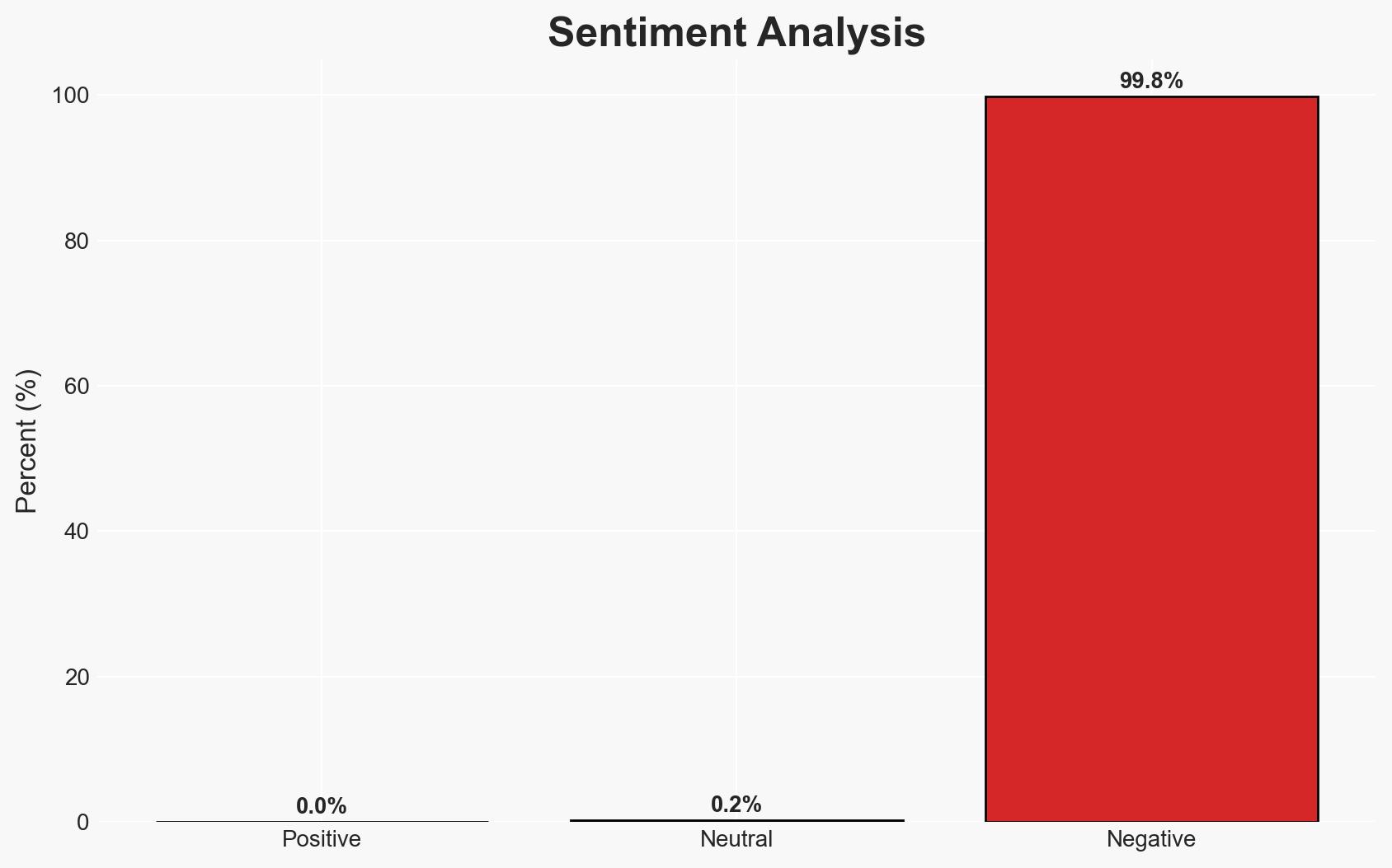
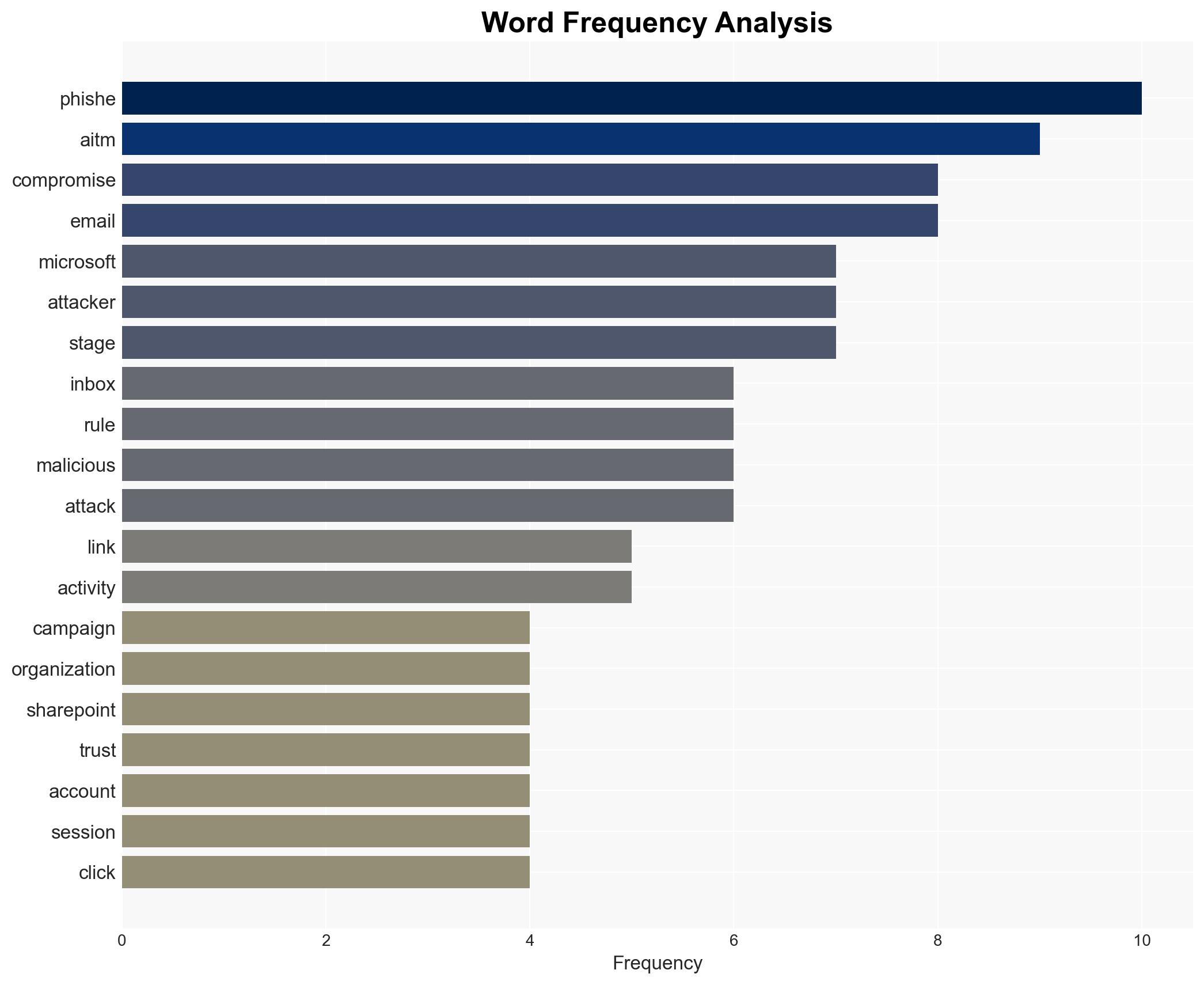
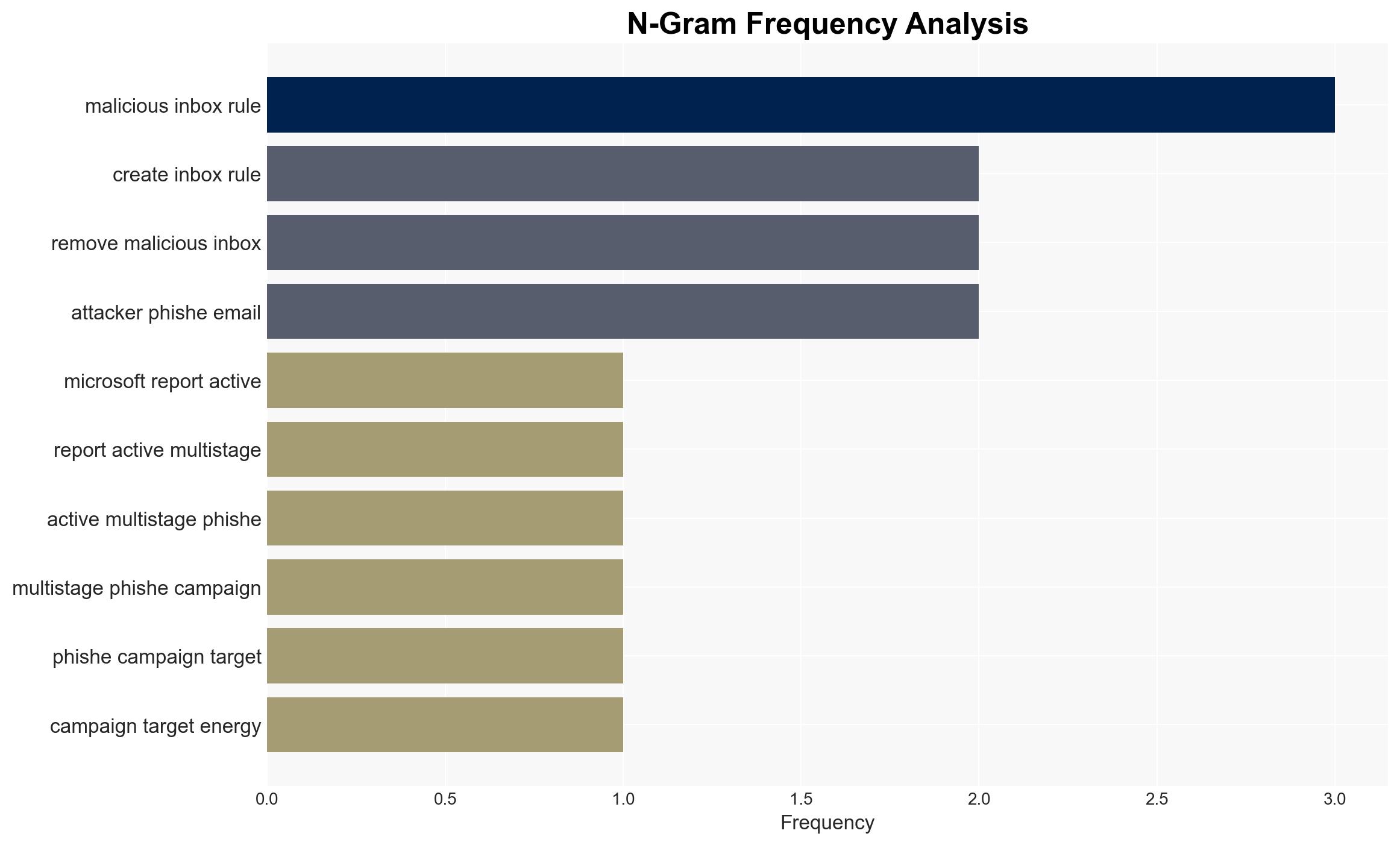
The energy sector is currently targeted by a sophisticated multi-stage phishing and business email compromise (BEC) campaign exploiting SharePoint to bypass defenses. The campaign’s complexity and persistence highlight significant vulnerabilities in current cybersecurity measures. The most likely hypothesis is that the campaign is state-sponsored, given its scale and sophistication. Overall confidence in this assessment is moderate due to limited attribution data.
2. Competing Hypotheses
- Hypothesis A: The campaign is state-sponsored, aimed at disrupting or gathering intelligence on the energy sector. This is supported by the campaign’s sophistication and scale, but lacks direct attribution evidence.
- Hypothesis B: The campaign is conducted by financially motivated cybercriminals targeting the energy sector for monetary gain. This is plausible given the BEC component, but the use of advanced techniques suggests a higher level of capability than typical criminal groups.
- Assessment: Hypothesis A is currently better supported due to the campaign’s complexity and potential strategic implications. Indicators such as direct attribution or geopolitical context could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The energy sector is a high-value target for state actors; the use of SharePoint is intentional to exploit trust in cloud services; the attackers have advanced capabilities.
- Information Gaps: Lack of direct attribution to a specific actor or state; insufficient data on the full scope of compromised entities.
- Bias & Deception Risks: Potential confirmation bias towards state-sponsored attribution; reliance on Microsoft as a single source may introduce bias.
4. Implications and Strategic Risks
This development could lead to increased targeting of critical infrastructure sectors and necessitate enhanced cybersecurity measures. The campaign’s persistence suggests potential for further escalation.
- Political / Geopolitical: Potential for increased tensions if linked to state actors; could influence energy policy and international relations.
- Security / Counter-Terrorism: Highlights vulnerabilities in critical infrastructure; may prompt increased security measures and collaboration.
- Cyber / Information Space: Demonstrates evolving threat landscape; could lead to increased investment in cybersecurity defenses and policies.
- Economic / Social: Potential economic impact if energy supply is disrupted; could affect public trust in digital communications.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of energy sector networks; implement advanced anti-phishing measures; conduct awareness training for employees.
- Medium-Term Posture (1–12 months): Develop resilience strategies; strengthen public-private partnerships; invest in cybersecurity infrastructure.
- Scenario Outlook:
- Best: Enhanced defenses prevent further breaches, and attribution leads to diplomatic resolution.
- Worst: Successful attacks lead to significant disruptions in energy supply and geopolitical tensions.
- Most-Likely: Continued attempts with varying success, prompting gradual improvements in cybersecurity posture.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, energy sector, phishing, business email compromise, state-sponsored threats, critical infrastructure, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us