Phishing emails delivering infostealers surge 84 – Help Net Security
Published on: 2025-04-23
Intelligence Report: Phishing Emails Delivering Infostealers Surge 84 – Help Net Security
1. BLUF (Bottom Line Up Front)
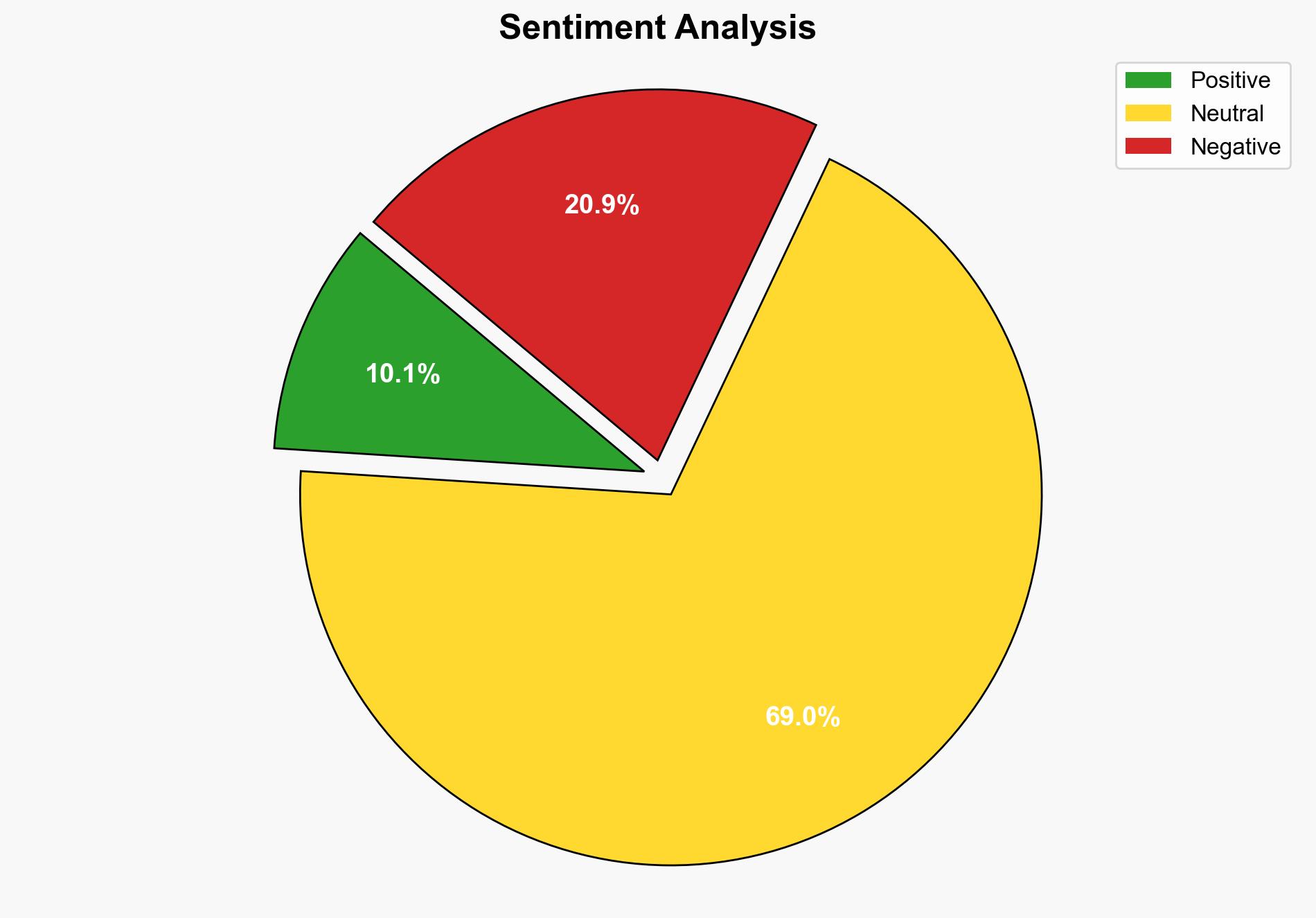
Recent analysis indicates a significant 84% surge in phishing emails delivering infostealers, highlighting a strategic shift by cybercriminals towards stealthy credential theft tactics. This trend coincides with a decline in ransomware attacks, suggesting an adaptation to increased law enforcement pressure and advanced detection technologies. Key recommendations include enhancing authentication management and real-time threat hunting to mitigate these evolving threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The evidence suggests that cybercriminals are prioritizing infostealers over ransomware due to their ability to quickly exfiltrate data with minimal forensic traces. This hypothesis is supported by the observed increase in phishing campaigns and the decline in ransomware incidents.
SWOT Analysis
Strengths: Improved detection technologies and increased law enforcement collaboration.
Weaknesses: Reliance on legacy systems and slow patching cycles.
Opportunities: Modernizing authentication management and proactive threat hunting.
Threats: Sophisticated phishing campaigns leveraging AI and dark web marketplaces for infostealers.
Indicators Development
Key indicators include increased phishing campaigns, lateral movement within networks, and the emergence of new infostealer variants. Monitoring these signs can help detect ongoing or emerging threats.
3. Implications and Strategic Risks
The shift towards infostealers poses a significant risk to critical infrastructure, as cybercriminals exploit vulnerabilities in hybrid cloud environments. This trend could lead to increased identity theft and unauthorized access, with potential cascading effects on national security and economic stability.
4. Recommendations and Outlook
- Enhance authentication management systems and plug multi-factor authentication gaps.
- Conduct regular real-time threat hunting to uncover hidden threats.
- Scenario-based projections:
- Best Case: Rapid adaptation to new threats reduces successful phishing incidents.
- Worst Case: Continued reliance on legacy systems leads to widespread data breaches.
- Most Likely: Incremental improvements in cyber defenses mitigate some risks but do not eliminate them.
5. Key Individuals and Entities
Mark Hughes is noted for his insights into the need for proactive cybersecurity measures.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)