Pink Ranger hacktivist disrupts white supremacist sites live at German conference, sparking online applause
Published on: 2026-01-07
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pink Ranger hacktivist wiped white supremacist dating site live on stage at a German conference Hacking for good
1. BLUF (Bottom Line Up Front)
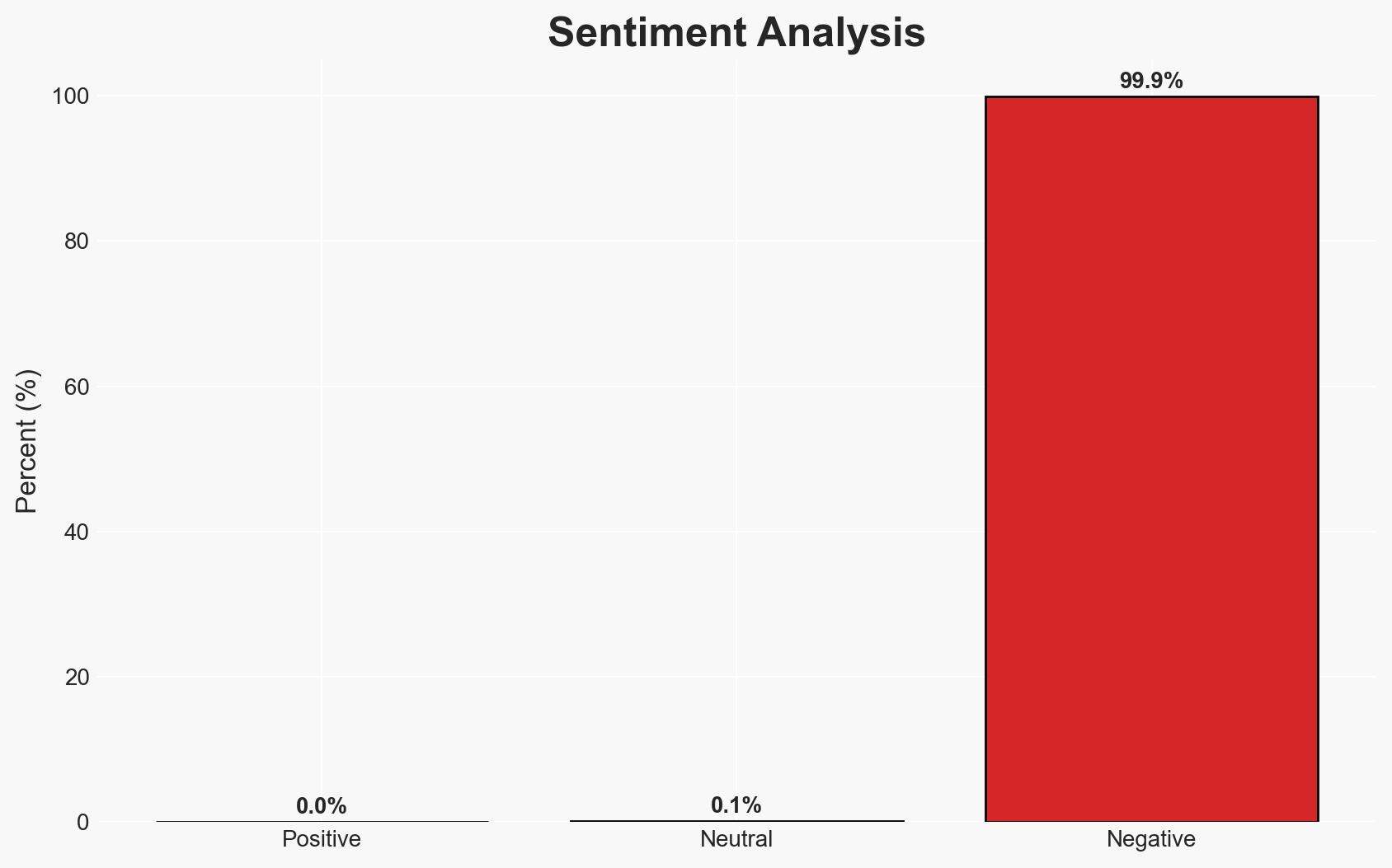
The hacktivist action by “Martha Root” against white supremacist websites at the Chaos Communication Congress in Germany highlights vulnerabilities in extremist digital infrastructure and the potential for hacktivism to disrupt such networks. The event has been widely praised online, indicating a positive public perception of hacktivism when targeting hate groups. Overall, I assess with moderate confidence that this incident may inspire similar actions against extremist platforms, potentially escalating tensions between hacktivists and extremist groups.
2. Competing Hypotheses
- Hypothesis A: The hacktivist action was a spontaneous act of protest against white supremacist ideologies, primarily aimed at raising awareness and disrupting extremist activities. Supporting evidence includes the public nature of the hack and the lack of sophisticated cybersecurity defenses on the targeted sites. Key uncertainties include the extent of premeditation and coordination with other actors.
- Hypothesis B: The hack was part of a coordinated campaign by a broader network of hacktivists targeting white supremacist groups, with potential links to organized anti-racist movements. This is supported by the strategic timing and public execution of the hack. Contradicting evidence includes the lack of explicit claims of affiliation with larger networks.
- Assessment: Hypothesis A is currently better supported due to the lack of evidence indicating broader coordination. However, indicators such as subsequent similar attacks or claims of responsibility by known hacktivist groups could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The hacktivist acted independently; the targeted websites had minimal cybersecurity defenses; public sentiment generally supports actions against hate groups.
- Information Gaps: Details on any potential coordination with other hacktivists; the full extent of data compromised; the response strategy of the affected websites.
- Bias & Deception Risks: Potential bias in public reporting favoring the hacktivist; the possibility of exaggerated claims by the hacktivist to enhance perceived impact.
4. Implications and Strategic Risks
This development could embolden other hacktivists to target extremist groups, potentially leading to an escalation in cyber confrontations. It may also prompt extremist groups to improve their cybersecurity measures.
- Political / Geopolitical: Increased tensions between extremist groups and anti-racist movements; potential for international attention on Germany’s handling of extremist digital platforms.
- Security / Counter-Terrorism: Potential retaliatory actions by extremist groups; increased focus on securing digital infrastructure of hate groups.
- Cyber / Information Space: Highlighted vulnerabilities in extremist websites; potential for increased hacktivist activities targeting similar platforms.
- Economic / Social: Possible social polarization due to differing views on hacktivism; minimal direct economic impact expected.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor extremist online platforms for retaliatory actions; engage with cybersecurity experts to assess vulnerabilities in similar sites.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to enhance monitoring of extremist content; invest in public awareness campaigns on cybersecurity hygiene.
- Scenario Outlook:
- Best Case: Increased cybersecurity measures deter future hacktivist actions without significant escalation.
- Worst Case: Retaliatory cyberattacks by extremist groups lead to broader cyber conflicts.
- Most Likely: Continued sporadic hacktivist actions against poorly secured extremist sites, with gradual improvements in cybersecurity by targeted groups.
6. Key Individuals and Entities
- Martha Root (hacktivist pseudonym)
- Eva Hoffmann (journalist)
- Christian Fuchs (journalist)
- WhiteDate (targeted website)
- WhiteChild (targeted website)
- WhiteDeal (targeted website)
7. Thematic Tags
cybersecurity, hacktivism, white supremacy, extremist groups, digital protest, cyber operations, public sentiment
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us