PlushDaemon compromises network devices for adversary-in-the-middle attacks – We Live Security
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
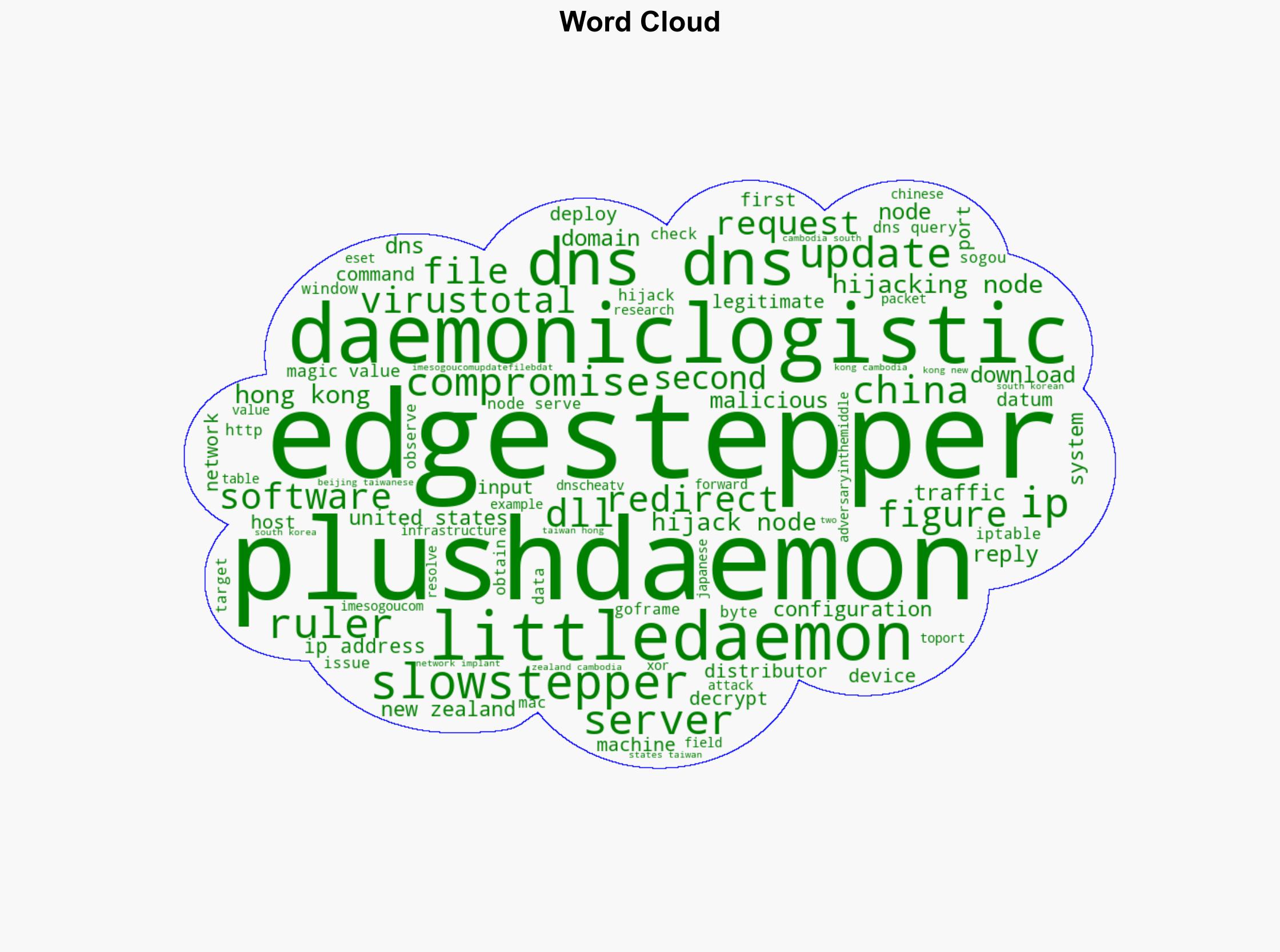
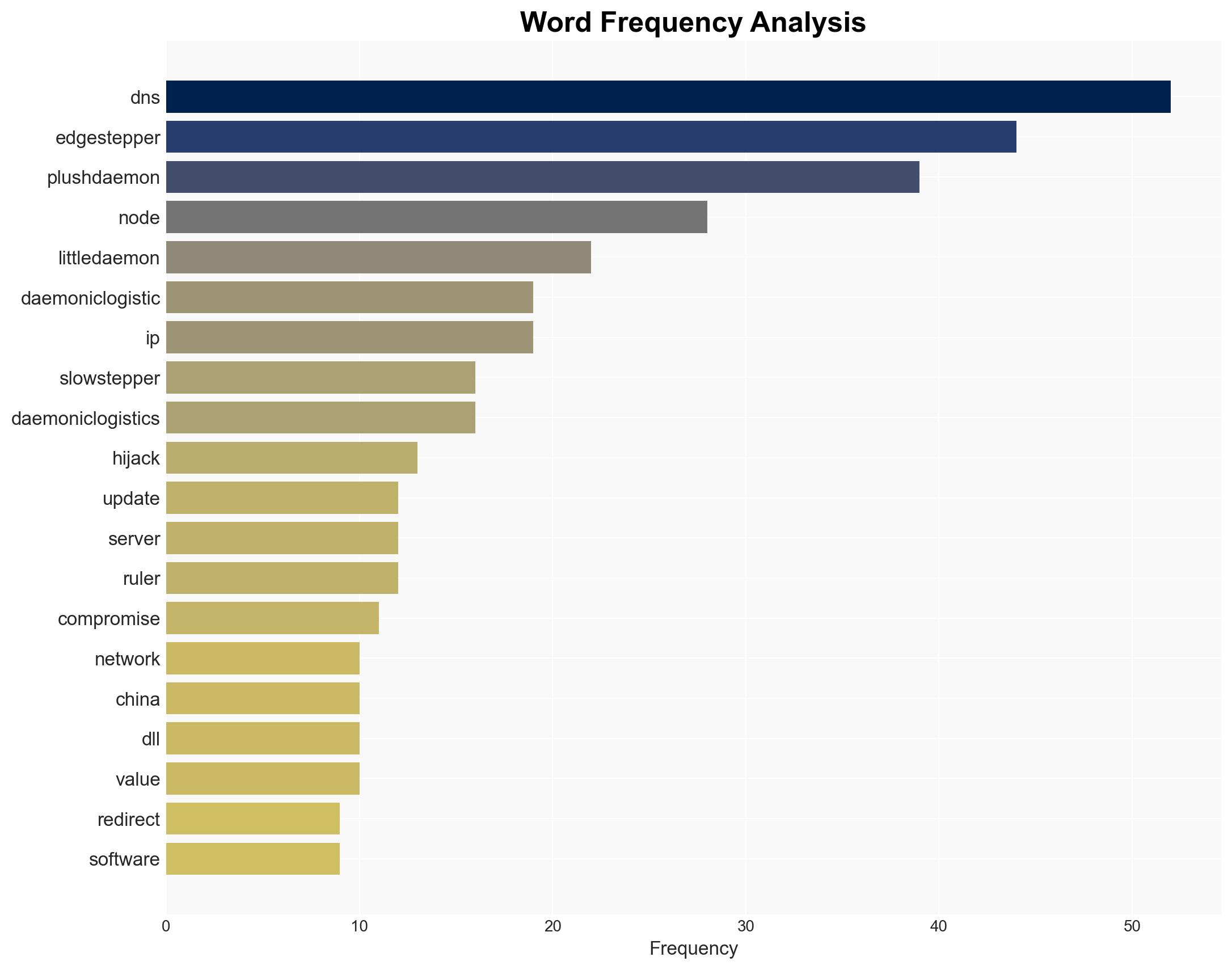
With a moderate confidence level, it is assessed that PlushDaemon, a China-aligned threat actor, is conducting adversary-in-the-middle attacks using a network implant named EdgeStepper to compromise network devices. The most supported hypothesis is that these activities are part of a broader espionage campaign targeting geopolitical adversaries and sectors of strategic interest. It is recommended that organizations enhance their network security protocols, particularly focusing on DNS security and software update integrity.
2. Competing Hypotheses
Hypothesis 1: PlushDaemon is primarily conducting espionage operations targeting geopolitical adversaries and sectors of strategic interest for China, such as technology and manufacturing.
Hypothesis 2: PlushDaemon is engaged in a broader cybercrime campaign, exploiting vulnerabilities for financial gain through ransom or data theft.
Hypothesis 1 is more likely due to the geographical distribution of targets, including universities and manufacturing sectors in regions of strategic interest to China. The use of sophisticated techniques like adversary-in-the-middle attacks and the targeting of software updates suggest a focus on long-term intelligence gathering rather than immediate financial gain.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the attribution to China-aligned actors is accurate based on the telemetry and the nature of the targets. It is also assumed that the observed activities are representative of a broader campaign.
Red Flags: The possibility of misattribution due to false flags or the involvement of multiple threat actors cannot be ruled out. The presence of compromised infrastructure and open directories could indicate deliberate deception to mislead investigators.
4. Implications and Strategic Risks
The implications of PlushDaemon’s activities include potential disruptions in critical sectors such as manufacturing and technology, particularly in regions like Taiwan and South Korea. Escalation scenarios could involve retaliatory cyber operations or increased geopolitical tensions, especially if state-sponsored involvement is confirmed. Economically, compromised supply chains could lead to significant financial losses and reputational damage for affected companies.
5. Recommendations and Outlook
- Enhance DNS security measures and monitor for unusual DNS query patterns.
- Implement strict controls over software update processes to prevent hijacking.
- Conduct regular security audits and vulnerability assessments on network devices.
- Best-case scenario: Organizations successfully mitigate risks, and geopolitical tensions remain stable.
- Worst-case scenario: Escalation leads to significant geopolitical conflict and widespread economic impact.
- Most-likely scenario: Continued cyber espionage activities with sporadic disruptions in targeted sectors.
6. Key Individuals and Entities
No specific individuals are named in the report. Key entities include PlushDaemon, EdgeStepper, and targeted organizations in the United States, Taiwan, China, Hong Kong, New Zealand, and Cambodia.
7. Thematic Tags
Cybersecurity, Espionage, Geopolitical Tensions, Supply Chain Security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us