PoC exploit for critical ErlangOTP SSH bug is public CVE-2025-32433 – Help Net Security
Published on: 2025-04-22
Intelligence Report: PoC exploit for critical ErlangOTP SSH bug is public CVE-2025-32433 – Help Net Security
1. BLUF (Bottom Line Up Front)
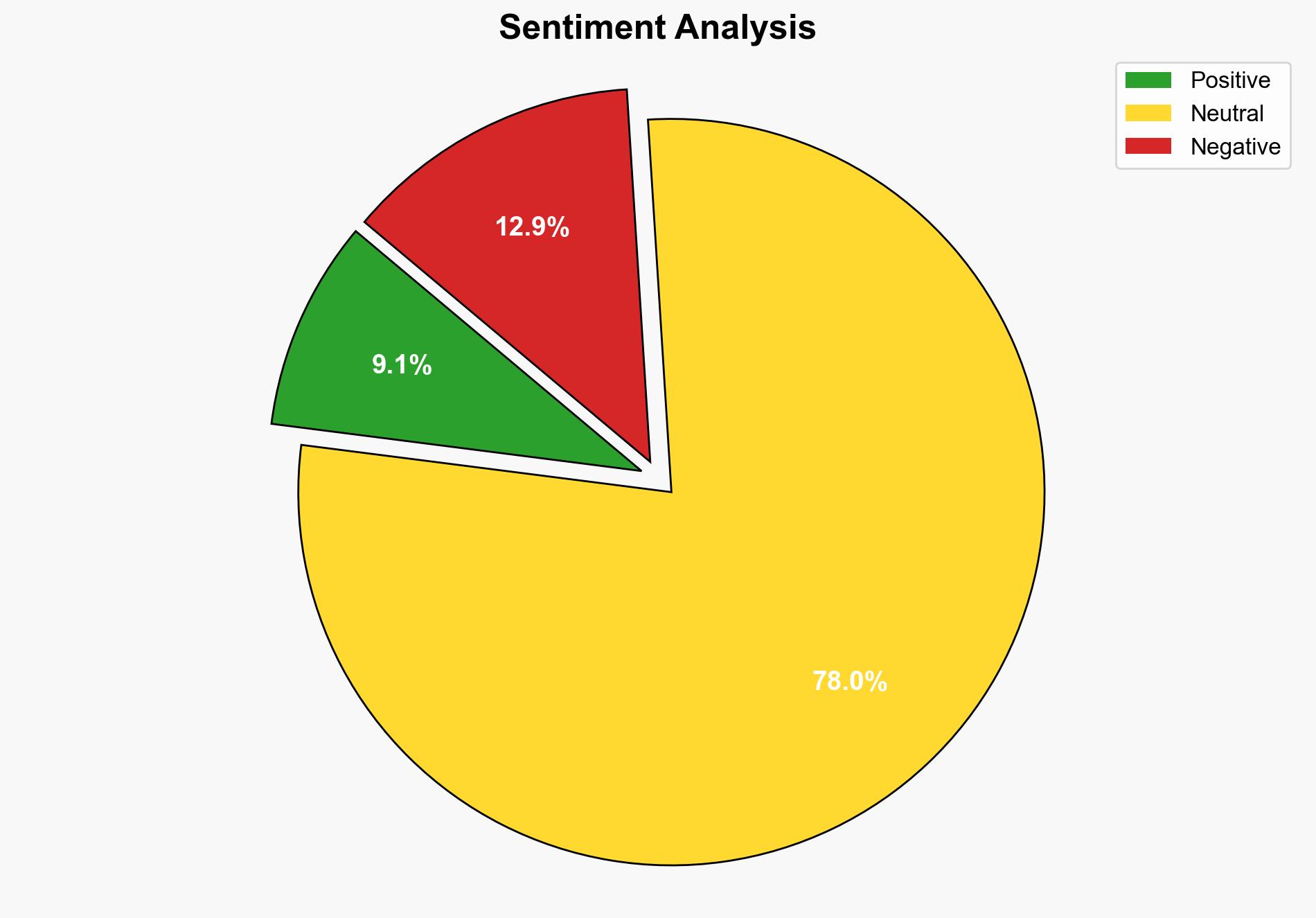
A proof-of-concept (PoC) exploit for a critical vulnerability in the ErlangOTP SSH library, identified as CVE-2025-32433, has been made public. This vulnerability allows unauthenticated attackers to execute arbitrary code on affected systems, posing significant security risks, especially for IoT devices and telecommunications platforms. Immediate patching and mitigation measures are recommended to prevent potential exploitation.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that the public release of the PoC exploit increases the likelihood of widespread attacks. Alternative hypotheses include the possibility of limited exploitation due to rapid patch deployment or inherent system protections.
SWOT Analysis
Strengths: Availability of a patch and security updates from ErlangOTP.
Weaknesses: Potential delay in patch application across all affected systems.
Opportunities: Enhancing cybersecurity protocols and awareness.
Threats: Increased risk of unauthorized access and data breaches.
Indicators Development
Monitor for unusual network activity, unauthorized access attempts, and any signs of lateral movement within networks. Pay attention to phishing campaigns that may exploit this vulnerability.
3. Implications and Strategic Risks
The public availability of the PoC exploit could lead to a surge in cyberattacks targeting vulnerable systems. This poses risks not only to individual organizations but also to critical infrastructure sectors reliant on ErlangOTP. The vulnerability could facilitate unauthorized access, data manipulation, and denial-of-service attacks, with potential cascading effects on economic and national security.
4. Recommendations and Outlook
- Immediately apply the latest security patches provided by ErlangOTP to all affected systems.
- Implement network segmentation and strict access controls to limit potential exploitation.
- Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
- Scenario-based projections:
- Best Case: Rapid patch deployment minimizes exploitation incidents.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most Likely: Moderate exploitation with localized impacts, mitigated by timely patching efforts.
5. Key Individuals and Entities
Fabian Bumer, a researcher involved in the discovery of the vulnerability, has provided insights into its implications and mitigation strategies.
6. Thematic Tags
(‘cybersecurity’, ‘vulnerability management’, ‘IoT security’, ‘telecommunications security’)