PoisonSeed campaign hijacks business CRM and email accounts to send out huge amounts of spam – TechRadar
Published on: 2025-04-07
Intelligence Report: PoisonSeed Campaign Hijacks Business CRM and Email Accounts to Send Out Huge Amounts of Spam – TechRadar
1. BLUF (Bottom Line Up Front)
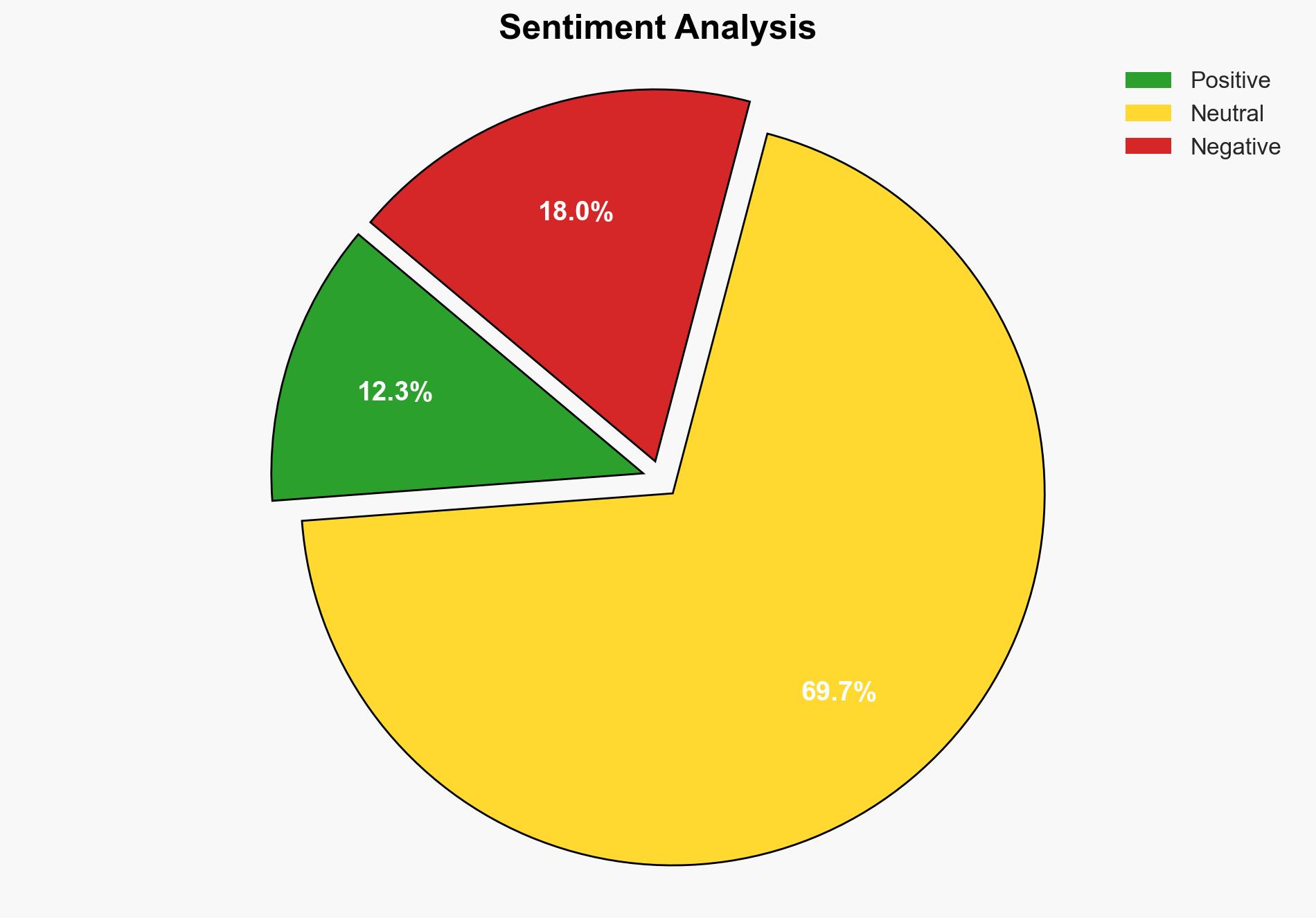
The PoisonSeed campaign has compromised business CRM and email accounts to distribute spam and steal cryptocurrency. This operation involves spoofing landing pages of major companies to harvest login credentials, enabling cybercriminals to impersonate legitimate entities. The campaign poses significant threats to financial security and organizational integrity, necessitating immediate countermeasures and heightened cybersecurity awareness.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
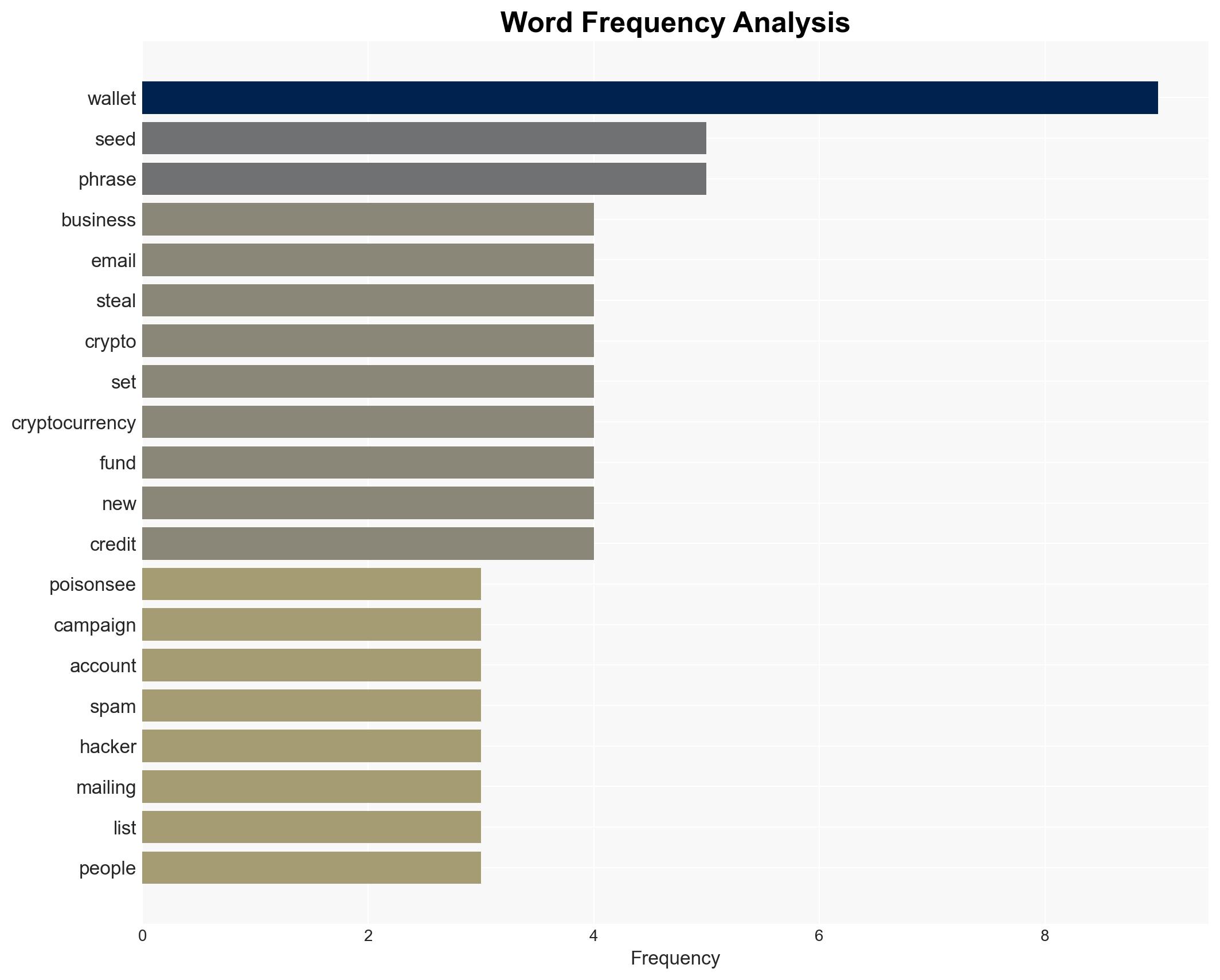
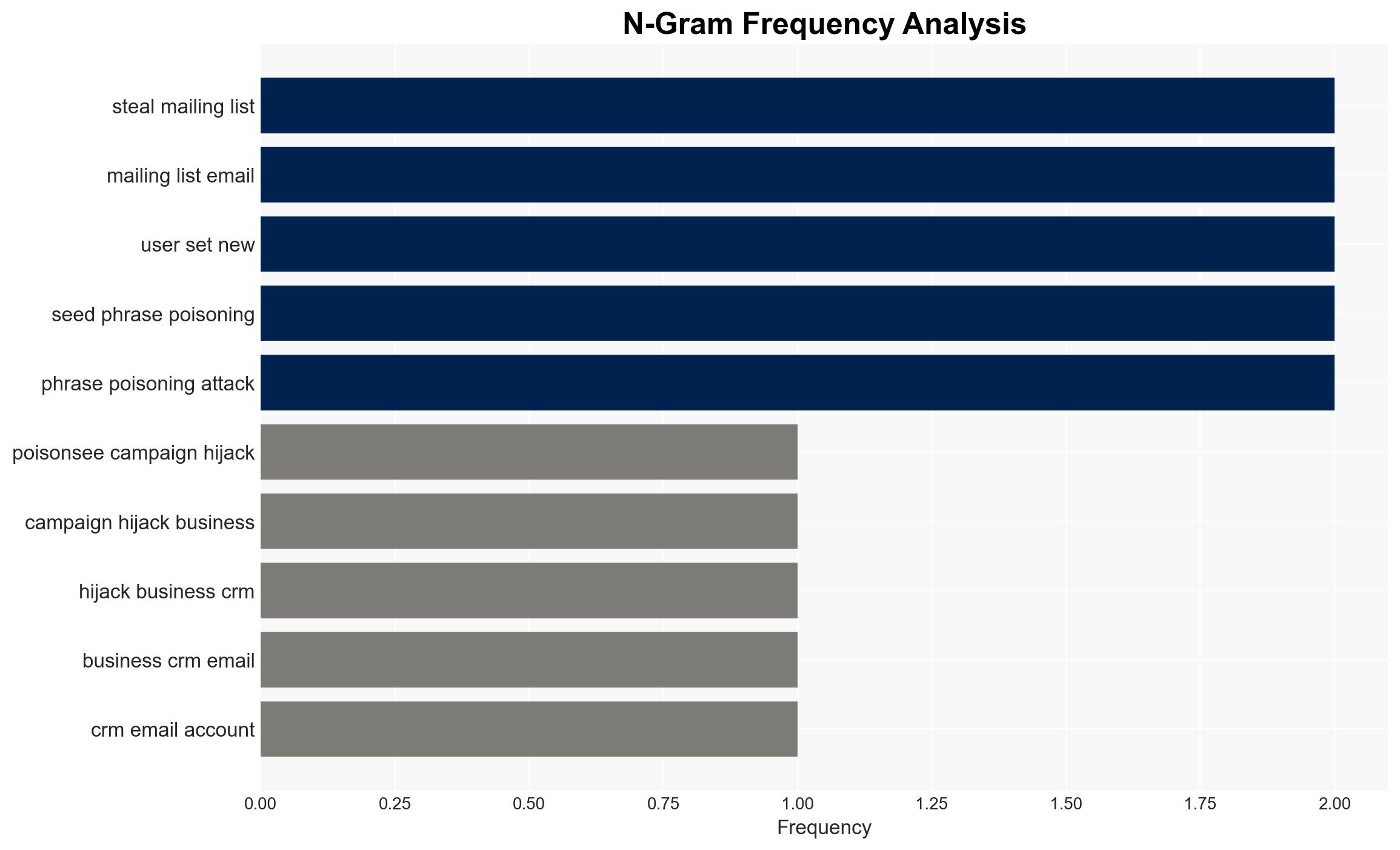
The PoisonSeed campaign primarily targets business CRM accounts to access mailing lists and distribute spam emails. These emails are crafted to trick recipients into compromising their cryptocurrency wallets by embedding seed phrases. The campaign exploits the trust associated with companies like Coinbase, Ledger, Mailchimp, SendGrid, and HubSpot. By harvesting login credentials, attackers gain unauthorized access to email services, enabling further dissemination of spam and phishing attacks. The ultimate goal is to steal funds from victims’ cryptocurrency wallets, resulting in permanent financial loss.
3. Implications and Strategic Risks
The PoisonSeed campaign presents several strategic risks:
- Increased vulnerability of businesses to cyberattacks, leading to potential financial losses and reputational damage.
- Heightened risk to individuals’ financial security due to compromised cryptocurrency wallets.
- Potential for widespread economic disruption if major companies’ CRM systems are persistently targeted.
- Threat to national security through the exploitation of digital financial systems and potential funding of illicit activities.
4. Recommendations and Outlook
Recommendations:
- Implement robust cybersecurity measures, including multi-factor authentication and regular security audits.
- Enhance employee training on recognizing phishing attempts and securing sensitive information.
- Encourage regulatory bodies to develop stricter guidelines for digital financial security and data protection.
- Invest in advanced threat detection technologies to identify and mitigate cyber threats in real-time.
Outlook:
Best-case scenario: Enhanced cybersecurity measures and regulatory frameworks significantly reduce the impact of similar campaigns, safeguarding financial systems and organizational integrity.
Worst-case scenario: Failure to address vulnerabilities leads to widespread financial losses and undermines trust in digital financial systems, with potential ripple effects on global markets.
Most likely outcome: Incremental improvements in cybersecurity practices and awareness mitigate some risks, but persistent threats continue to challenge digital security.
5. Key Individuals and Entities
The report mentions significant individuals and organizations involved in or affected by the campaign:
- Silent Push – Cybersecurity researchers who reported on the campaign.
- Scatter Spider – Alleged threat actor associated with the campaign.
- Cryptochameleon – Reportedly part of a broader cybercrime ecosystem.
- Sead – Journalist who reported on related cybersecurity issues.