Poland Successfully Defends Against Major Cyberattack Targeting Energy Infrastructure
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Poland Thwarts Russian Wiper Malware Attack on Power Plants
1. BLUF (Bottom Line Up Front)
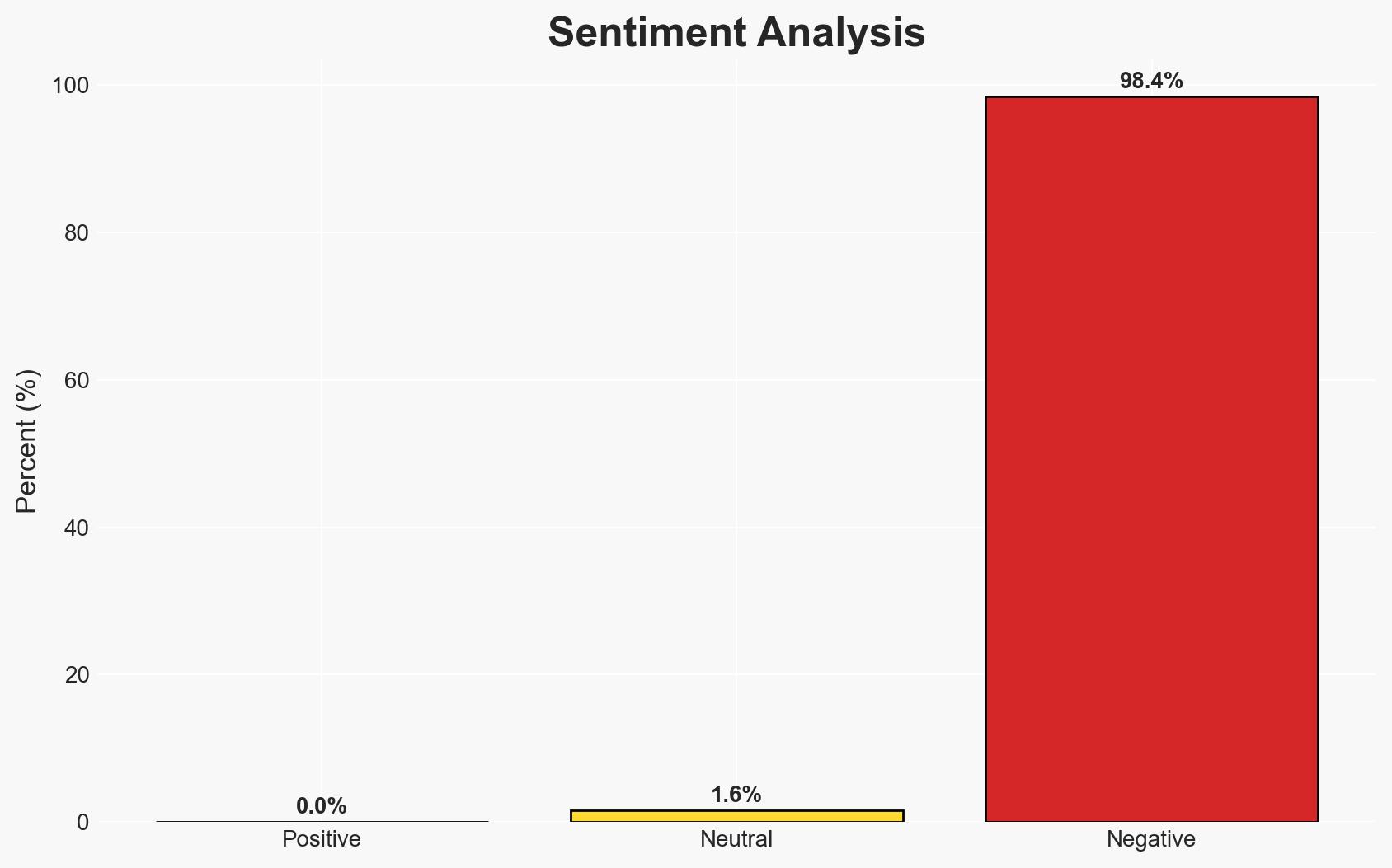
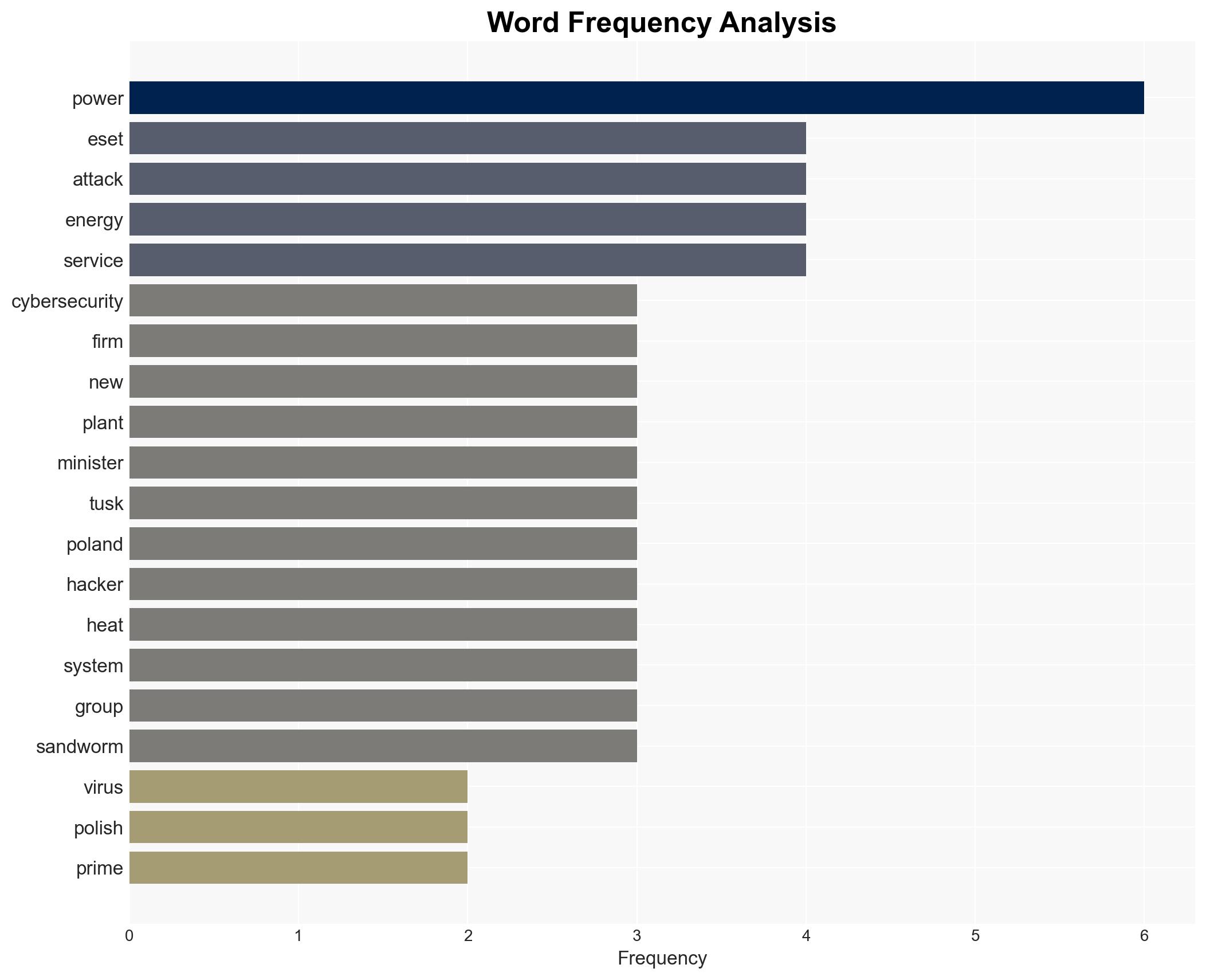
Poland successfully thwarted a significant cyberattack on its power infrastructure, attributed to the Russian hacking group Sandworm. The attack aimed to deploy a new wiper malware, DynoWiper, but was neutralized without disrupting power supply. This incident underscores the persistent threat posed by Russian cyber operations against European critical infrastructure. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was a deliberate Russian state-sponsored operation aimed at destabilizing Poland’s energy infrastructure. Supporting evidence includes the attribution to Sandworm, a group linked to the GRU, and the sophisticated nature of the malware. However, the lack of direct evidence linking the Russian state to the specific attack remains a key uncertainty.
- Hypothesis B: The attack was conducted by a non-state actor or rogue elements within Sandworm, seeking to test new malware capabilities. While this is less supported by current evidence, the possibility cannot be entirely ruled out due to the absence of concrete state directives.
- Assessment: Hypothesis A is currently better supported due to the historical pattern of Sandworm’s operations aligning with Russian geopolitical interests. Indicators that could shift this judgment include new intelligence on command structures or communications confirming state involvement.
3. Key Assumptions and Red Flags
- Assumptions: The GRU maintains operational control over Sandworm; Polish cybersecurity defenses are robust enough to detect and mitigate advanced threats; Russian cyber operations are likely to continue targeting European infrastructure.
- Information Gaps: Specific technical details of the malware’s deployment and any potential insider facilitation; comprehensive attribution evidence linking the attack directly to Russian state directives.
- Bias & Deception Risks: Attribution bias due to historical patterns of Russian cyber aggression; potential misinformation from involved cybersecurity firms or state actors to influence public perception.
4. Implications and Strategic Risks
This development highlights the ongoing cyber threat to European critical infrastructure and may prompt increased cybersecurity measures across the region. The incident could also exacerbate tensions between NATO and Russia.
- Political / Geopolitical: Potential for increased diplomatic friction between Poland and Russia, with possible NATO involvement in response strategies.
- Security / Counter-Terrorism: Heightened alert levels for critical infrastructure, necessitating enhanced security protocols and intelligence sharing.
- Cyber / Information Space: Likely acceleration of cybersecurity legislation and investment in defensive capabilities within Poland and possibly the EU.
- Economic / Social: Potential economic impact from increased cybersecurity spending; public concern over energy security could influence domestic policy debates.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; engage in diplomatic channels to address the cyber threat; increase public awareness and preparedness for potential future incidents.
- Medium-Term Posture (1–12 months): Develop resilience measures, including cross-sector cybersecurity training; strengthen international partnerships for intelligence sharing; invest in advanced detection and response technologies.
- Scenario Outlook:
- Best: Strengthened defenses deter future attacks, leading to improved regional stability.
- Worst: Successful future attacks lead to significant infrastructure disruption and geopolitical escalation.
- Most-Likely: Continued cyber probing with incremental improvements in defensive measures and international cooperation.
6. Key Individuals and Entities
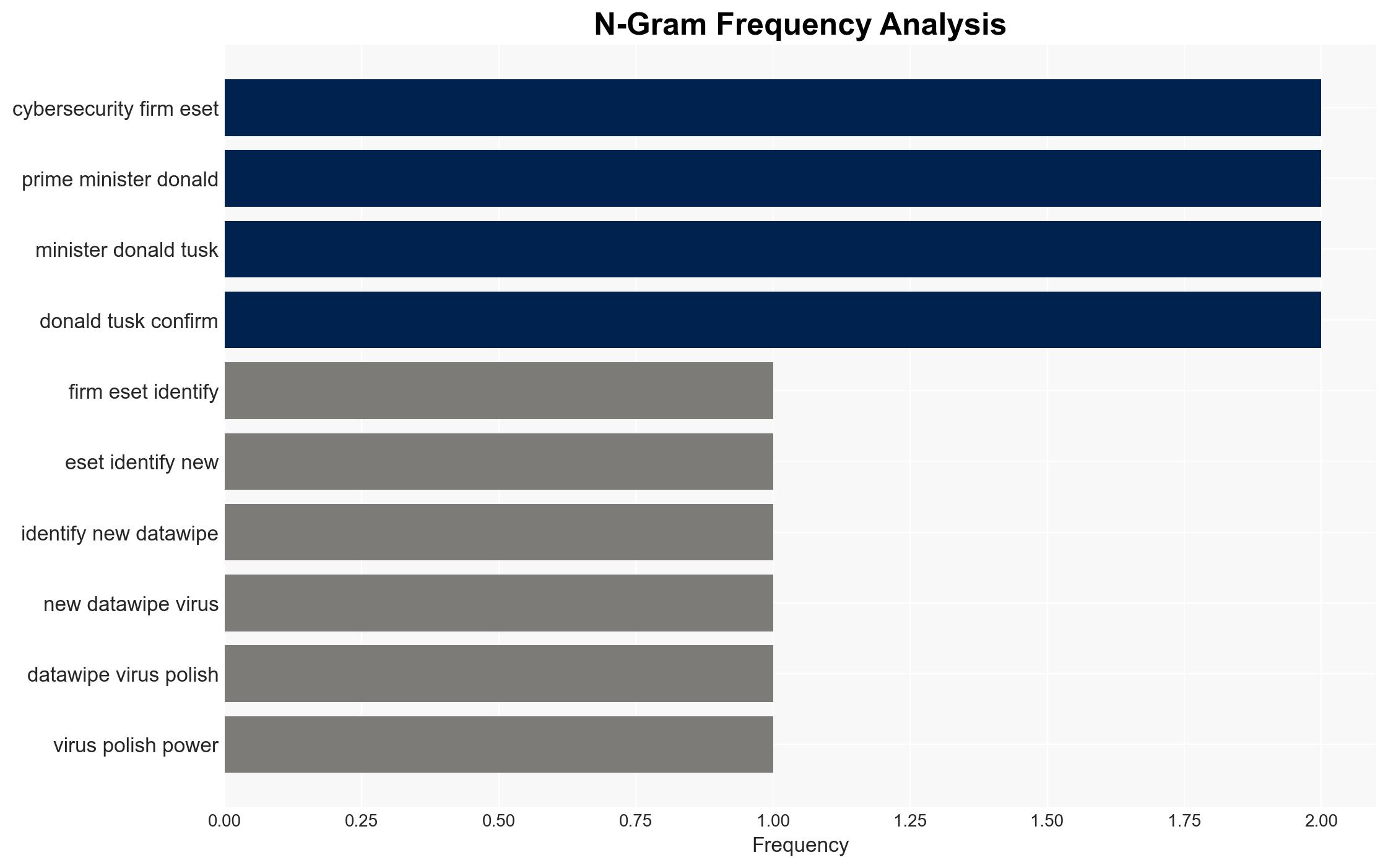
- Prime Minister Donald Tusk
- Robert Lipovsky, ESET Lead Researcher
- Sandworm (APT44, Seashell Blizzard)
- GRU (Main Intelligence Directorate, Unit 74455)
7. Thematic Tags
cybersecurity, energy security, Russian cyber operations, critical infrastructure, Poland, GRU, Sandworm
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us