Poland’s CERT Reports Coordinated Cyber Attacks on Over 30 Renewable Energy Facilities Linked to Russian Thre…
Published on: 2026-01-31
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CERT Polska Details Coordinated Cyber Attacks on 30 Wind and Solar Farms
1. BLUF (Bottom Line Up Front)
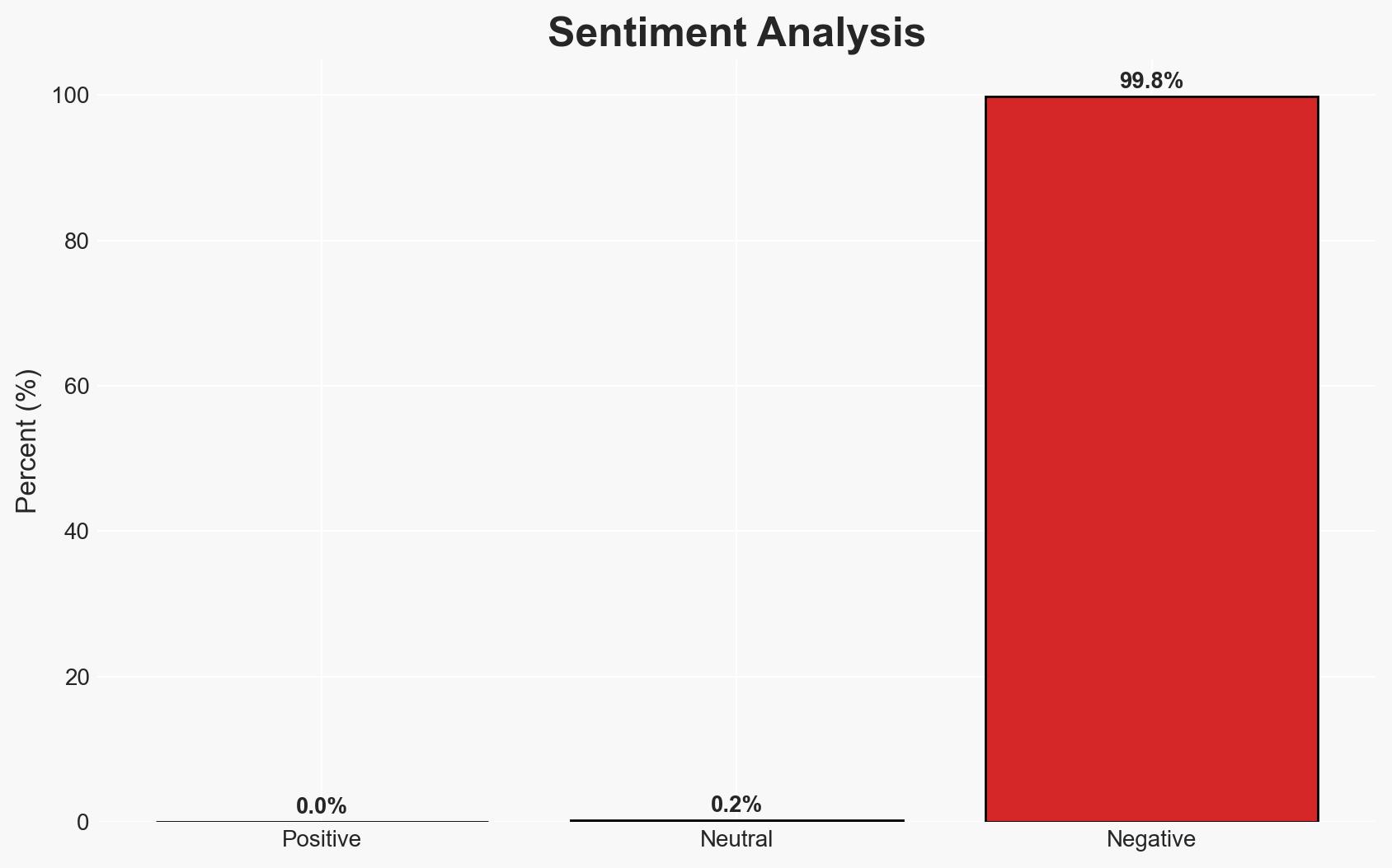
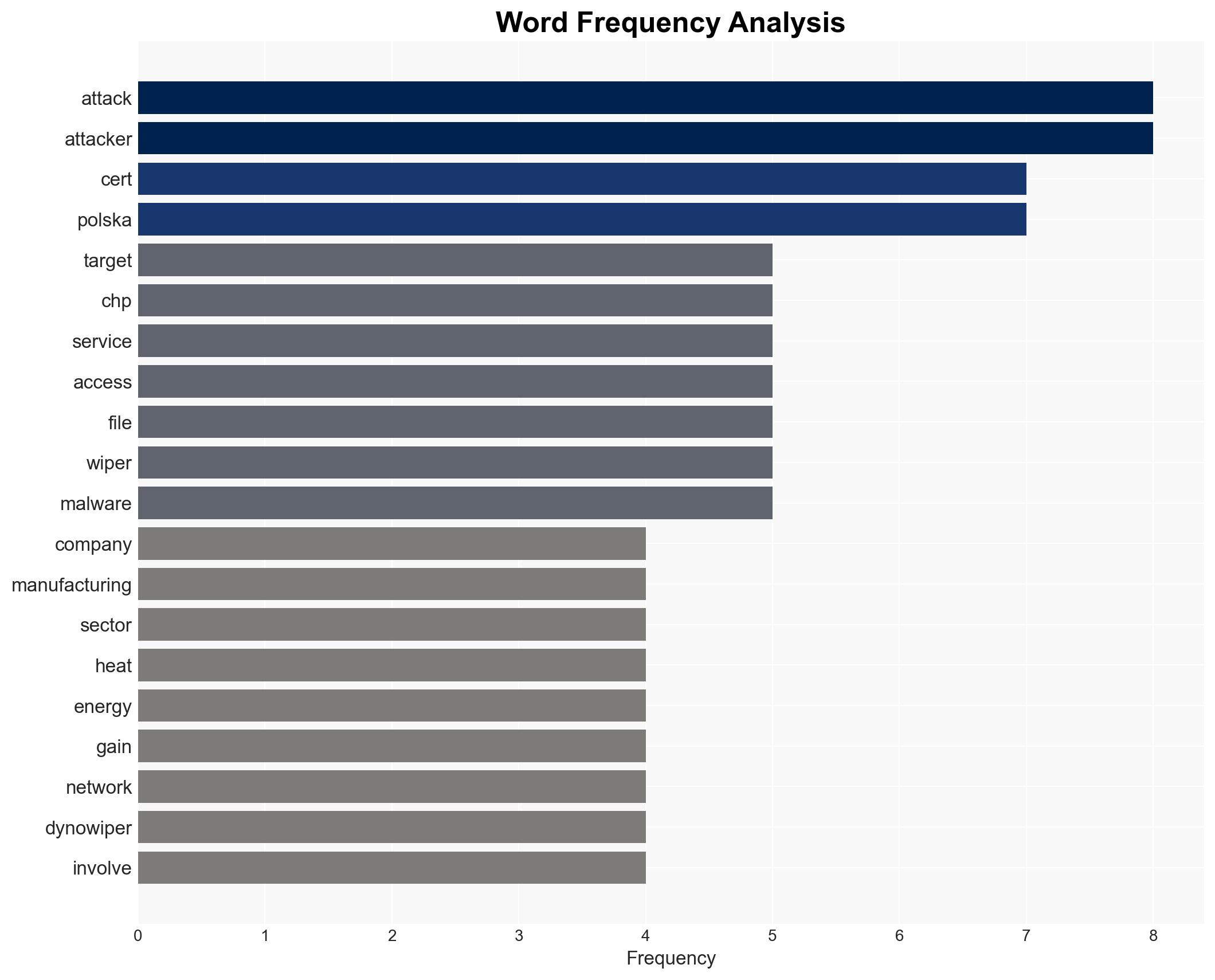
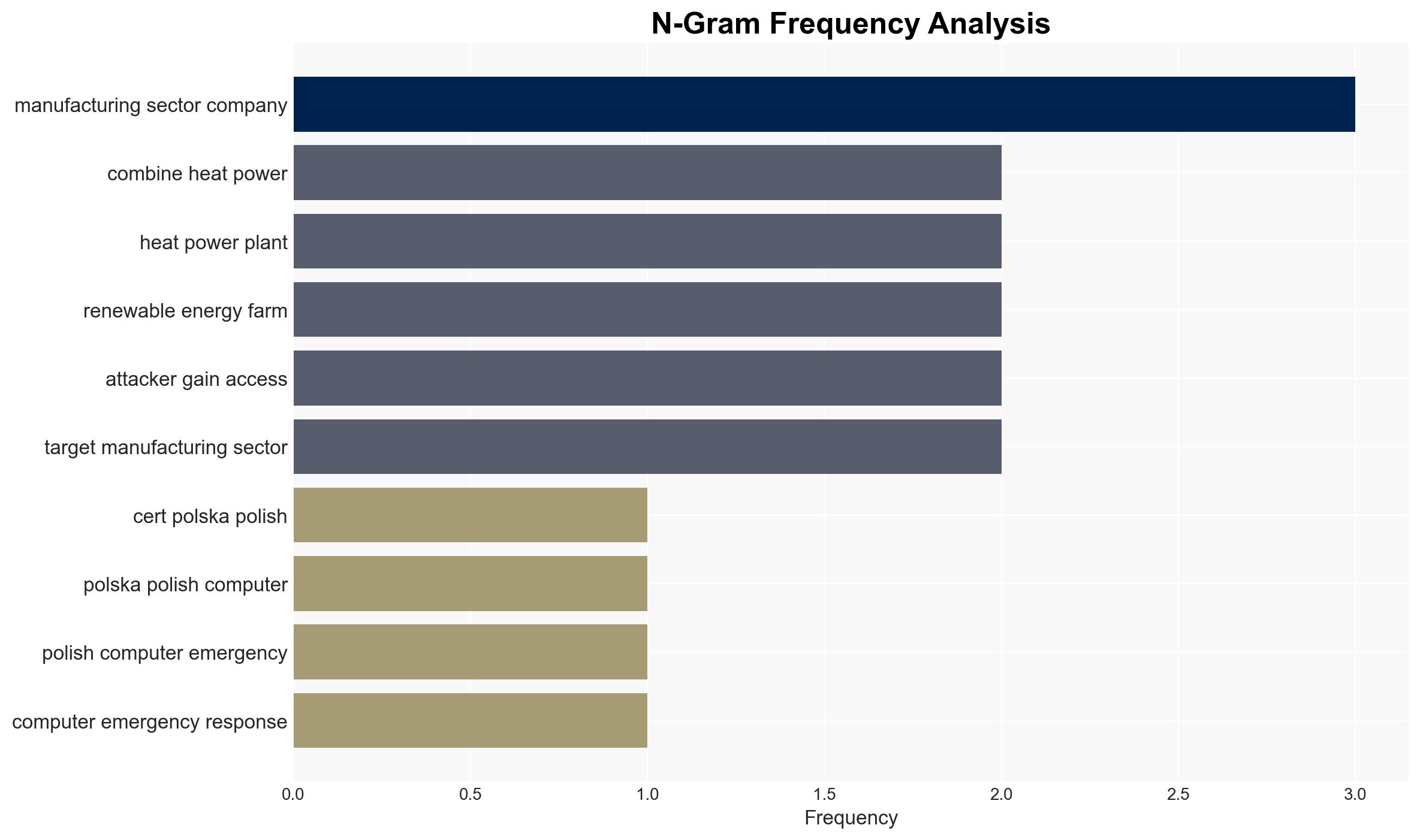
Coordinated cyber attacks attributed to the Russian-linked group Static Tundra targeted critical energy infrastructure in Poland, including wind and solar farms, a manufacturing company, and a combined heat and power plant. The attacks were primarily destructive but failed to disrupt energy production or heat supply. The attribution to Static Tundra is contested by other reports suggesting Sandworm involvement. Overall, this assessment is made with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The attacks were conducted by Static Tundra, linked to Russia’s FSB, as part of a strategic campaign to disrupt Poland’s energy sector. This is supported by CERT Polska’s attribution and the use of tactics consistent with Static Tundra’s historical activities. However, the attribution is contested by other cybersecurity firms.
- Hypothesis B: The attacks were carried out by Sandworm, another Russian state-sponsored group, aiming to test new cyber capabilities or as a diversionary tactic. This is supported by ESET and Dragos reports attributing the activity to Sandworm with moderate confidence.
- Assessment: Hypothesis A is currently better supported due to CERT Polska’s detailed analysis and historical patterns of Static Tundra’s operations. However, further evidence could shift this judgment, particularly if new technical indicators or intelligence confirm Sandworm’s involvement.
3. Key Assumptions and Red Flags
- Assumptions: The attribution to Static Tundra is accurate; the attacks were state-sponsored; the primary objective was disruption rather than espionage.
- Information Gaps: Lack of detailed technical indicators linking the attacks definitively to either group; limited visibility into the attackers’ long-term strategic objectives.
- Bias & Deception Risks: Potential bias in attribution due to geopolitical tensions; risk of deception by attackers using false flags to mislead attribution efforts.
4. Implications and Strategic Risks
The attacks highlight vulnerabilities in Poland’s critical infrastructure and may signal an escalation in cyber operations targeting the energy sector. This could lead to increased geopolitical tensions and necessitate enhanced cybersecurity measures.
- Political / Geopolitical: Potential for increased tensions between Poland and Russia, with possible diplomatic repercussions.
- Security / Counter-Terrorism: Heightened threat environment for critical infrastructure, necessitating increased vigilance and security measures.
- Cyber / Information Space: Demonstrates evolving cyber capabilities and tactics, highlighting the need for improved cyber defenses and threat intelligence sharing.
- Economic / Social: While immediate economic impacts are minimal, ongoing threats could undermine investor confidence and public trust in energy reliability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks, implement immediate patching of known vulnerabilities, and increase threat intelligence sharing with allies.
- Medium-Term Posture (1–12 months): Develop resilience measures, including redundancy and incident response capabilities, and strengthen partnerships with international cybersecurity organizations.
- Scenario Outlook:
- Best Case: Improved defenses deter future attacks, and diplomatic efforts reduce tensions.
- Worst Case: Escalation of cyber attacks leads to significant disruptions and geopolitical conflict.
- Most Likely: Continued low-level cyber operations with periodic disruptions, requiring sustained defensive efforts.
6. Key Individuals and Entities
- Static Tundra (linked to Russia’s FSB), Sandworm (Russian state-sponsored group), CERT Polska, ESET, Dragos
7. Thematic Tags
cybersecurity, energy infrastructure, Russian cyber operations, critical infrastructure protection, cyber attribution, state-sponsored attacks, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us