Police nab Ogun hospital cleaner posing as doctor to defraud woman
Published on: 2025-11-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
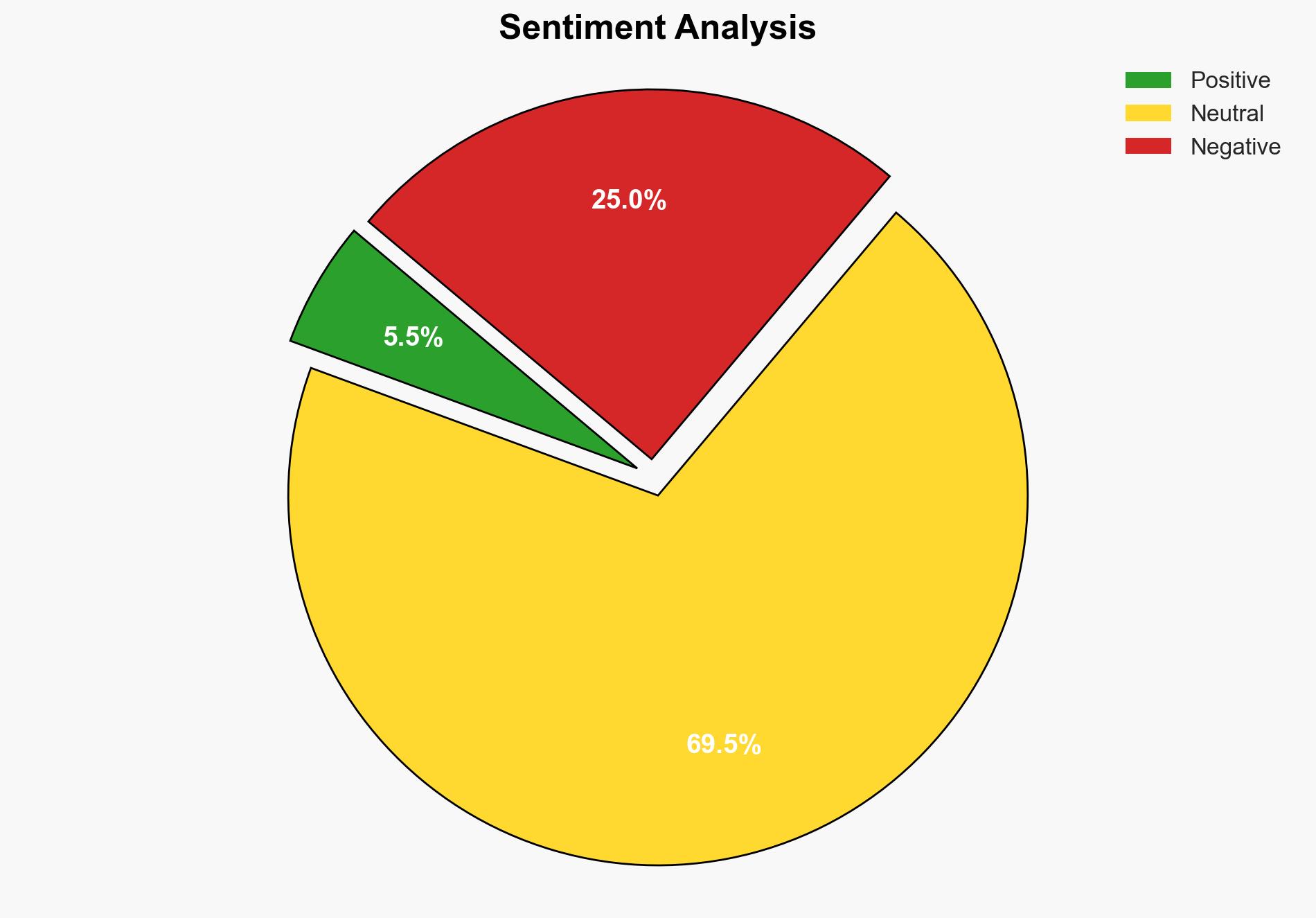
The most supported hypothesis is that Victor Cletus exploited social media platforms to impersonate a medical professional, targeting vulnerable individuals for financial and sexual exploitation. Confidence level: High. Recommended action includes enhancing public awareness campaigns and strengthening cybersecurity measures to prevent similar incidents.
2. Competing Hypotheses
Hypothesis 1: Victor Cletus deliberately used social media to impersonate a doctor to exploit and defraud individuals, indicating a premeditated criminal strategy.
Hypothesis 2: Cletus’s actions were opportunistic rather than premeditated, driven by immediate financial needs rather than a sustained criminal enterprise.
Hypothesis 1 is more likely due to the structured approach Cletus used, including fabricating credentials and consistently demanding money and sexual favors, suggesting a calculated plan rather than a spontaneous act.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that Cletus acted alone without a network of accomplices. The victim’s account is assumed to be accurate and truthful.
Red Flags: The use of social media for impersonation and the lack of verification mechanisms for professional credentials online are significant red flags.
Deception Indicators: Cletus’s ability to convincingly present himself as a medical professional suggests potential prior experience or knowledge in the field.
4. Implications and Strategic Risks
The incident highlights vulnerabilities in online identity verification, posing broader risks of similar crimes. If unaddressed, such exploitation could escalate, leading to increased public distrust in digital platforms and potential reputational damage to legitimate institutions like Babcock University Teaching Hospital.
5. Recommendations and Outlook
- Enhance public awareness campaigns focusing on the risks of online interactions and identity verification.
- Implement stricter cybersecurity measures and verification protocols for professional credentials on social media platforms.
- Best-case scenario: Public awareness and improved cybersecurity measures reduce similar incidents.
- Worst-case scenario: Failure to address these issues leads to an increase in online impersonation crimes.
- Most-likely scenario: Incremental improvements in public awareness and cybersecurity measures mitigate but do not eliminate the risk.
6. Key Individuals and Entities
Victor Cletus, CSP Omolola Odutola, Lanre Ogunlowo.
7. Thematic Tags
Cybersecurity, Online Fraud, Identity Verification, Social Media Risks
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us