Police report Bondi Beach shooter received firearms training with father prior to attack.
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Bondi Beach gunmen got firearms training together police say
1. BLUF (Bottom Line Up Front)
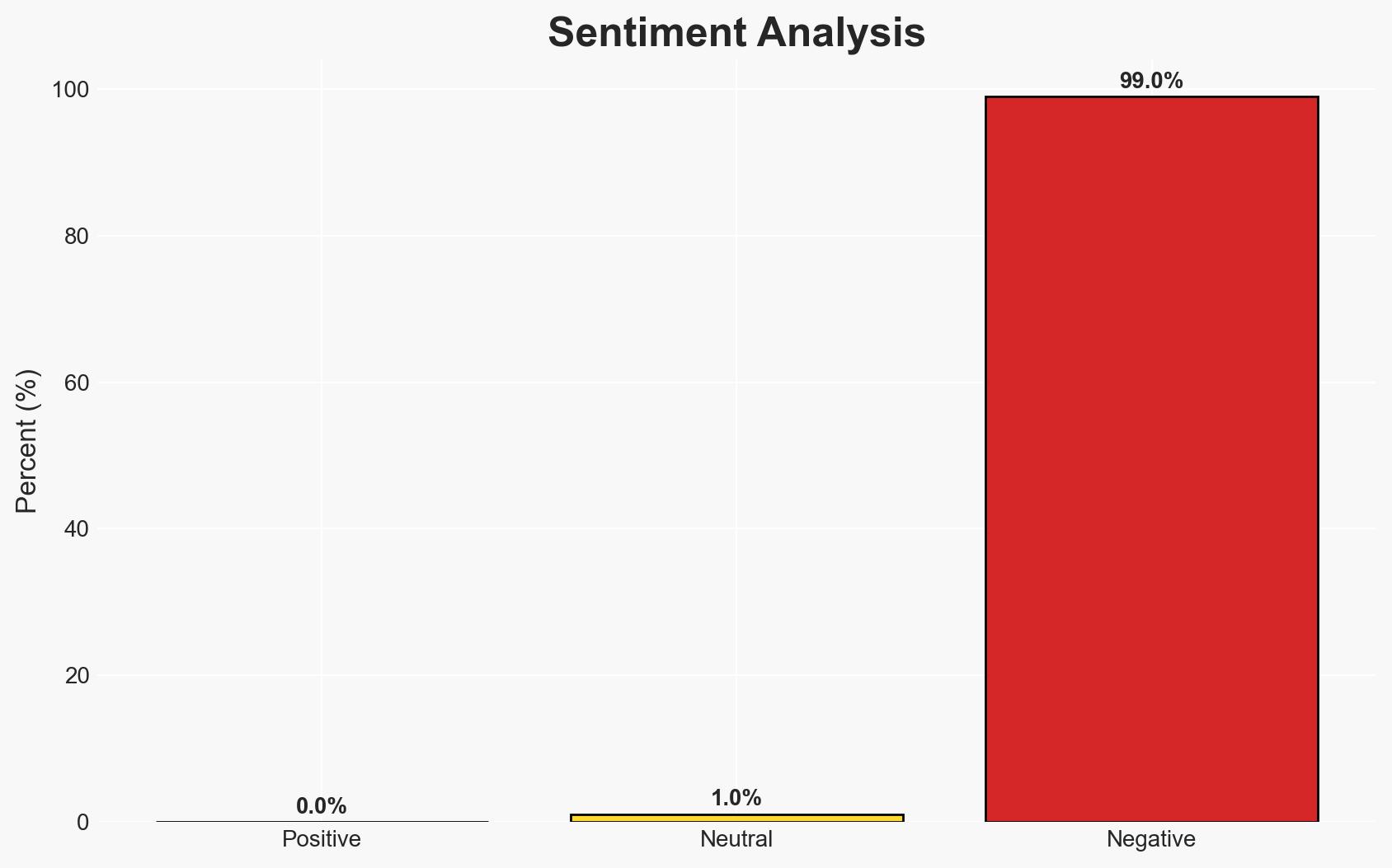
The Bondi Beach attack, reportedly inspired by ISIS, involved firearms training and the use of improvised explosive devices by Naveed Akram and his father. The attack highlights significant gaps in counter-terrorism measures and firearms regulation in Australia. Given the available evidence, the hypothesis that the attackers were self-radicalized with external influences is currently better supported. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was primarily self-radicalized, with Naveed and Sajid Akram acting independently but inspired by ISIS ideology. Supporting evidence includes their firearms training and the presence of ISIS flags. However, uncertainties remain about the extent of any direct ISIS involvement.
- Hypothesis B: The attack was orchestrated with direct operational support from ISIS or an affiliated group. This is contradicted by the lack of evidence of direct contact or operational support, as indicated by their limited activity during the trip to the Philippines.
- Assessment: Hypothesis A is currently better supported due to the lack of direct evidence of external operational support. Key indicators that could shift this judgment include evidence of communication with ISIS operatives or financial support from external sources.
3. Key Assumptions and Red Flags
- Assumptions: The attackers were primarily motivated by ISIS ideology; the firearms training was a significant factor in the attack’s execution; the trip to the Philippines was related to radicalization efforts.
- Information Gaps: Details on the nature and extent of the attackers’ communication with ISIS or affiliated groups; comprehensive analysis of the trip to the Philippines.
- Bias & Deception Risks: Potential bias in attributing the attack solely to ISIS influence without considering other radicalization pathways; possible deception in attackers’ motives or affiliations.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of radicalization pathways and firearms regulations in Australia, potentially influencing policy changes and international cooperation on counter-terrorism.
- Political / Geopolitical: Potential strain on Australia-Philippines relations if further links to local insurgencies are established.
- Security / Counter-Terrorism: Increased threat level and potential for copycat attacks; need for enhanced surveillance and intelligence-sharing.
- Cyber / Information Space: Possible increase in online radicalization efforts and propaganda dissemination by ISIS affiliates.
- Economic / Social: Potential impact on tourism and community relations, particularly affecting Jewish communities and public event security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of radicalization indicators, review firearms licensing processes, and increase security at public events.
- Medium-Term Posture (1–12 months): Strengthen international counter-terrorism partnerships, particularly with Southeast Asian nations, and invest in community resilience programs.
- Scenario Outlook: Best: Strengthened counter-terrorism measures prevent further attacks. Worst: Increased radicalization leads to more attacks. Most-Likely: Continued isolated incidents with improved response capabilities.
6. Key Individuals and Entities
- Naveed Akram – Accused attacker
- Sajid Akram – Deceased attacker
- ISIS – Ideological influence
- Australian Police – Investigating authority
- Australian Government – Policy-making body
7. Thematic Tags
Counter-Terrorism, radicalization, firearms regulation, ISIS influence, Australia-Philippines relations, public security, intelligence sharing
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us