Polish Authorities Detain Three Ukrainians for Alleged Possession of Hacking Equipment and Defense Data Theft
Published on: 2025-12-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
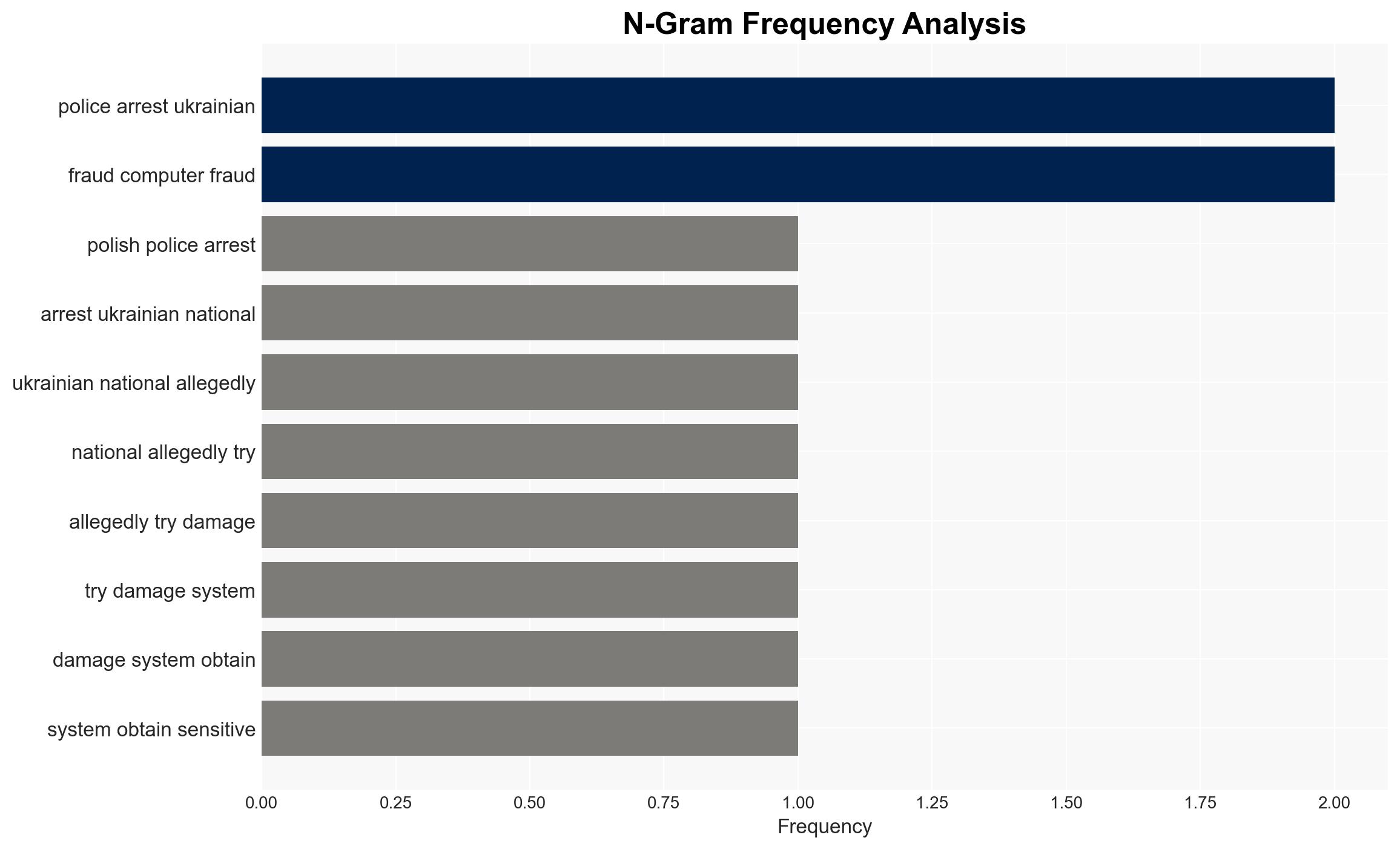
Intelligence Report: Polish Police arrest 3 Ukrainians for possessing advanced hacking tools
1. BLUF (Bottom Line Up Front)
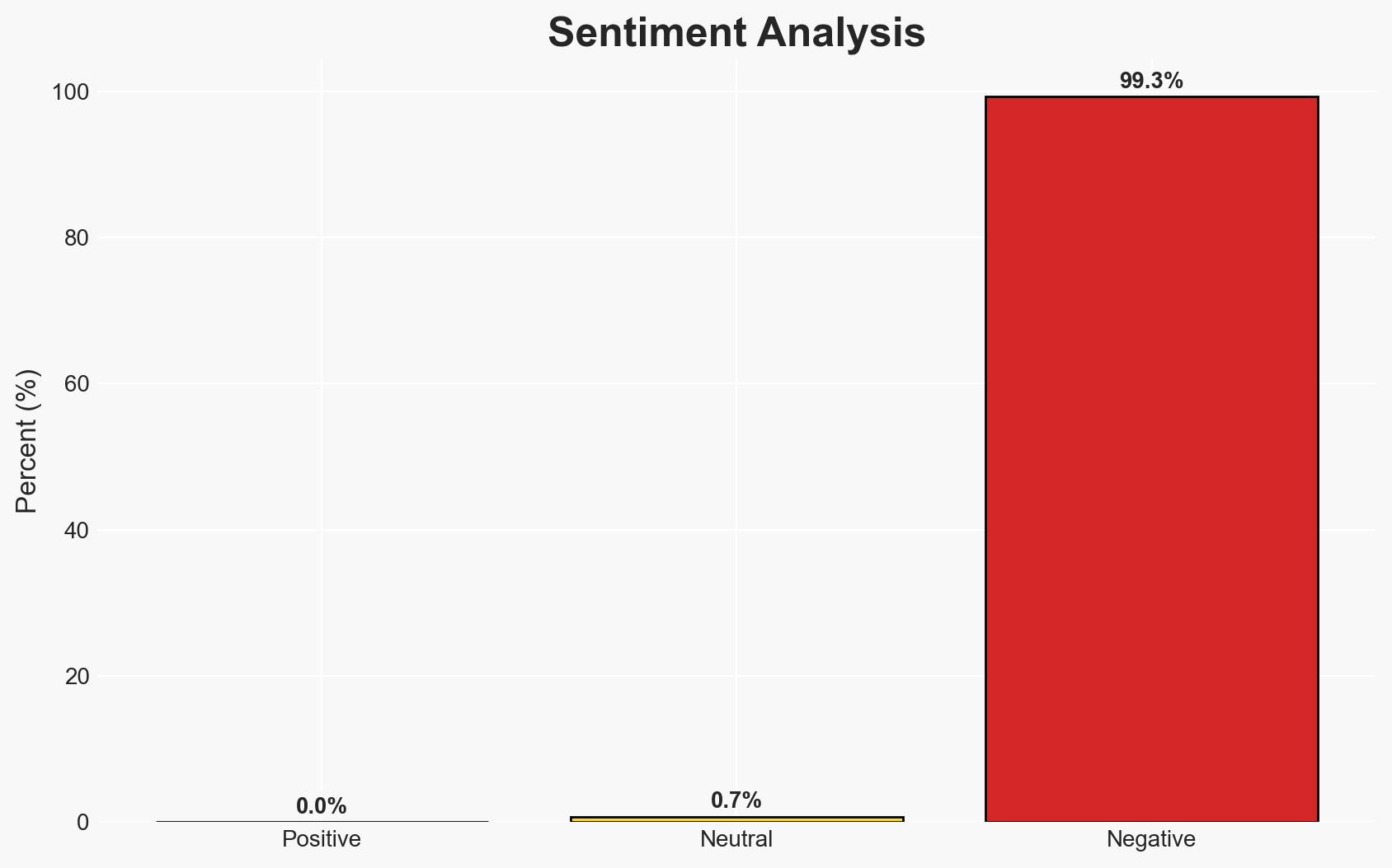
Polish authorities have detained three Ukrainian nationals suspected of possessing advanced hacking tools with potential implications for national defense IT systems. The most likely hypothesis is that these individuals were involved in unauthorized cyber activities targeting sensitive infrastructure. This incident could affect regional cybersecurity dynamics and bilateral relations. Overall confidence in this assessment is moderate due to existing information gaps.
2. Competing Hypotheses
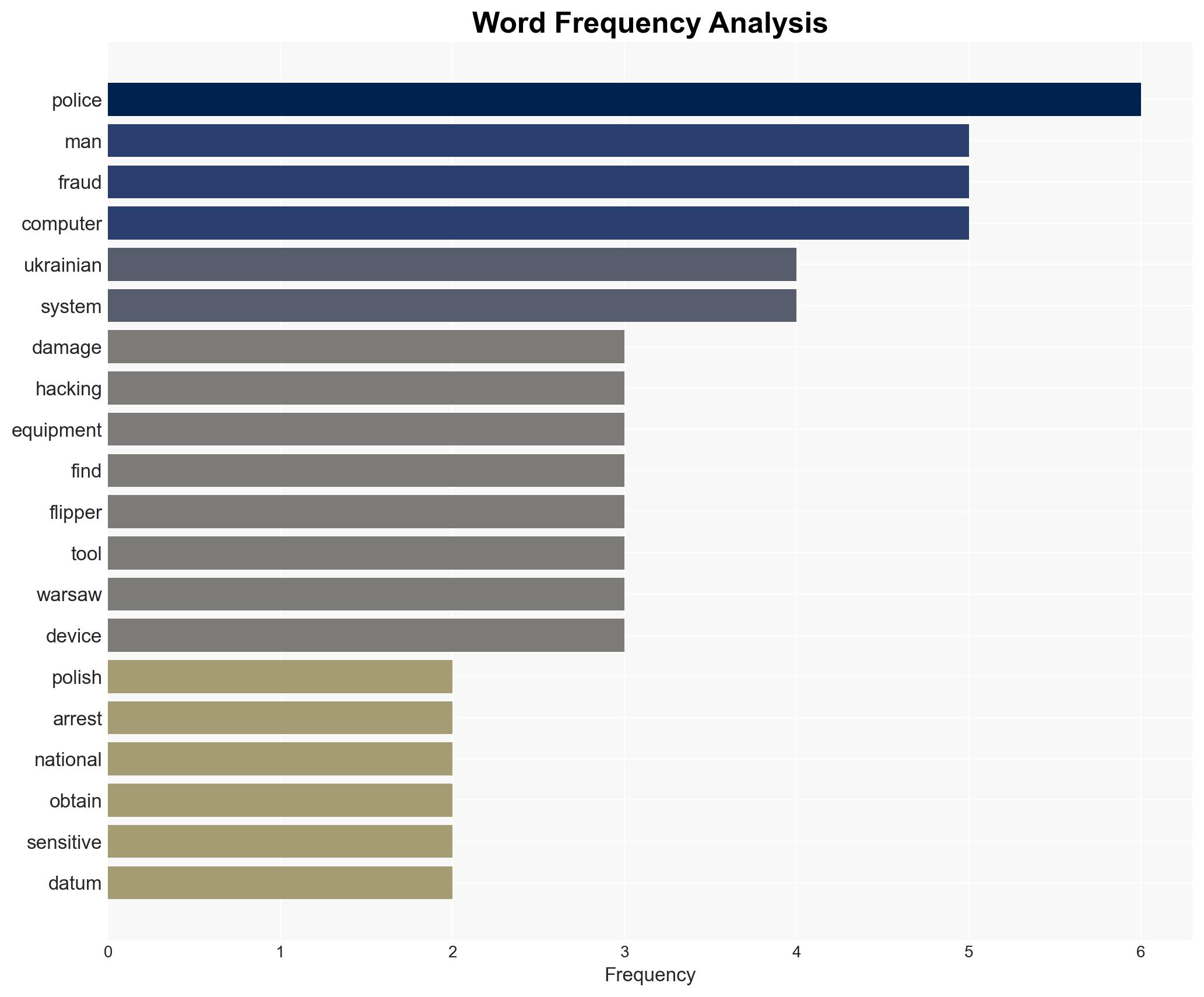
- Hypothesis A: The suspects were engaged in espionage or cyber operations targeting Polish national defense systems. Supporting evidence includes the possession of advanced hacking tools and counter-surveillance equipment. However, the suspects’ true intentions remain unclear, and their claims of being IT experts could be a cover.
- Hypothesis B: The suspects were independently conducting cybercriminal activities unrelated to state-sponsored espionage. This is supported by the charges of fraud and computer fraud. Contradicting this is the sophistication of the equipment, which suggests a higher level of organization.
- Assessment: Hypothesis A is currently better supported due to the nature of the equipment and the context of the arrests. Key indicators that could shift this judgment include further evidence of state sponsorship or clarification of the suspects’ affiliations and objectives.
3. Key Assumptions and Red Flags
- Assumptions: The suspects’ possession of advanced tools implies intent to use them for unauthorized access; the equipment’s sophistication suggests organized activity; the suspects’ nervous behavior indicates awareness of illicit activities.
- Information Gaps: The specific targets and objectives of the suspects; any connections to state actors or organized cybercrime groups; the full extent of the data potentially compromised.
- Bias & Deception Risks: Potential bias in interpreting the suspects’ nationality as indicative of state-sponsored activity; risk of deception by the suspects regarding their true intentions and affiliations.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of Ukrainian nationals in Poland and heightened cybersecurity measures. It may also strain Poland-Ukraine relations if state involvement is suspected.
- Political / Geopolitical: Potential diplomatic tensions between Poland and Ukraine; increased regional focus on cybersecurity cooperation.
- Security / Counter-Terrorism: Heightened alertness to potential cyber threats targeting national infrastructure; possible reevaluation of security protocols.
- Cyber / Information Space: Increased awareness and monitoring of cyber tools like Flipper Zero; potential for copycat incidents or further exploitation of similar tools.
- Economic / Social: Possible impact on IT and cybersecurity sectors; public concern over national security vulnerabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cross-border cyber activities; conduct thorough forensic analysis of seized devices; engage in diplomatic dialogue with Ukraine.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity frameworks and international cooperation; develop public-private partnerships for threat intelligence sharing.
- Scenario Outlook:
- Best: The incident is isolated, leading to improved cybersecurity measures without diplomatic fallout.
- Worst: Evidence of state-sponsored activity emerges, escalating regional tensions and cyber threats.
- Most-Likely: The suspects are found to be part of a non-state actor group, leading to increased cybersecurity vigilance.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, espionage, Poland-Ukraine relations, cybercrime, national defense, information security, regional security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us