Pondurance’s RansomSnare Prevents Ransomware Encryption and Data Theft in Real-Time
Published on: 2026-01-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pondurance RansomSnare blocks file encryption and data exfiltration
1. BLUF (Bottom Line Up Front)
Pondurance’s RansomSnare represents a significant advancement in ransomware prevention by halting attacks before file encryption and data exfiltration occur, potentially reducing operational and regulatory impacts. This capability is particularly beneficial for mid-market organizations in regulated sectors. The most likely hypothesis is that RansomSnare will enhance cybersecurity resilience for these organizations, with moderate confidence due to existing information gaps regarding its operational effectiveness across diverse threat environments.
2. Competing Hypotheses
- Hypothesis A: RansomSnare will significantly reduce ransomware incidents for mid-market organizations by preventing encryption and exfiltration. This is supported by its design to stop ransomware processes without relying on signatures or baselines, but lacks empirical data on its effectiveness across varied attack vectors.
- Hypothesis B: RansomSnare may not substantially impact ransomware incidents due to potential adaptation by threat actors to bypass its mechanisms. This hypothesis is supported by the historical adaptability of ransomware techniques, though currently lacking specific evidence of such adaptations targeting RansomSnare.
- Assessment: Hypothesis A is currently better supported due to the innovative nature of RansomSnare’s approach and its alignment with current needs in mid-market sectors. Indicators such as successful bypass attempts or increased ransomware incidents despite RansomSnare deployment could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: RansomSnare operates effectively across all ransomware variants; mid-market organizations will adopt the technology; threat actors will not rapidly develop countermeasures.
- Information Gaps: Empirical data on RansomSnare’s performance in real-world scenarios; detailed threat actor capabilities and adaptation timelines.
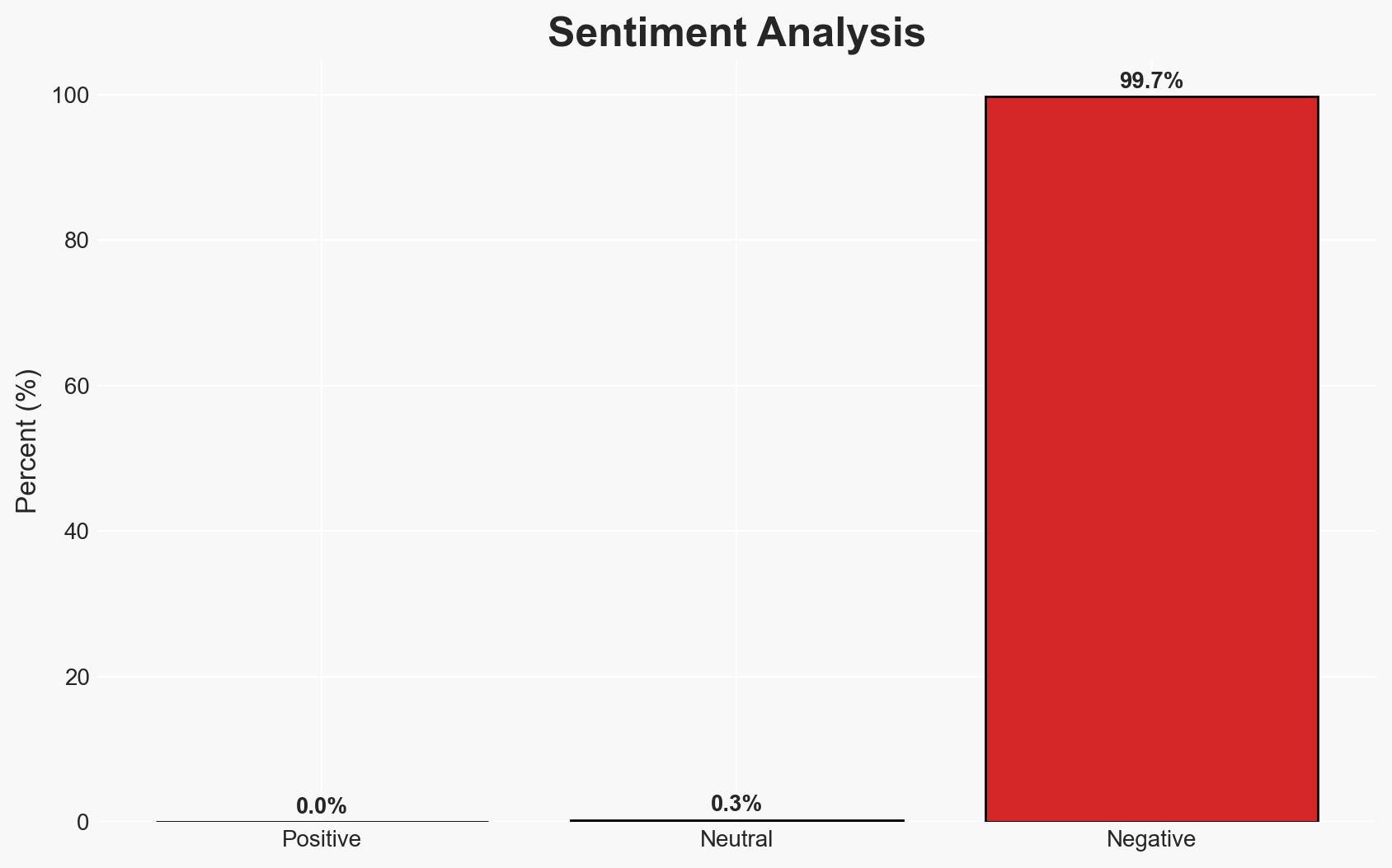
- Bias & Deception Risks: Potential bias from Pondurance’s promotional materials; lack of independent verification of RansomSnare’s capabilities; possible underreporting of bypass incidents by affected organizations.
4. Implications and Strategic Risks
The introduction of RansomSnare could alter the cybersecurity landscape by providing a robust defense against ransomware, though its long-term effectiveness remains uncertain.
- Political / Geopolitical: Could influence national cybersecurity policies and international collaboration on cyber defense.
- Security / Counter-Terrorism: May reduce the operational success of ransomware groups, potentially shifting their focus to less protected targets.
- Cyber / Information Space: Could drive innovation in ransomware tactics, leading to an arms race in cyber capabilities.
- Economic / Social: Potential reduction in financial losses and reputational damage for mid-market organizations, improving economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor RansomSnare deployment outcomes; engage with Pondurance for detailed technical briefings; assess integration with existing cybersecurity frameworks.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for shared threat intelligence; invest in training for security teams on new defensive technologies.
- Scenario Outlook:
- Best: RansomSnare significantly reduces ransomware incidents, leading to widespread adoption.
- Worst: Threat actors quickly adapt, nullifying RansomSnare’s effectiveness.
- Most-Likely: RansomSnare provides a temporary advantage, prompting ongoing adaptation by both defenders and attackers.
6. Key Individuals and Entities
- Doug Howard, CEO of Pondurance
- Pondurance (Cybersecurity firm)
- Not clearly identifiable from open sources in this snippet for additional individuals or entities.
7. Thematic Tags
cybersecurity, ransomware prevention, cybersecurity innovation, mid-market organizations, data exfiltration, endpoint security, threat actor adaptation, regulatory compliance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us