Presentation Trust No One Securing the Modern Software Supply Chain with Zero Trust
Published on: 2025-11-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
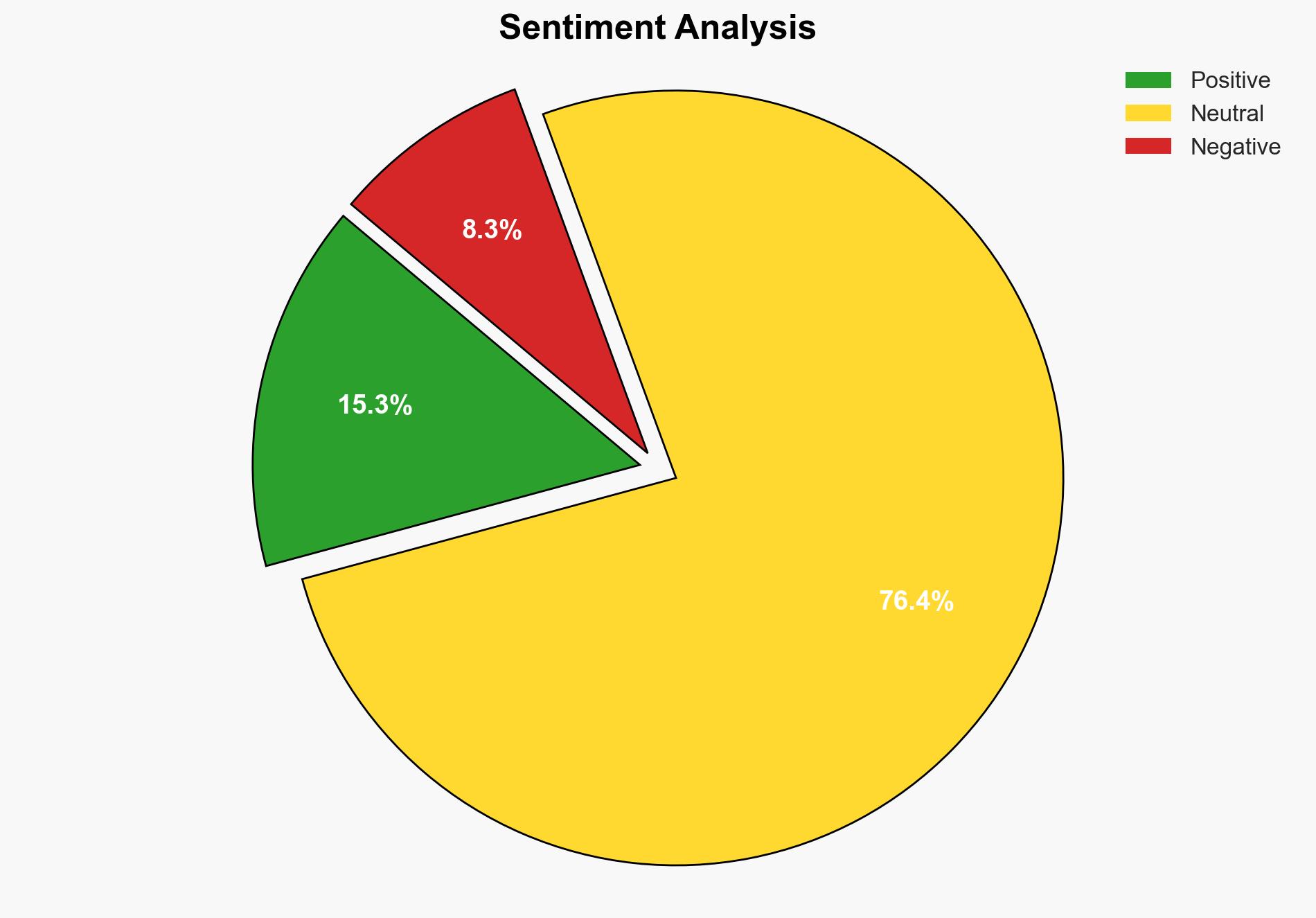
With moderate confidence, the most supported hypothesis is that the adoption of zero trust principles in securing the software supply chain will significantly mitigate the risk of supply chain attacks. It is recommended that organizations prioritize implementing zero trust frameworks in their CI/CD pipelines and enhance developer awareness to safeguard against evolving threats.
2. Competing Hypotheses
Hypothesis 1: Implementing zero trust principles in the software supply chain will significantly reduce the risk of supply chain attacks.
Hypothesis 2: Despite the adoption of zero trust principles, the complexity and sophistication of supply chain attacks will continue to pose a significant threat.
Hypothesis 1 is more supported due to the structured approach of zero trust in minimizing attack vectors and enhancing security controls at every stage of the software development lifecycle. However, Hypothesis 2 cannot be entirely dismissed given the adaptive nature of threat actors and the inherent vulnerabilities in open-source dependencies.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that organizations have the resources and expertise to implement zero trust frameworks effectively. Another assumption is that developers will adhere to security protocols and practices.
Red Flags: A potential red flag is the over-reliance on zero trust as a panacea, which might lead to complacency in other security areas. Additionally, the rapid evolution of attack techniques could outpace current zero trust implementations.
4. Implications and Strategic Risks
The failure to implement robust zero trust measures could lead to increased frequency and impact of supply chain attacks, affecting not only individual organizations but also their downstream customers. This could result in significant economic losses, reputational damage, and potential regulatory repercussions. Politically, such vulnerabilities could be exploited by state-sponsored actors to undermine national security.
5. Recommendations and Outlook
- Organizations should conduct comprehensive audits of their software supply chains to identify vulnerabilities and prioritize zero trust implementations.
- Invest in continuous training and awareness programs for developers to recognize and mitigate potential threats.
- Establish a robust incident response plan to quickly address and recover from supply chain attacks.
- Best-case scenario: Successful implementation of zero trust leads to a marked decrease in supply chain attacks.
- Worst-case scenario: Attackers develop new methods to bypass zero trust defenses, leading to widespread breaches.
- Most-likely scenario: A gradual reduction in attack success rates as organizations adapt and refine their security measures.
6. Key Individuals and Entities
Emma Yuan Fang, Security Architect at EPAM, leads the UK and Ireland security practice and is involved in various security initiatives.
7. Thematic Tags
Cybersecurity, Zero Trust, Software Supply Chain, CI/CD Pipeline, Open Source Security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us