Profile of Bondi Beach Attackers: Father-Son Duo Linked to Islamic State Behind Deadly Hanukkah Shooting
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: What we know about the Bondi gunmen
1. BLUF (Bottom Line Up Front)
The Bondi Beach attack, executed by a father-son duo, is assessed as a terrorist act motivated by extremist ideology, specifically allegiance to the Islamic State (IS). The incident resulted in significant casualties and is the worst mass shooting in Australia in decades. Current analysis supports the hypothesis that the attackers acted independently, without direct operational support from a larger network. Overall confidence in this assessment is moderate, given existing information gaps and potential biases.
2. Competing Hypotheses
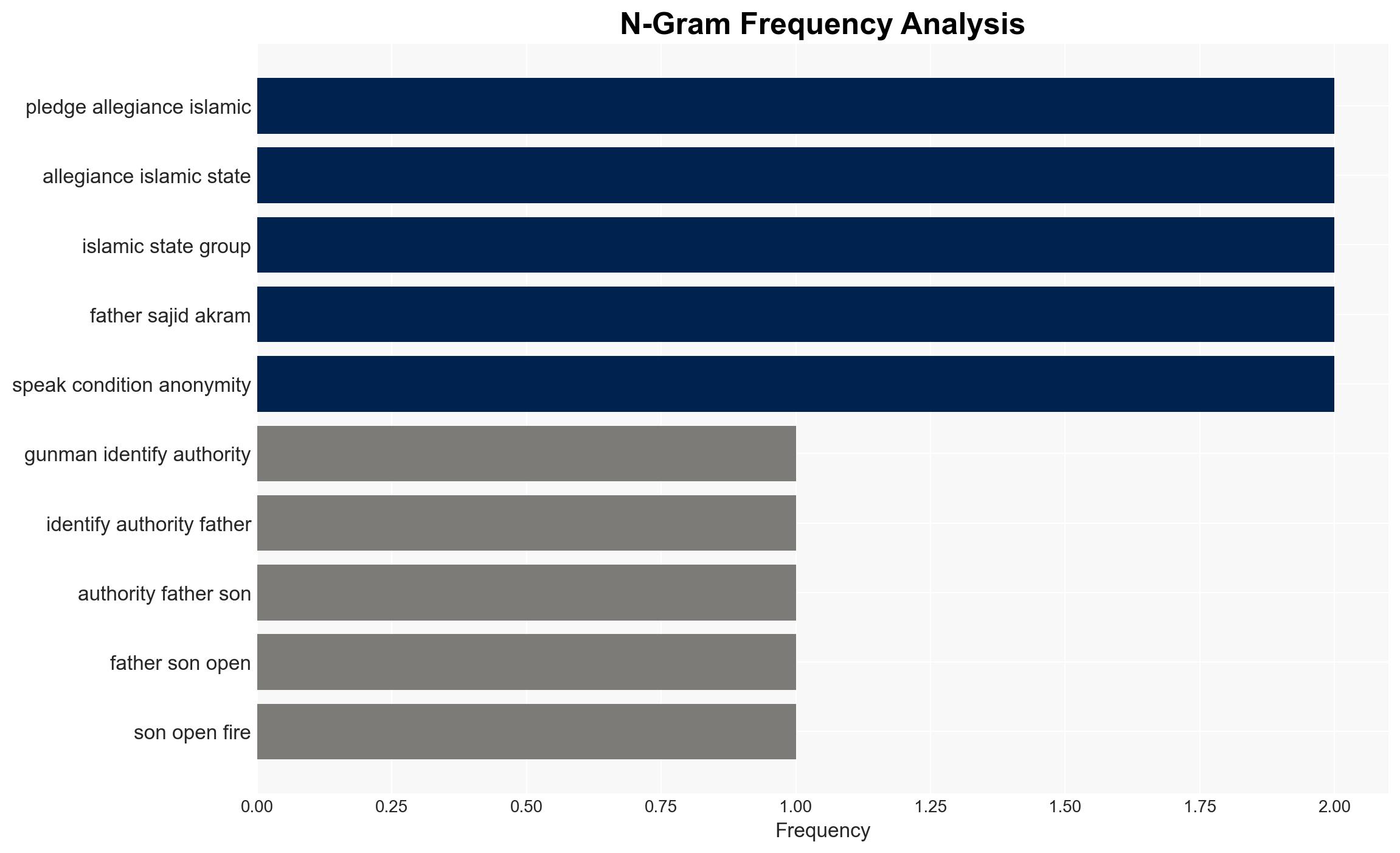
- Hypothesis A: The attack was an independent operation by the father-son duo, motivated by extremist ideology and allegiance to IS. Supporting evidence includes their pledge to IS, the presence of IS flags, and the lack of evidence linking them to a broader cell. However, uncertainties remain about potential indirect influences or communications with IS affiliates.
- Hypothesis B: The attack was part of a coordinated effort involving a larger extremist network. This is contradicted by the Prime Minister’s statement of no wider cell involvement and the lack of direct evidence of external coordination. However, the son’s past connections to known extremists suggest possible indirect influences.
- Assessment: Hypothesis A is currently better supported due to the lack of concrete evidence of broader network involvement and official statements confirming independent action. Key indicators that could shift this judgment include new intelligence on communications with external actors or discovery of logistical support from IS affiliates.
3. Key Assumptions and Red Flags
- Assumptions: The attackers acted independently; IS influence was ideological rather than operational; Australian intelligence has no evidence of broader network involvement.
- Information Gaps: Details on the attackers’ communications and planning processes; potential undisclosed connections to other extremists; full background on the father’s immigration history and affiliations.
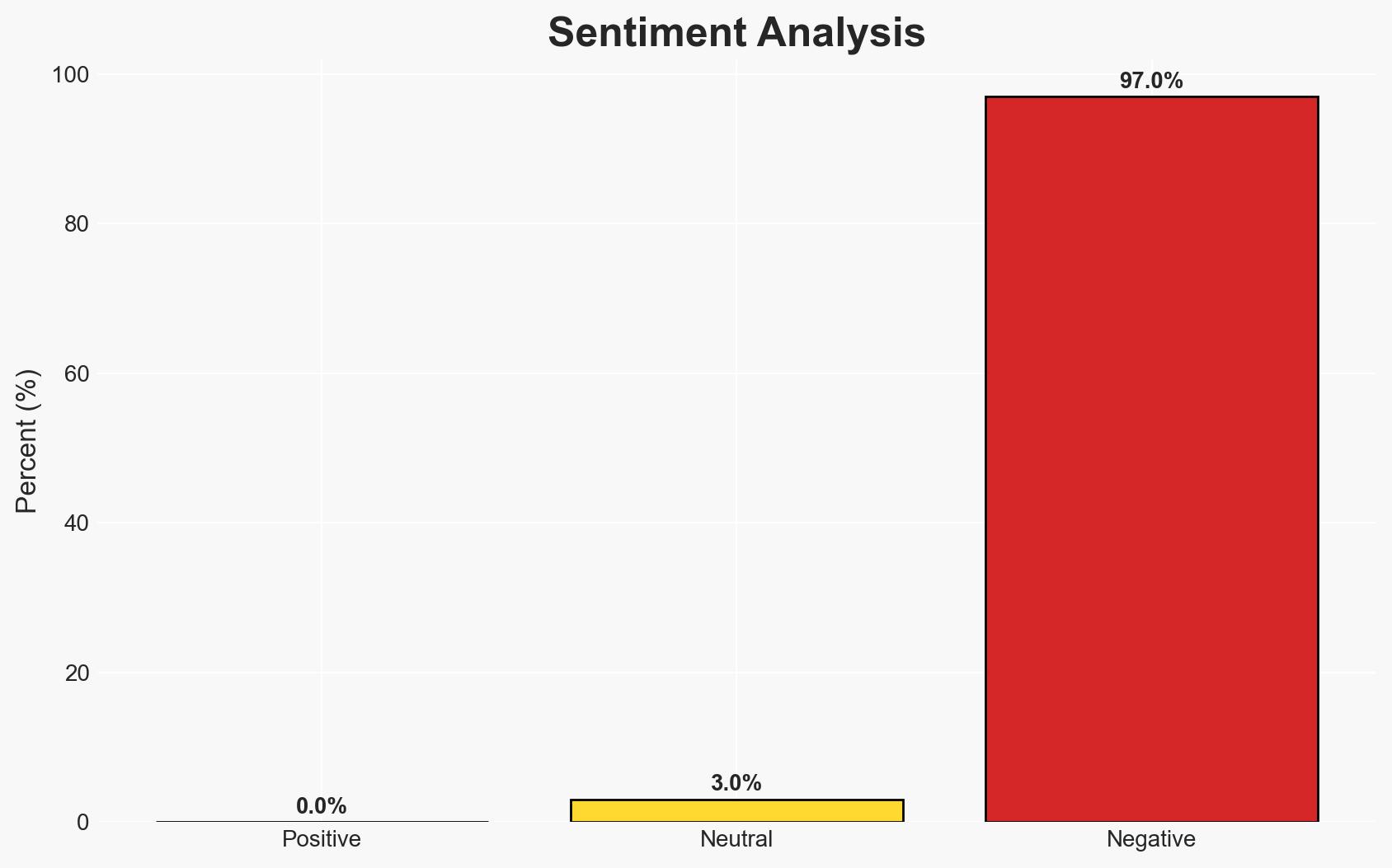
- Bias & Deception Risks: Potential confirmation bias in focusing on IS links; source bias from anonymous officials; risk of deception by attackers in pledging allegiance to IS as a diversion.
4. Implications and Strategic Risks
This attack could influence domestic and international counter-terrorism policies, potentially leading to increased security measures and scrutiny of extremist activities. The incident may also affect community relations and perceptions of security within Australia.
- Political / Geopolitical: Potential strain on immigration policies and international relations, particularly with countries linked to extremist ideologies.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation for monitoring lone actors and small cells.
- Cyber / Information Space: Increased propaganda and recruitment efforts by IS online, exploiting the attack for ideological gains.
- Economic / Social: Possible impacts on tourism and local economies, alongside heightened social tensions and community distrust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence sharing and coordination among agencies; increase monitoring of online extremist activities; engage with community leaders to mitigate social tensions.
- Medium-Term Posture (1–12 months): Develop resilience measures against lone-actor terrorism; strengthen partnerships with international counter-terrorism entities; invest in deradicalization programs.
- Scenario Outlook:
- Best: No further attacks; improved community relations and effective counter-terrorism measures.
- Worst: Additional attacks inspired by this incident; increased radicalization and community division.
- Most-Likely: Sporadic lone-actor threats; gradual improvement in intelligence capabilities and community engagement.
6. Key Individuals and Entities
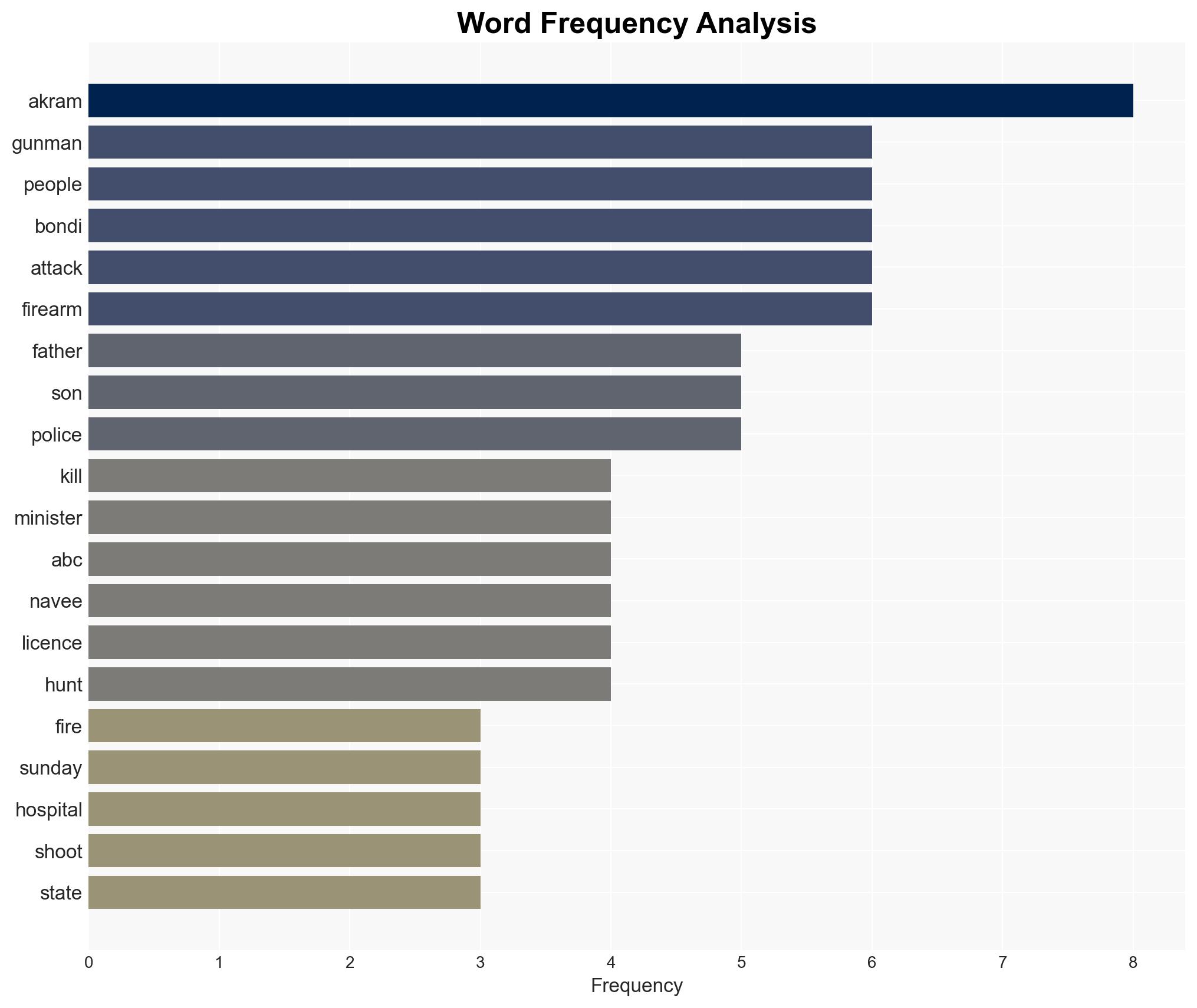
- Naveed Akram (attacker, hospitalized)
- Sajid Akram (attacker, deceased)
- Isaac El Matari (known extremist, linked to Naveed Akram)
- Islamic State (ideological influence)
- Australian Security Intelligence Organisation (ASIO)
- Joint Counter Terrorism Team (JCTT)
7. Thematic Tags
Counter-Terrorism, lone-actor terrorism, Islamic State, extremist ideology, community relations, intelligence sharing, radicalization
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us