Prosper disclosed a data breach impacting 176 million accounts – Securityaffairs.com
Published on: 2025-10-17
Intelligence Report: Prosper disclosed a data breach impacting 176 million accounts – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
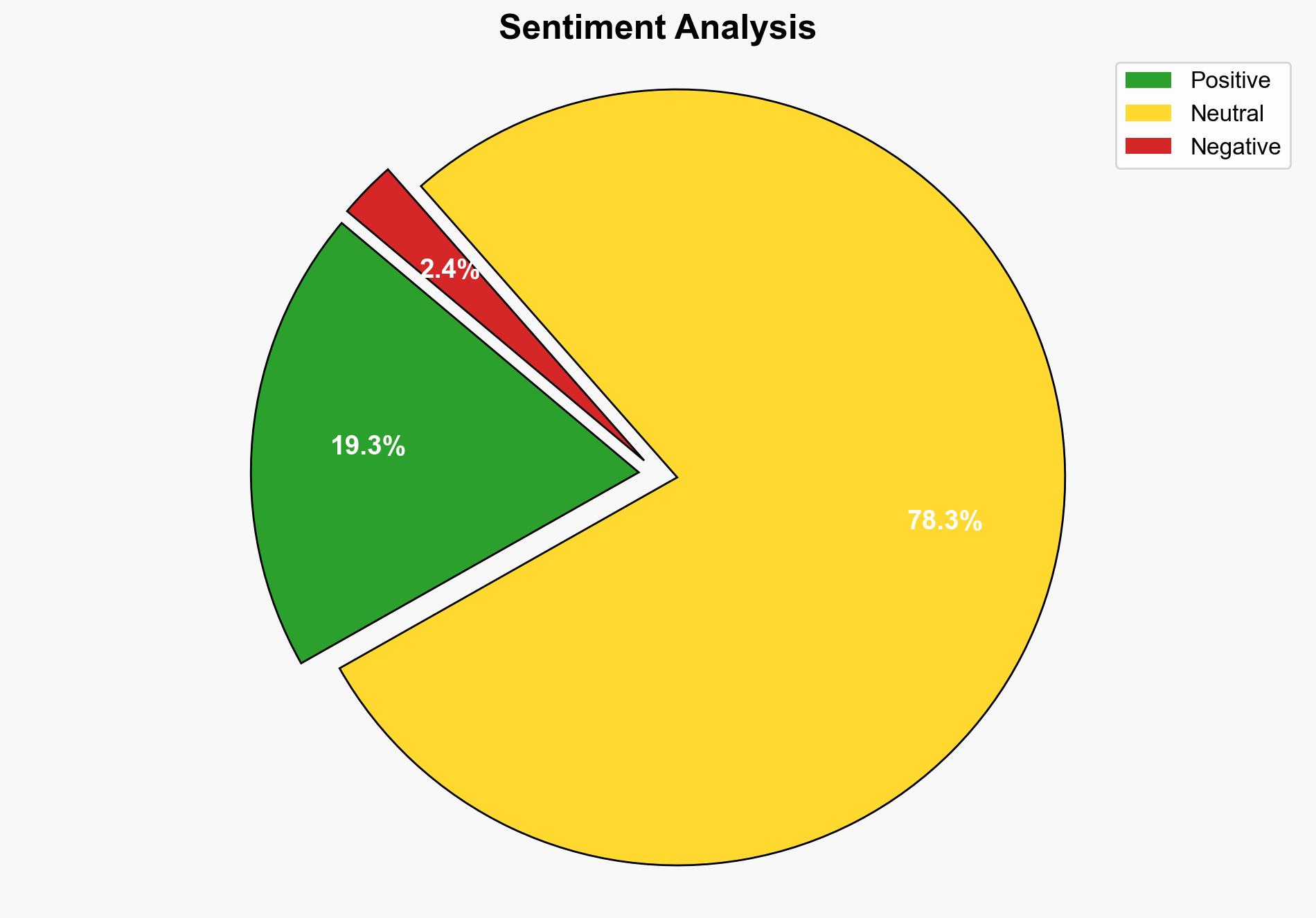
The most supported hypothesis is that the data breach at Prosper was a result of a sophisticated cyberattack aimed at extracting sensitive personal information for financial gain. This conclusion is derived from the structured analysis of available data, including the nature of the stolen information and the involvement of a cybersecurity firm in the investigation. Confidence in this hypothesis is moderate due to ongoing investigations and the lack of a confirmed perpetrator. Recommended actions include enhancing cybersecurity measures and conducting a comprehensive review of data protection protocols.
2. Competing Hypotheses
1. **Hypothesis A**: The breach was orchestrated by a financially motivated cybercriminal group seeking to exploit personal data for identity theft and fraud.
2. **Hypothesis B**: The breach was an insider threat, possibly involving a disgruntled employee or contractor with access to sensitive systems, aiming to undermine the company’s reputation or for personal gain.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported. The nature of the data stolen and the scale of the breach align with typical external cybercriminal activities. Hypothesis B lacks supporting evidence, as there is no indication of internal sabotage or motive.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the breach was detected promptly and that all affected data has been identified. The assumption that external actors are responsible is based on the involvement of a cybersecurity firm.
– **Red Flags**: The absence of a confirmed perpetrator raises questions about the completeness of the investigation. The lack of specific details about how the breach occurred could indicate either ongoing investigations or a gap in Prosper’s security awareness.
– **Potential Bias**: Confirmation bias may arise if investigators focus solely on external threats, potentially overlooking internal vulnerabilities.
4. Implications and Strategic Risks
The breach poses significant risks, including potential identity theft and financial fraud affecting millions of individuals. This incident could lead to increased regulatory scrutiny and damage to Prosper’s reputation, impacting customer trust and market position. If the breach is linked to a broader cyberattack campaign, it could signal heightened threats to the financial sector, necessitating industry-wide vigilance.
5. Recommendations and Outlook
- Enhance cybersecurity infrastructure, focusing on intrusion detection and response capabilities.
- Conduct a thorough audit of internal security protocols and employee access controls.
- Engage with industry partners to share threat intelligence and best practices.
- Scenario Projections:
- Best Case: The breach is contained with no further incidents, and affected individuals are protected through credit monitoring.
- Worst Case: The breach leads to widespread identity theft, resulting in significant financial losses and legal challenges.
- Most Likely: The breach results in moderate financial and reputational damage, prompting regulatory changes and improved security measures.
6. Key Individuals and Entities
– Prosper
– Have I Been Pwned (HIBP)
7. Thematic Tags
national security threats, cybersecurity, financial sector risk, data protection