ProSpy ToSpy malware pose as Signal and ToTok to steal data in UAE – Securityaffairs.com
Published on: 2025-10-03
Intelligence Report: ProSpy ToSpy malware pose as Signal and ToTok to steal data in UAE – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
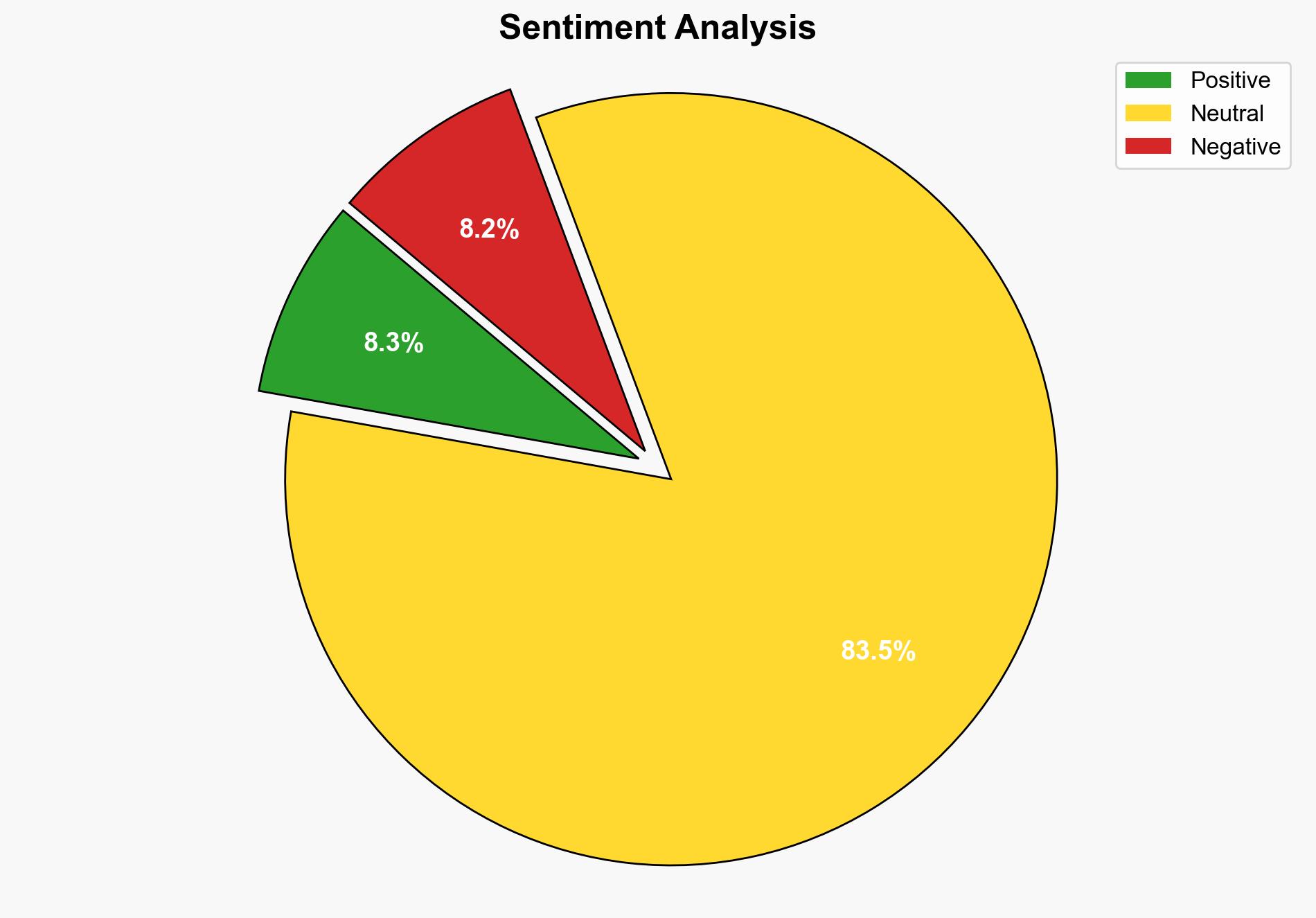
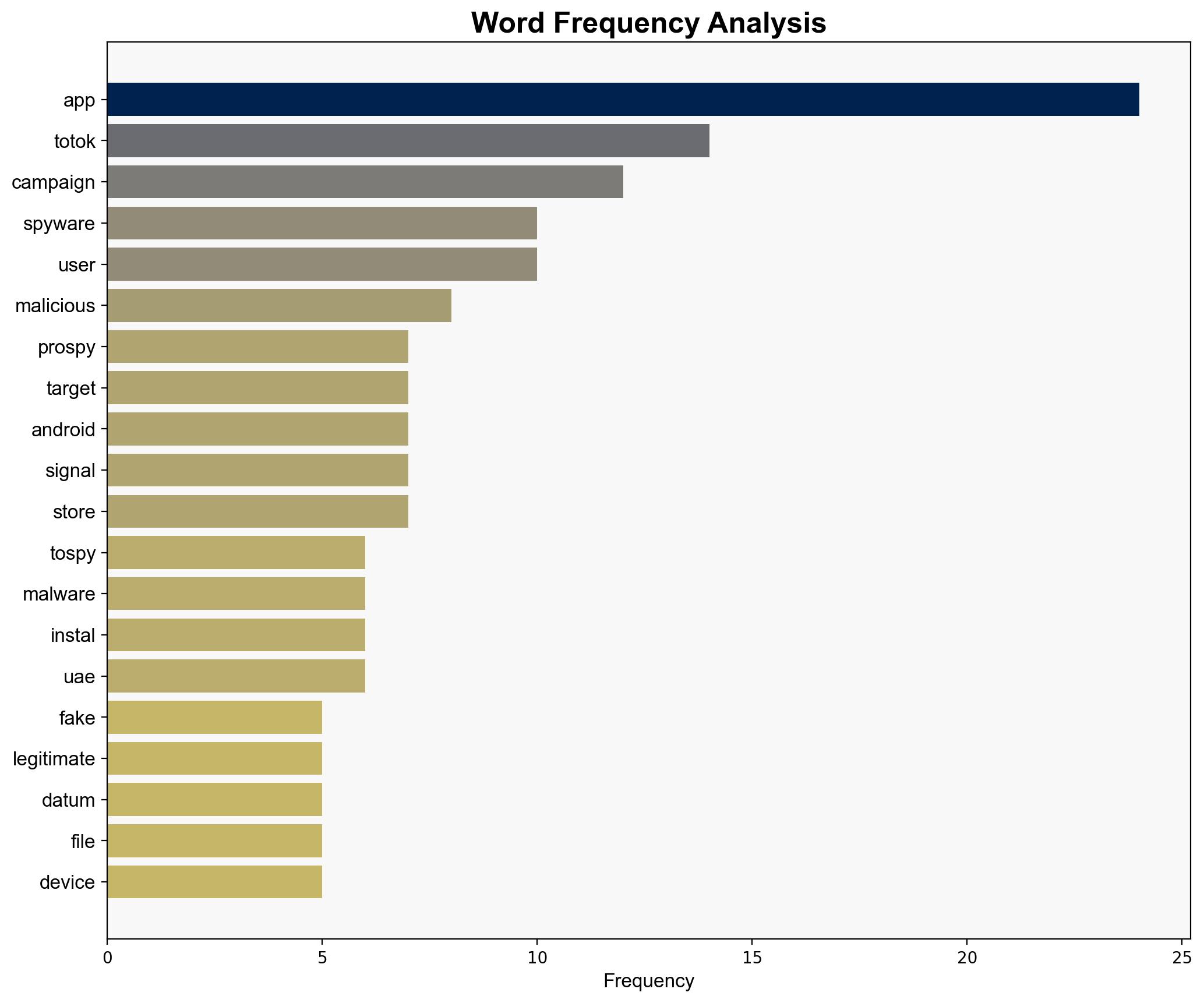
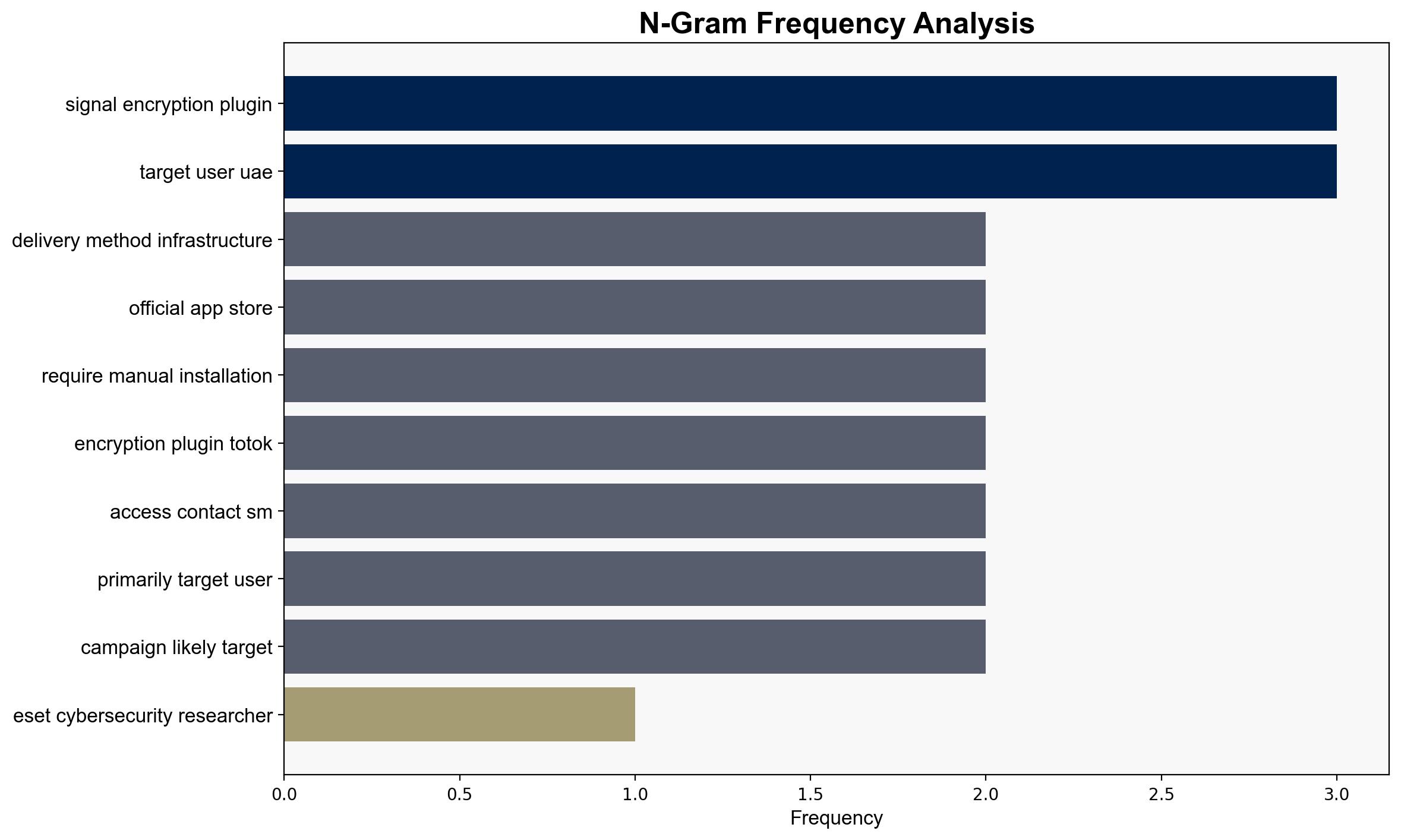
The ProSpy and ToSpy malware campaigns, targeting Android users in the UAE by impersonating popular apps like Signal and ToTok, represent a significant cybersecurity threat. The most supported hypothesis is that these campaigns are state-sponsored efforts aimed at surveillance and data collection. Confidence level: Moderate. Recommended action: Enhance cybersecurity awareness and defenses, particularly in regions vulnerable to such attacks.
2. Competing Hypotheses
1. **State-Sponsored Surveillance**: The malware campaigns are orchestrated by a state actor, potentially the UAE government, to conduct surveillance on its citizens and residents. This is supported by the targeted nature of the attacks and the historical context of ToTok being removed from app stores over similar concerns.
2. **Cybercriminal Exploitation**: The campaigns are driven by independent cybercriminals seeking to exploit users for financial gain through data theft and potential blackmail. This hypothesis considers the use of phishing sites and the impersonation of popular apps as typical cybercriminal tactics.
3. Key Assumptions and Red Flags
– **Assumptions**: The state-sponsored hypothesis assumes government involvement based on past incidents with ToTok. The cybercriminal hypothesis assumes financial motivation without direct evidence.
– **Red Flags**: The lack of direct attribution to a specific actor and the reliance on phishing sites raise questions about the true origin and intent of the campaigns.
– **Blind Spots**: Limited information on the infrastructure and command-and-control servers used in the campaigns.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: Continued exploitation of popular apps could undermine trust in digital communications and lead to widespread data breaches.
– **Geopolitical Risks**: If state-sponsored, these campaigns could strain international relations and lead to increased scrutiny of UAE’s digital policies.
– **Economic Risks**: Potential economic impact due to loss of consumer confidence in digital services and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- **Mitigation**: Implement robust cybersecurity training for users, focusing on recognizing phishing attempts and verifying app sources.
- **Technical Measures**: Strengthen app store vetting processes and enhance monitoring of app distribution channels.
- **Scenario Projections**:
– **Best Case**: Increased awareness and improved defenses lead to a decline in successful attacks.
– **Worst Case**: Escalation of attacks with broader regional impact and potential international fallout.
– **Most Likely**: Continued targeted attacks with gradual improvements in user defenses and app store security.
6. Key Individuals and Entities
No specific individuals are named in the intelligence. Entities involved include ESET cybersecurity researchers and potentially the UAE government.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus