Quantum computers will be a dream come true for hackers risking everything from military secrets to bank information Can we stop them – Live Science
Published on: 2025-04-04
Intelligence Report: Quantum computers will be a dream come true for hackers risking everything from military secrets to bank information Can we stop them – Live Science
1. BLUF (Bottom Line Up Front)
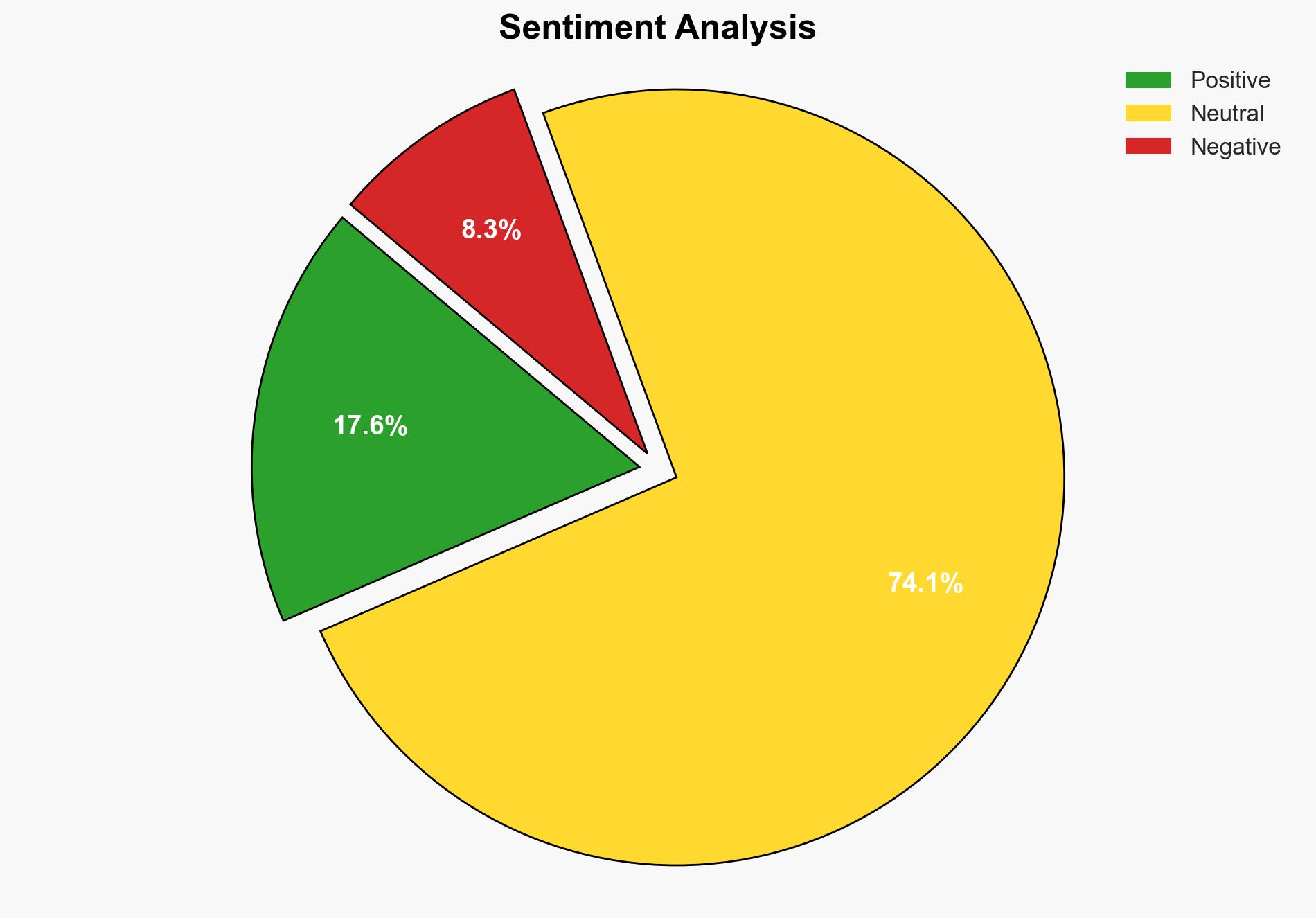
Quantum computing poses a significant threat to current cryptographic systems, potentially compromising sensitive data across military, financial, and personal sectors. Immediate action is required to develop and implement post-quantum cryptography to safeguard against these emerging threats. Stakeholders must prioritize investment in research and collaboration to ensure data security in the quantum era.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
Quantum computers, by leveraging quantum mechanical effects such as superposition and entanglement, offer unprecedented computational power. This capability threatens to render current cryptographic systems obsolete, as quantum algorithms can efficiently solve complex problems that classical computers cannot. The potential for quantum computers to crack encryption poses a significant risk to data security, necessitating the development of new cryptographic algorithms resistant to quantum attacks.
3. Implications and Strategic Risks
The advent of quantum computing presents several strategic risks:
- National Security: Quantum computers could decrypt classified military communications, exposing sensitive operations and strategies.
- Economic Interests: Financial institutions face risks as quantum computers could compromise banking encryption, leading to potential financial instability.
- Regional Stability: The imbalance in quantum computing capabilities among nations could lead to geopolitical tensions and an arms race in quantum technology.
4. Recommendations and Outlook
Recommendations:
- Accelerate research and development in post-quantum cryptography to create robust encryption methods resistant to quantum attacks.
- Encourage international collaboration to establish global standards and protocols for quantum-safe cryptographic practices.
- Invest in public-private partnerships to foster innovation and rapid deployment of quantum-resistant technologies.
Outlook:
Best-case scenario: Successful development and widespread adoption of post-quantum cryptography, ensuring data security and maintaining trust in digital systems.
Worst-case scenario: Delays in cryptographic advancements lead to widespread data breaches, undermining national security and economic stability.
Most likely outcome: Gradual transition to quantum-resistant systems, with intermittent security challenges as quantum computing technology matures.
5. Key Individuals and Entities
The report references several key individuals and entities involved in the quantum computing and cybersecurity landscape:
- Rebecca Krauthamer
- Britta Hale
- Michele Mosca
- Peter Shor
These individuals are pivotal in the ongoing efforts to address the challenges posed by quantum computing to data security.