Quantum computing will make cryptography obsolete But computer scientists are working to make them unhackable – Live Science
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Quantum computing will make cryptography obsolete But computer scientists are working to make them unhackable – Live Science
1. BLUF (Bottom Line Up Front)
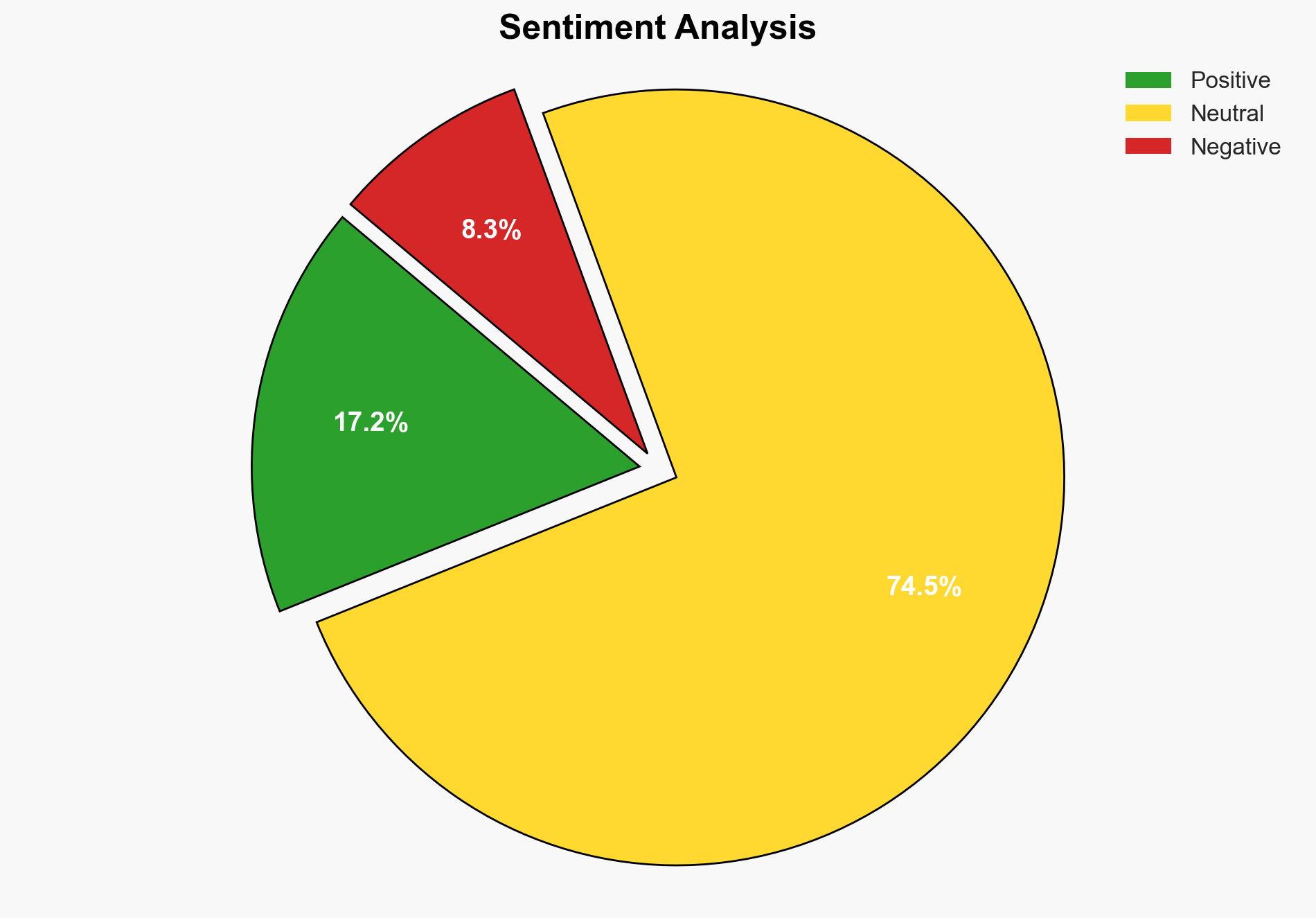
With a moderate confidence level, the most supported hypothesis is that quantum computing will significantly challenge current cryptographic systems, but ongoing advancements in post-quantum cryptography will mitigate the risk of obsolescence. Strategic actions should focus on accelerating research in post-quantum cryptography and preparing for potential cybersecurity threats posed by quantum advancements.
2. Competing Hypotheses
Hypothesis 1: Quantum computing will render current cryptographic systems obsolete, leading to widespread vulnerabilities in data security.
Hypothesis 2: While quantum computing poses a significant threat to current cryptographic systems, advancements in post-quantum cryptography will provide effective countermeasures, maintaining data security integrity.
Hypothesis 2 is more likely due to ongoing research and development in post-quantum cryptographic algorithms, which aim to preemptively address vulnerabilities before quantum computers become widely operational.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that quantum computers will become operational and accessible in the near future, and that current cryptographic systems will not be able to withstand quantum attacks without significant adaptation.
Red Flags: Over-reliance on the timeline for quantum computing advancements could lead to underestimating the urgency of developing post-quantum solutions. Additionally, there may be deception indicators if adversaries exaggerate their quantum capabilities to induce panic or mislead strategic planning.
4. Implications and Strategic Risks
The advent of quantum computing could lead to cascading threats in cybersecurity, with potential impacts on political, economic, and informational domains. Politically, nations may experience increased espionage risks. Economically, industries reliant on secure data transmission could face significant disruptions. Informationally, the integrity of sensitive data could be compromised, leading to a loss of public trust.
5. Recommendations and Outlook
- Actionable Steps: Invest in research and development of post-quantum cryptographic algorithms. Establish partnerships between government, academia, and industry to accelerate innovation. Conduct regular assessments of cryptographic infrastructure vulnerabilities.
- Best-case Scenario: Post-quantum cryptography is successfully implemented before quantum computers become operational, maintaining data security.
- Worst-case Scenario: Quantum computers become operational before effective cryptographic solutions are in place, leading to widespread data breaches.
- Most-likely Scenario: A transitional period where both vulnerabilities and solutions coexist, requiring adaptive strategies to manage risks.
6. Key Individuals and Entities
Rebecca Krauthamer, CEO of QuSecure; Britta Hale, Computer Scientist at Naval Postgraduate School; Michele Mosca, CEO of EvolutionQ.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·