Radware Cyber Survey Uncovers Critical Weaknesses in Application Security Measures – Vmblog.com
Published on: 2025-06-12
Intelligence Report: Radware Cyber Survey Uncovers Critical Weaknesses in Application Security Measures – Vmblog.com
1. BLUF (Bottom Line Up Front)
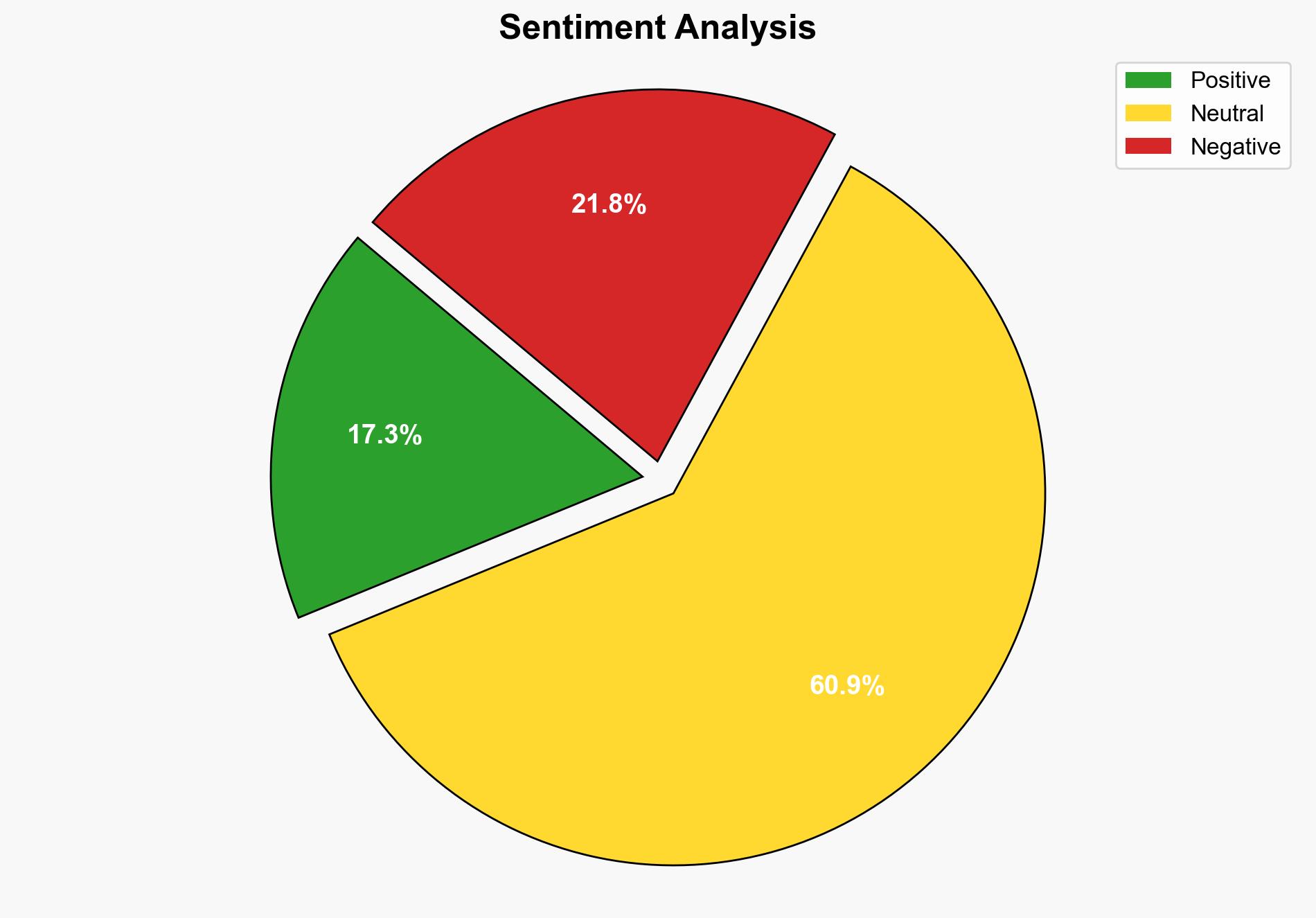
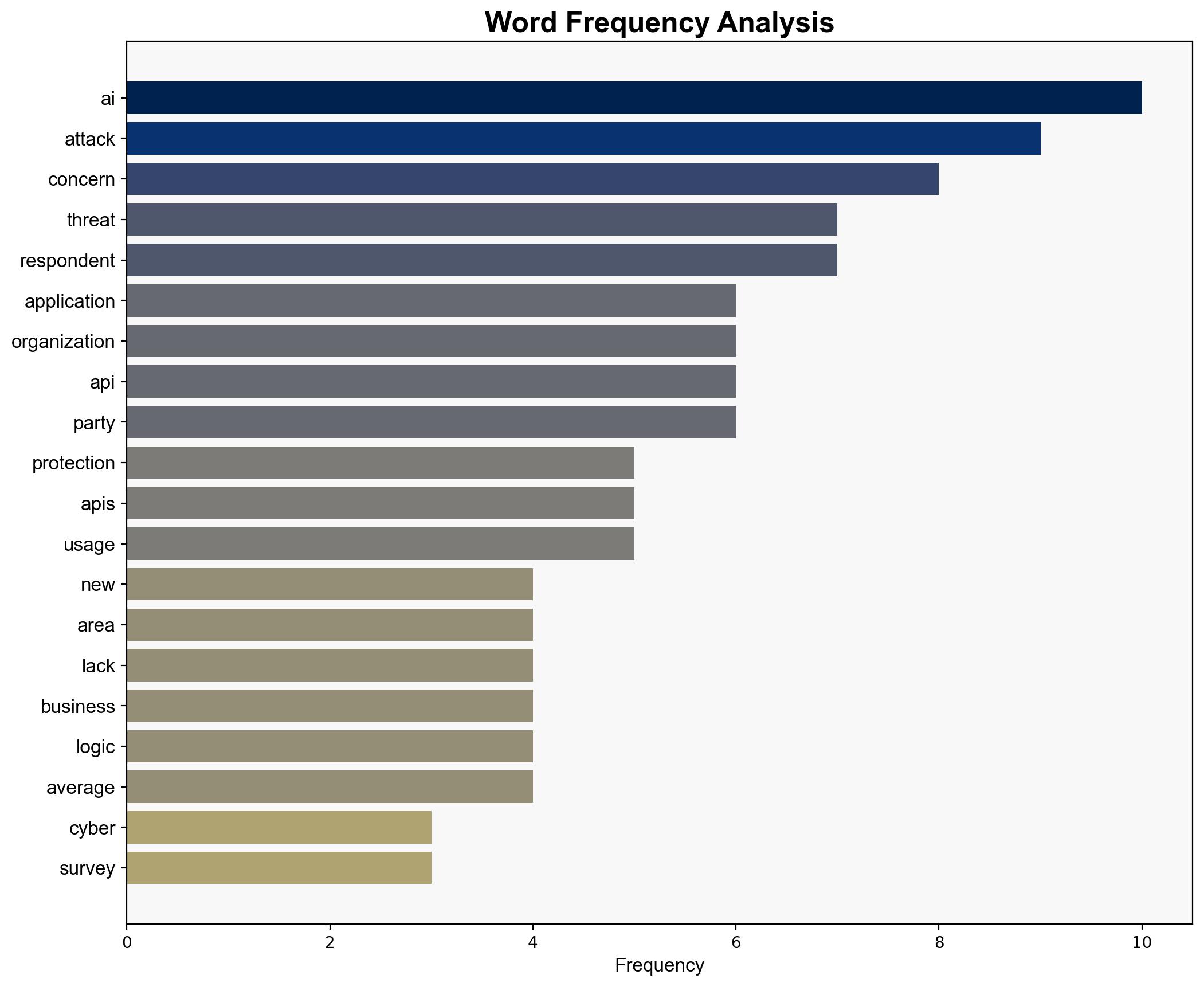
The Radware cyber survey highlights significant vulnerabilities in application security, particularly concerning AI threats, API security, and business logic attacks. Organizations are struggling to keep pace with evolving cyber threats, with a notable gap in readiness and protection measures. Immediate action is required to enhance AI-based defenses and improve API security protocols.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations reveal that cyber adversaries are increasingly leveraging AI to develop sophisticated attack tools, posing a significant threat to unprotected systems.
Indicators Development
Key indicators include rapid API updates and the proliferation of third-party services, which increase the risk of data breaches and require enhanced monitoring.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of AI-driven attacks bypassing traditional defenses, necessitating the adoption of advanced AI-based security solutions.
3. Implications and Strategic Risks
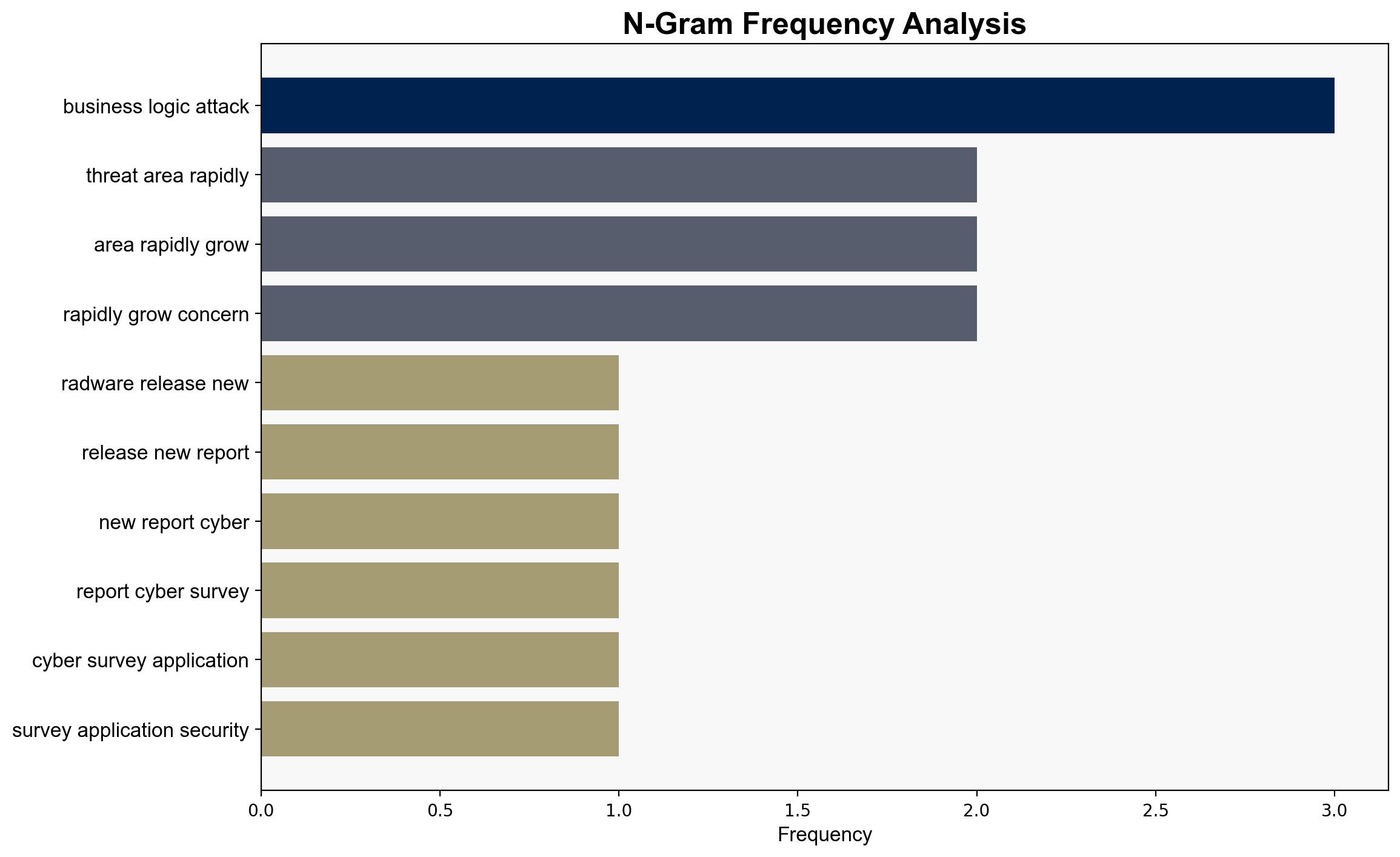
The survey underscores a growing concern over AI-enhanced cyber threats, which could lead to widespread data breaches and operational disruptions. The lack of preparedness in API security and business logic protection presents systemic vulnerabilities that could have cascading effects on national and economic security.
4. Recommendations and Outlook
- Implement AI-based cybersecurity solutions to counter AI-driven threats effectively.
- Enhance API security by deploying real-time protection measures and conducting regular security audits.
- Train security personnel to detect and mitigate business logic attacks promptly.
- Scenario-based projections indicate that without immediate action, organizations face increased risks of data breaches and regulatory non-compliance.
5. Key Individuals and Entities
Shira Sagiv
6. Thematic Tags
national security threats, cybersecurity, AI threats, API security, data breaches