Ransomware Attack Compromises Approximately 1,000 Systems at Romanian Water Management Agency
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Around 1000 systems compromised in ransomware attack on Romanian water agency
1. BLUF (Bottom Line Up Front)
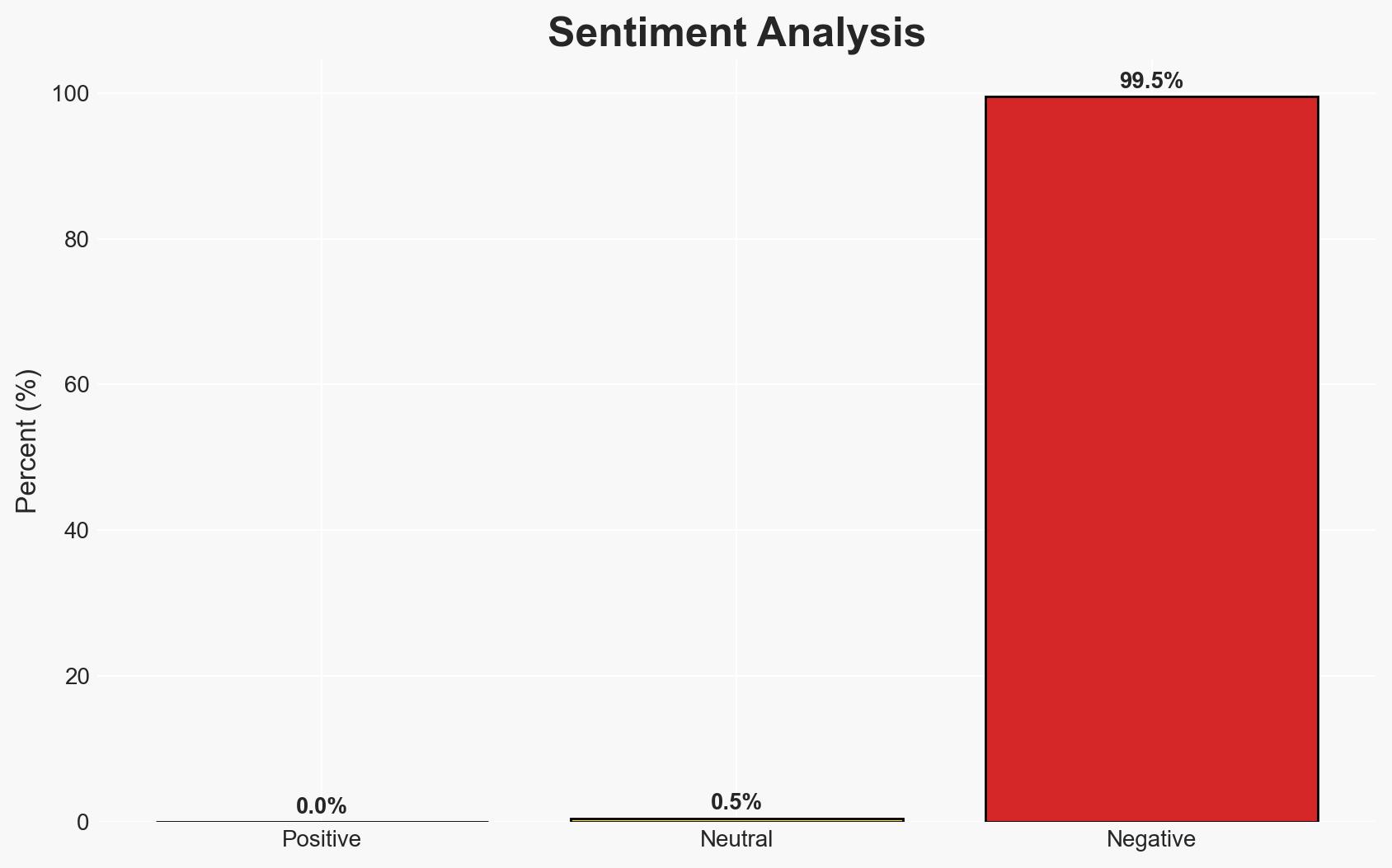
The ransomware attack on Romania’s water management administration compromised approximately 1,000 systems, impacting IT infrastructure but not operational capabilities. The attack exploited Windows’ BitLocker, suggesting a potentially unsophisticated actor. The incident highlights vulnerabilities in critical infrastructure protection. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was conducted by a financially motivated cybercriminal group using opportunistic methods. Supporting evidence includes the use of ransom notes and encryption, typical of financially motivated attacks. However, the lack of a known ransomware group’s signature payload introduces uncertainty.
- Hypothesis B: The attack was executed by a less sophisticated actor or an insider exploiting known vulnerabilities in the system. The use of BitLocker, a common tool, supports this hypothesis, but the scale of the attack suggests some level of coordination and capability.
- Assessment: Hypothesis A is currently better supported due to the presence of ransom notes and encryption demands, which align with typical ransomware motivations. Future identification of the group or specific tactics could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attack was financially motivated; Romanian Waters’ operational capabilities remain unaffected; the attackers are not linked to a known sophisticated ransomware group.
- Information Gaps: Identity of the attackers; specific vulnerabilities exploited; full extent of data compromised.
- Bias & Deception Risks: Potential underestimation of the attacker’s sophistication; reliance on publicly available statements which may omit sensitive details.
4. Implications and Strategic Risks
This incident underscores the vulnerability of critical infrastructure to cyberattacks and may prompt increased scrutiny and investment in cybersecurity measures. The attack could influence policy changes and international cooperation on cyber defense.
- Political / Geopolitical: Potential for increased governmental focus on cybersecurity legislation and international collaboration.
- Security / Counter-Terrorism: Heightened alertness for similar attacks on critical infrastructure; potential reevaluation of threat models.
- Cyber / Information Space: Increased emphasis on integrating critical infrastructure into national cybersecurity frameworks.
- Economic / Social: Limited immediate economic impact, but potential long-term costs associated with enhanced security measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation to identify the attackers and vulnerabilities; enhance monitoring of critical infrastructure systems.
- Medium-Term Posture (1–12 months): Integrate Romanian Waters into national cybersecurity frameworks; develop public-private partnerships for improved cyber resilience.
- Scenario Outlook:
- Best: Attackers are identified and neutralized, leading to improved cybersecurity measures.
- Worst: Further attacks on critical infrastructure occur, causing operational disruptions.
- Most-Likely: Incremental improvements in cybersecurity posture, with ongoing threat of similar attacks.
6. Key Individuals and Entities
- Administrația Națională Apele Române (Romanian Waters)
- Romanian National Cyber Security Directorate (DNSC)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, critical infrastructure, national security, cybercrime, information security, public-private partnership
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us