Ransomware Attack Disrupts Romanian Water Authority, Compromising 1,000 Systems
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Romanian water authority hit by ransomware attack over weekend
1. BLUF (Bottom Line Up Front)
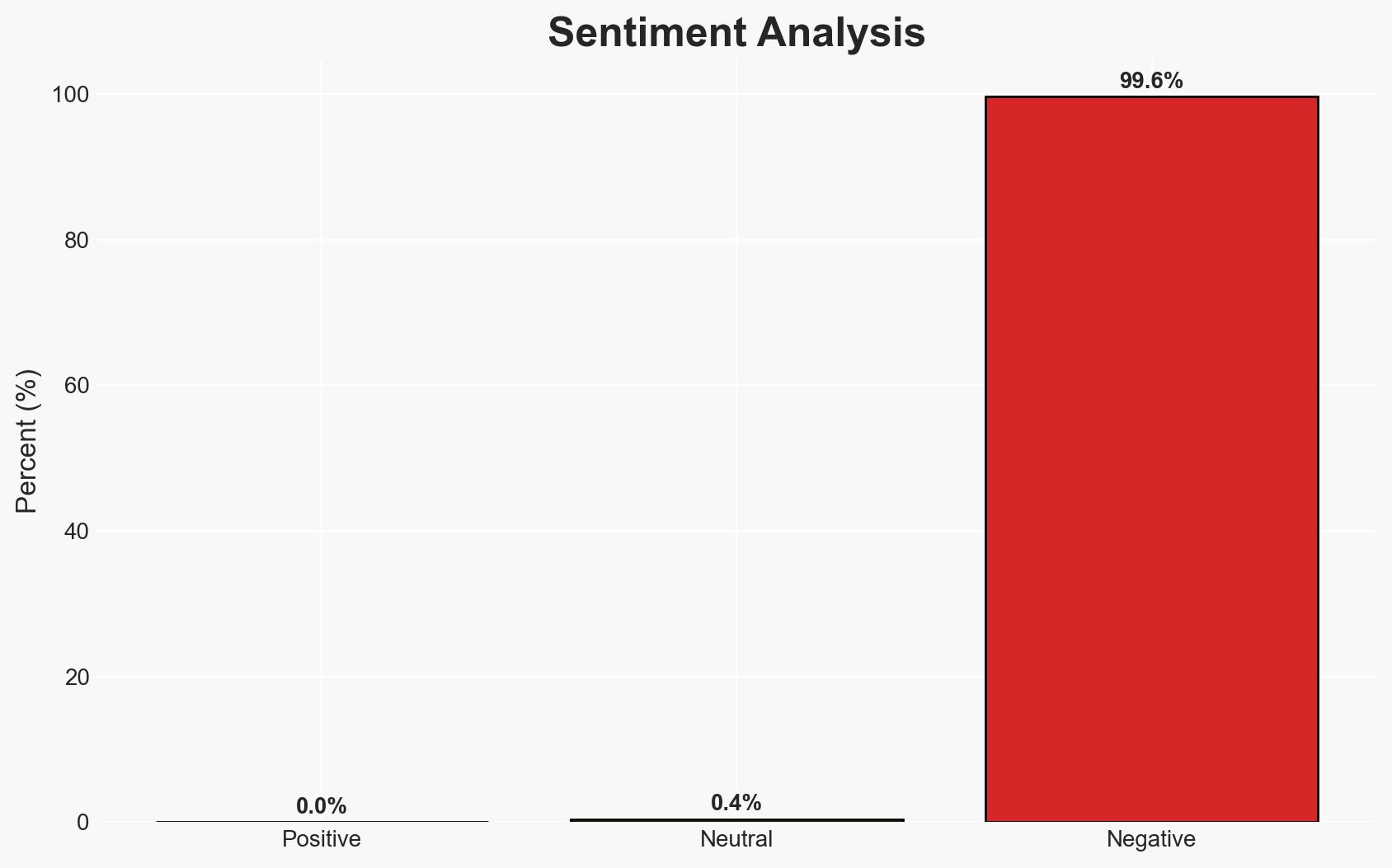
The Romanian water management authority, Romanian Waters, experienced a ransomware attack affecting approximately 1,000 computer systems. While operational technology systems remain unaffected, the attack highlights vulnerabilities in critical infrastructure. The incident is currently unattributed, with moderate confidence in the assessment that pro-Russian hacktivist groups may be involved, given recent warnings and geopolitical tensions.
2. Competing Hypotheses
- Hypothesis A: The attack was conducted by a financially motivated cybercriminal group using ransomware to extort money. This is supported by the use of BitLocker to lock files and demand a ransom. However, the lack of immediate attribution or ransom payment details introduces uncertainty.
- Hypothesis B: The attack was orchestrated by pro-Russian hacktivist groups targeting critical infrastructure as part of a broader geopolitical strategy. This aligns with recent warnings from international cybersecurity agencies and the geopolitical context involving Russia. The absence of a claim of responsibility is a contradicting factor.
- Assessment: Hypothesis B is currently better supported due to the geopolitical context and recent warnings about pro-Russian groups targeting infrastructure. Indicators such as attribution by authorities or a claim of responsibility could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attack’s primary motive is financial or geopolitical disruption; Romanian Waters’ critical operations remain unaffected; the attackers have not yet been identified.
- Information Gaps: Specific attack vector details, identity of the attackers, and whether any ransom was paid or negotiations occurred.
- Bias & Deception Risks: Potential bias towards attributing attacks to geopolitical adversaries; deception risk from attackers using false flags to mislead attribution efforts.
4. Implications and Strategic Risks
This ransomware attack underscores vulnerabilities in critical infrastructure and may prompt increased cybersecurity measures. The incident could exacerbate geopolitical tensions and influence future cyber defense strategies.
- Political / Geopolitical: Potential escalation in cyber hostilities between Romania and adversarial states, particularly Russia.
- Security / Counter-Terrorism: Increased threat to critical infrastructure, necessitating enhanced security protocols and collaboration with international partners.
- Cyber / Information Space: Heightened focus on cybersecurity resilience and potential for increased cyber operations targeting similar infrastructure.
- Economic / Social: Limited immediate economic impact, but potential long-term implications for public trust in infrastructure security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure, conduct a thorough forensic investigation, and increase collaboration with international cybersecurity entities.
- Medium-Term Posture (1–12 months): Develop resilience measures, integrate national cybersecurity systems, and strengthen partnerships with allied countries to deter future attacks.
- Scenario Outlook: Best: Attack attributed and mitigated with no further incidents. Worst: Escalation of cyberattacks on critical infrastructure. Most-Likely: Continued probing of vulnerabilities with sporadic incidents.
6. Key Individuals and Entities
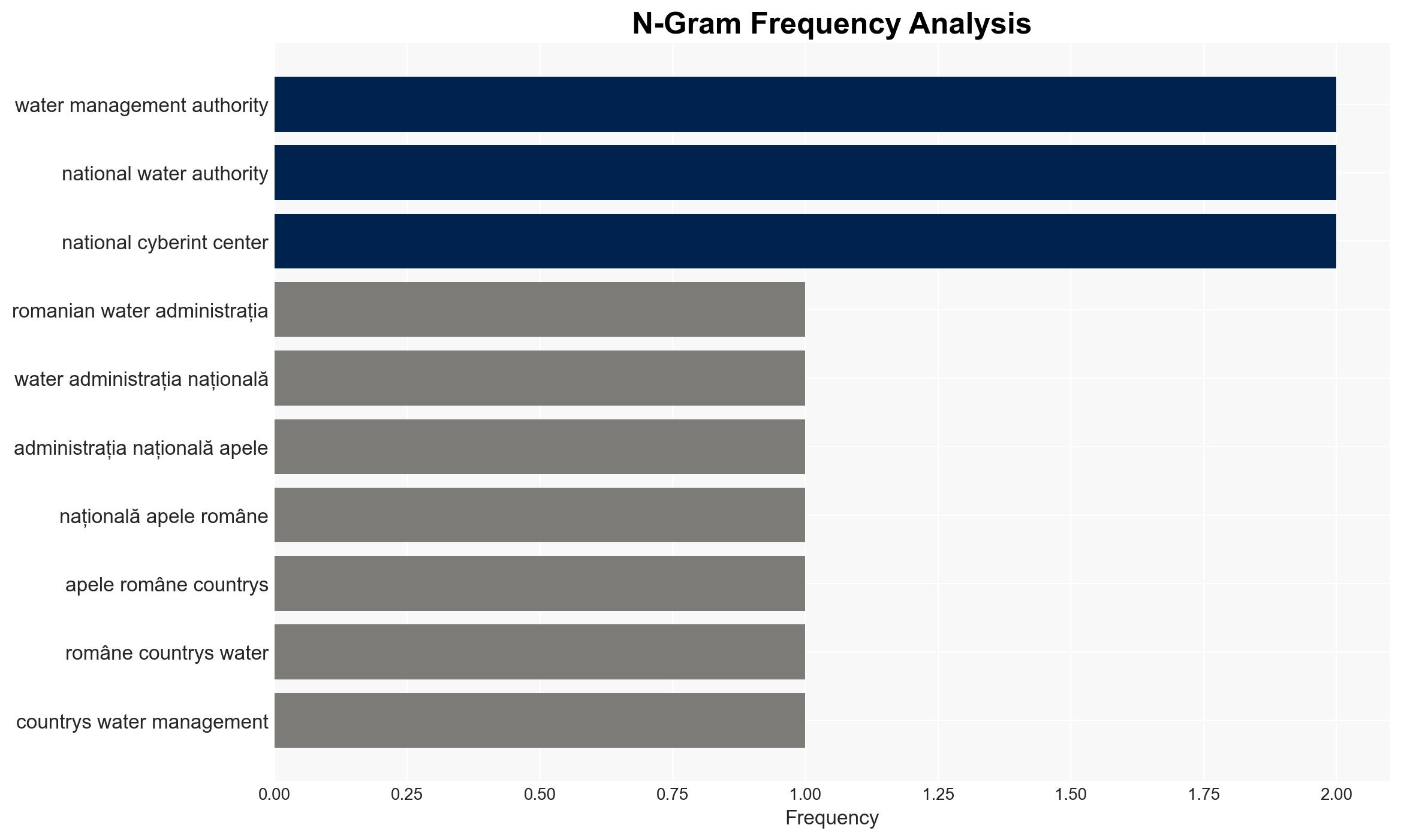
- Romanian Waters (Administrația Națională Apele Române)
- National Cyber Security Directorate (DNSC)
- Romanian Intelligence Service’s National Cyberint Center
- Pro-Russian hacktivist groups (e.g., Z-Pentest, Sector16, NoName, CARR)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
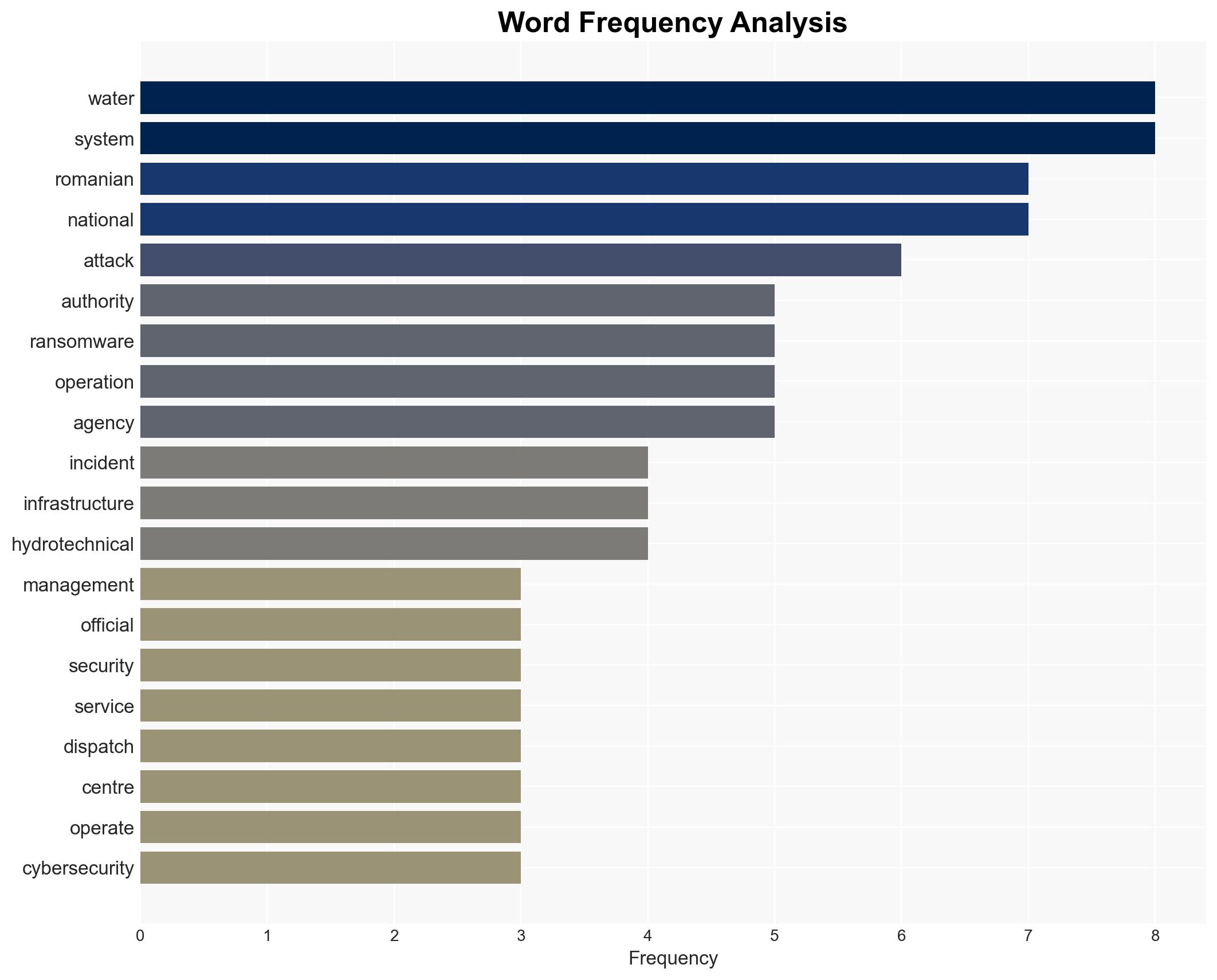
cybersecurity, ransomware, critical infrastructure, cyber security, geopolitical tensions, pro-Russian hacktivists, national security, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us