Ransomware Attack on Romanian Waters Affects IT Systems, But Water Operations Remain Uninterrupted
Published on: 2025-12-22
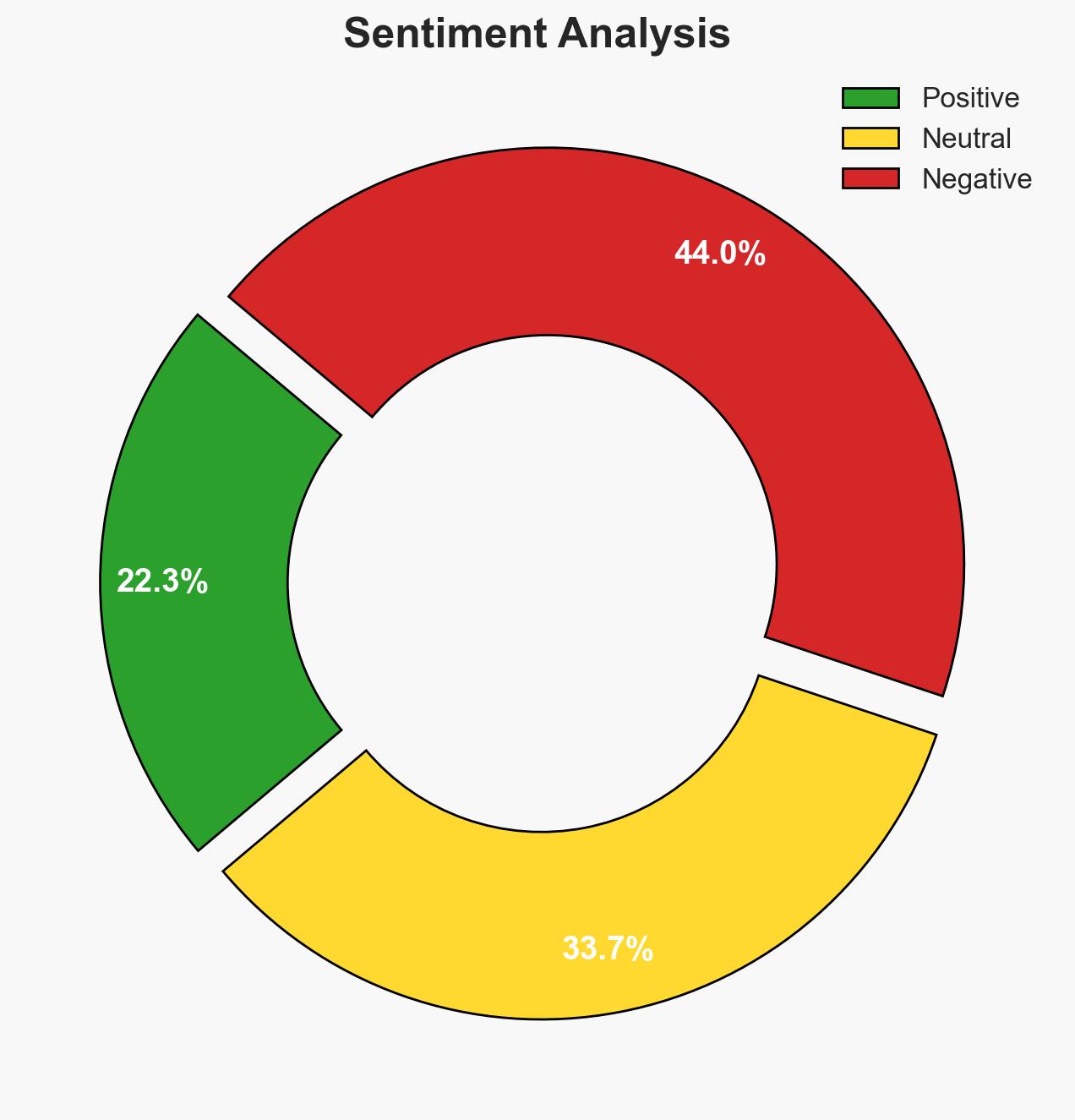
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Romanian Waters confirms cyberattack critical water operations unaffected
1. BLUF (Bottom Line Up Front)
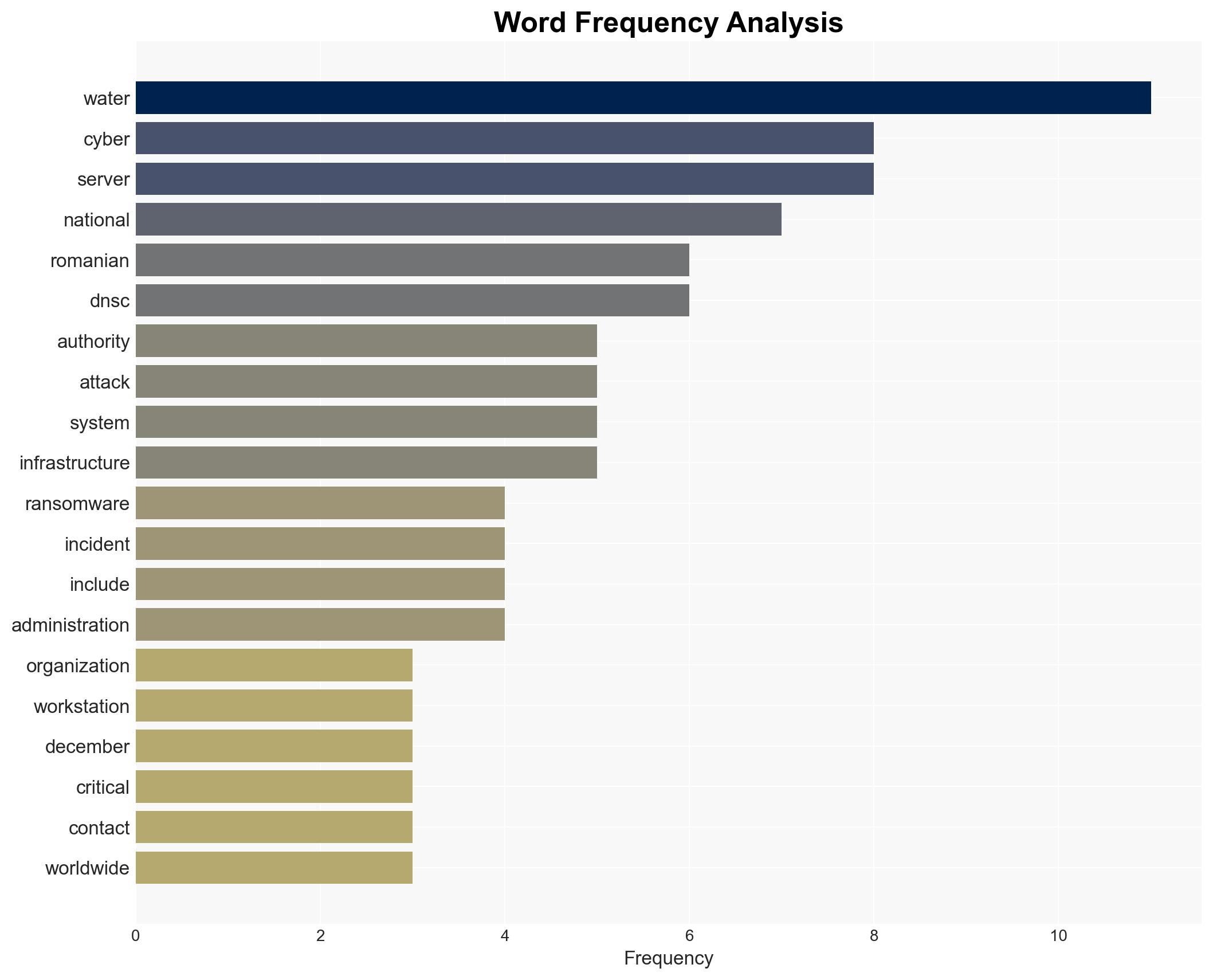
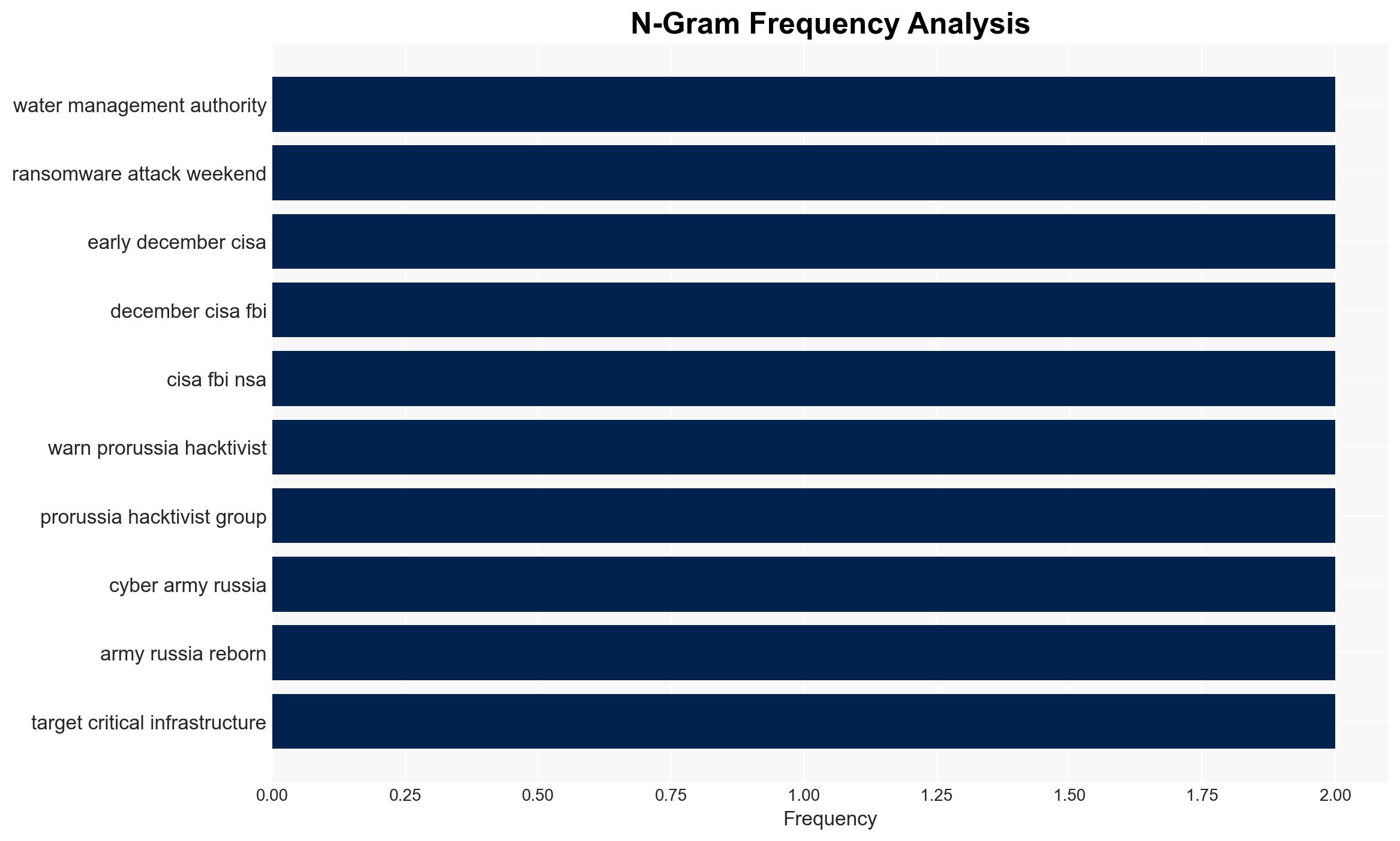
The Romanian Waters authority experienced a ransomware attack affecting IT systems, but operational water infrastructure remains unaffected. The attack compromised approximately 1,000 systems, including GIS and email servers. The most likely hypothesis is that this attack was opportunistic rather than targeted, with moderate confidence due to the lack of identified threat actors and attack vectors.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack was opportunistic, targeting Romanian Waters due to vulnerabilities in their IT systems. This is supported by the lack of a specific attack vector and the absence of direct claims of responsibility. Key uncertainties include the motivation and identity of the attackers.
- Hypothesis B: The attack was a targeted operation by pro-Russian hacktivist groups aiming to disrupt Romanian critical infrastructure. This is contradicted by the absence of direct impact on operational technology systems and no specific claims of responsibility from known groups.
- Assessment: Hypothesis A is currently better supported due to the lack of specific indicators pointing to a targeted attack. Indicators that could shift this judgment include the emergence of claims of responsibility or evidence of targeted reconnaissance activities.
3. Key Assumptions and Red Flags
- Assumptions: The attack was not specifically aimed at disrupting water operations; Romanian Waters’ IT systems had exploitable vulnerabilities; No insider threat was involved.
- Information Gaps: The specific attack vector and identity of the attackers remain unknown; the extent of data exfiltration, if any, is unclear.
- Bias & Deception Risks: There is a risk of confirmation bias in attributing the attack to opportunistic actors without concrete evidence; potential for deceptive claims by threat actors to mislead investigators.
4. Implications and Strategic Risks
This incident underscores vulnerabilities in critical infrastructure IT systems and highlights the need for enhanced cybersecurity measures. The situation could evolve with further attacks or demands from the threat actors.
- Political / Geopolitical: Potential for increased tensions if linked to state-sponsored actors; could influence Romania’s cybersecurity policy and international cooperation.
- Security / Counter-Terrorism: Raises awareness of cyber threats to critical infrastructure, necessitating improved defensive measures.
- Cyber / Information Space: Highlights the importance of integrating critical infrastructure into national cyber defense systems; potential for increased cyber operations targeting similar vulnerabilities.
- Economic / Social: Minimal immediate economic impact, but long-term risks if water infrastructure becomes a target; public confidence in infrastructure security may be affected.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Romanian Waters’ IT systems, expedite integration into national cyber defense platforms, and conduct a thorough forensic investigation to identify attack vectors.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular security audits and staff training; strengthen partnerships with international cybersecurity agencies.
- Scenario Outlook:
- Best: Attack remains isolated with no further incidents; vulnerabilities are patched.
- Worst: Further attacks occur, affecting operational systems and causing disruptions.
- Most-Likely: Continued opportunistic attacks on similar vulnerabilities; gradual improvement in cybersecurity posture.
6. Key Individuals and Entities
- Romanian Waters (Administrația Națională Apele Române)
- National Cyber Security Directorate (DNSC)
- SRI’s National Cyberint Center
- Pro-Russian hacktivist groups (e.g., Z-Pentest, Sector16, NoName, Cyber Army of Russia Reborn)
7. Thematic Tags
cybersecurity, ransomware, critical infrastructure, national security, cyber defense, water management, threat actors
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us