Ransomware gang leaks data on 10000 WASHPOST employees contractors – San.com
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware gang leaks data on 10000 WASHPOST employees contractors – San.com
1. BLUF (Bottom Line Up Front)
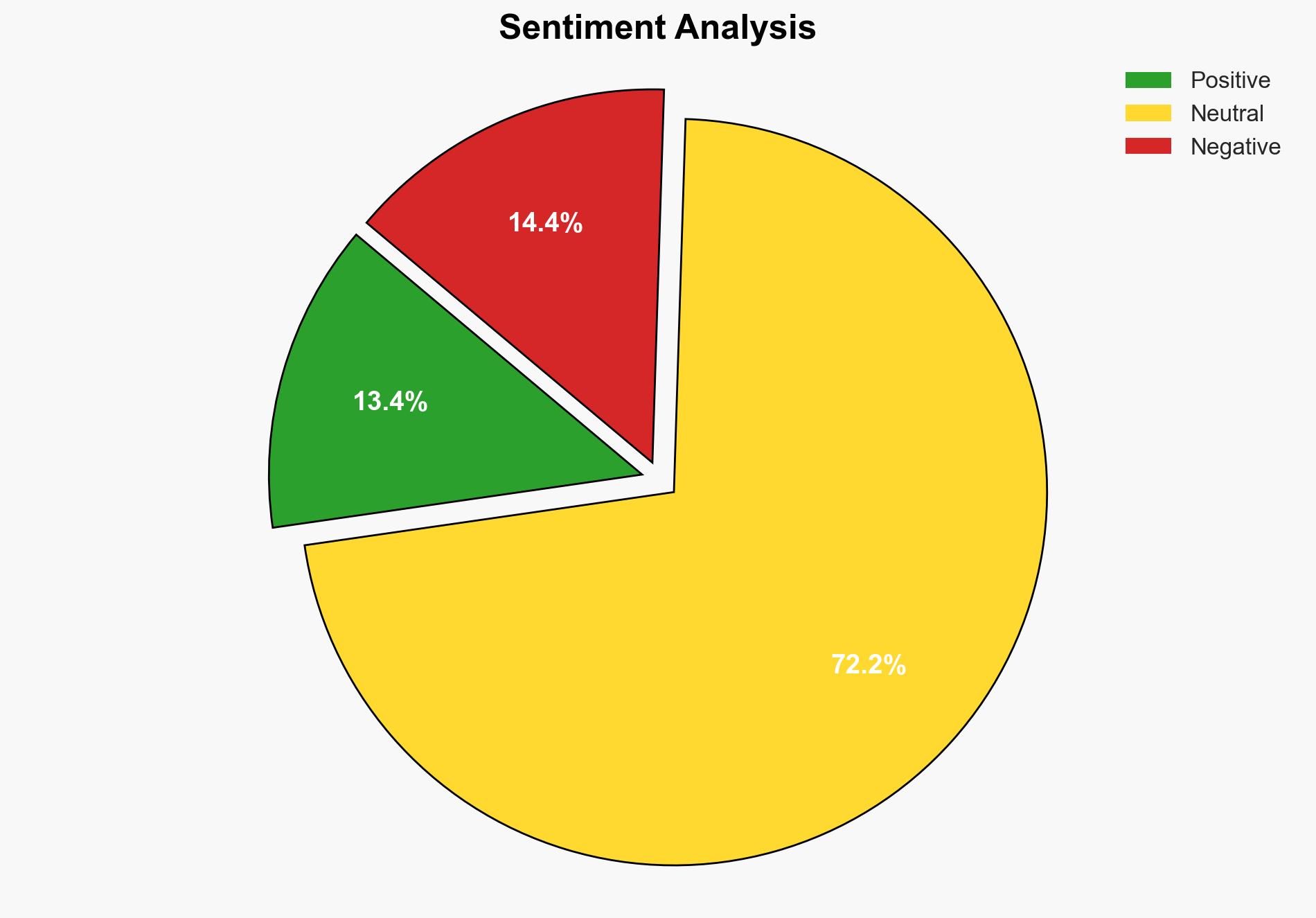
The most supported hypothesis is that the Russian-speaking ransomware gang, Clop, executed a targeted cyberattack exploiting a vulnerability in Oracle’s software to obtain sensitive data from The Washington Post. This poses significant risks to personal privacy and national security. Confidence Level: Moderate. Recommended actions include enhancing cybersecurity measures and engaging in diplomatic channels to address potential state-sponsored cyber threats.
2. Competing Hypotheses
Hypothesis 1: The Clop ransomware gang independently targeted The Washington Post using a vulnerability in Oracle’s software to steal and leak data for financial gain.
Hypothesis 2: The attack was state-sponsored, with Clop acting as a proxy for a nation-state, aiming to gather intelligence and disrupt U.S. media operations.
Hypothesis 1 is more likely due to Clop’s known modus operandi of financially motivated attacks. However, the involvement of high-profile individuals like John Bolton suggests potential geopolitical motives, lending some credence to Hypothesis 2.
3. Key Assumptions and Red Flags
Assumptions: Clop is acting independently without state sponsorship; the vulnerability in Oracle’s software was previously unknown to all parties.
Red Flags: The targeting of high-profile individuals with national security implications; lack of direct communication from Clop post-attack.
Deception Indicators: Potential misinformation regarding the extent of data compromised or the true perpetrators of the attack.
4. Implications and Strategic Risks
The breach could lead to identity theft, financial fraud, and exploitation of sensitive information. Politically, it may escalate tensions between the U.S. and Russia if state sponsorship is suspected. Economically, it could undermine trust in Oracle’s software, affecting its market position. Informationally, it risks undermining the credibility and operational security of The Washington Post.
5. Recommendations and Outlook
- Enhance cybersecurity protocols at The Washington Post and similar entities, focusing on software vulnerabilities.
- Engage in international dialogue to address cyber threats and establish norms against targeting media outlets.
- Monitor Clop’s activities and communications for further insights into their motivations and potential state affiliations.
- Best-case scenario: The breach is contained, and no further sensitive information is exploited.
- Worst-case scenario: The breach leads to significant national security threats and deteriorates international relations.
- Most-likely scenario: The breach results in financial and reputational damage, prompting increased cybersecurity measures.
6. Key Individuals and Entities
John Bolton, Fareed Zakaria, Joe Scarborough, Malcolm Nance
7. Thematic Tags
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Structured challenge to expose and correct biases.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us
·