Ransomware Group Trinity of Chaos Launches Data Leak Site – Infosecurity Magazine
Published on: 2025-10-06
Intelligence Report: Ransomware Group Trinity of Chaos Launches Data Leak Site – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
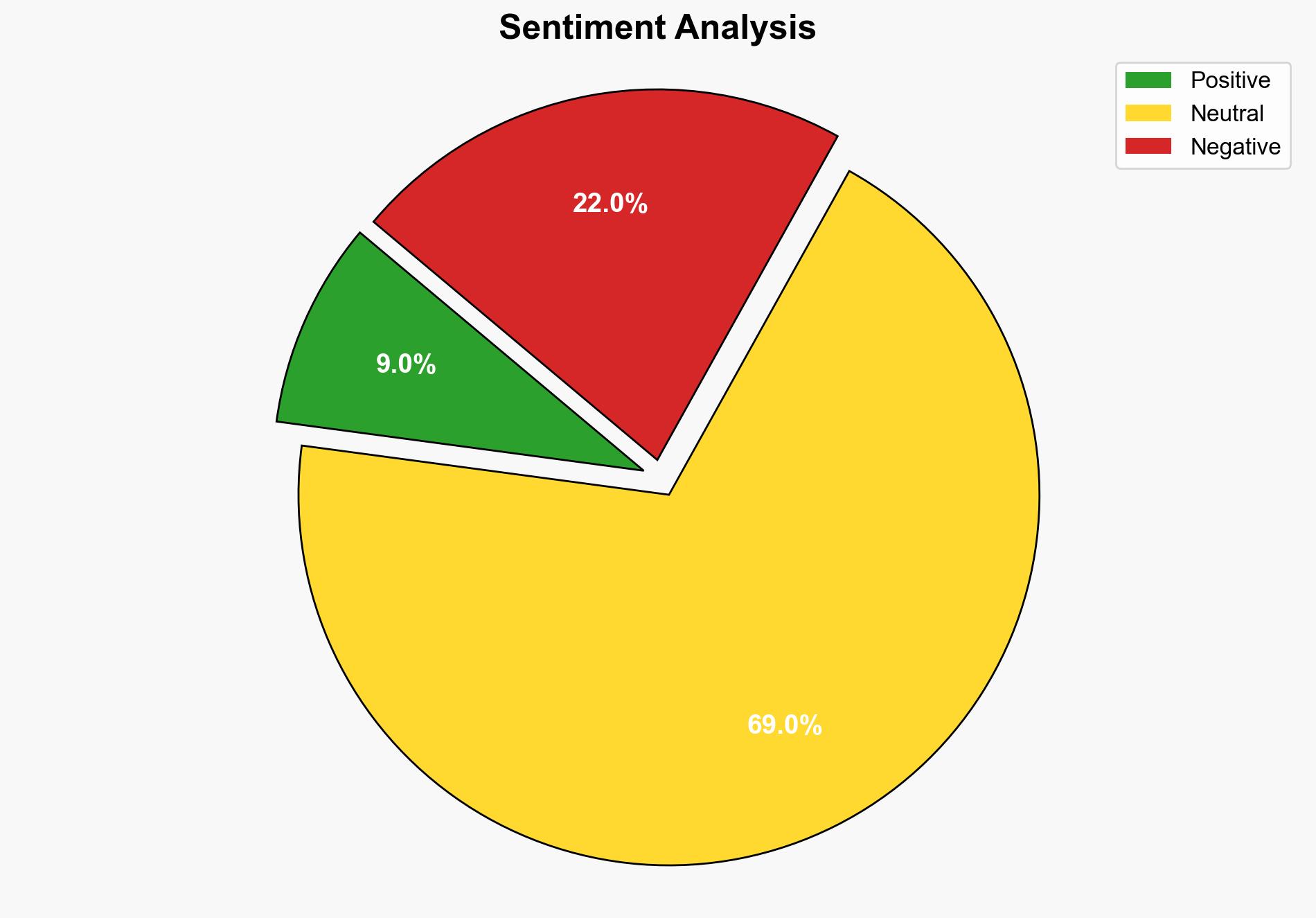
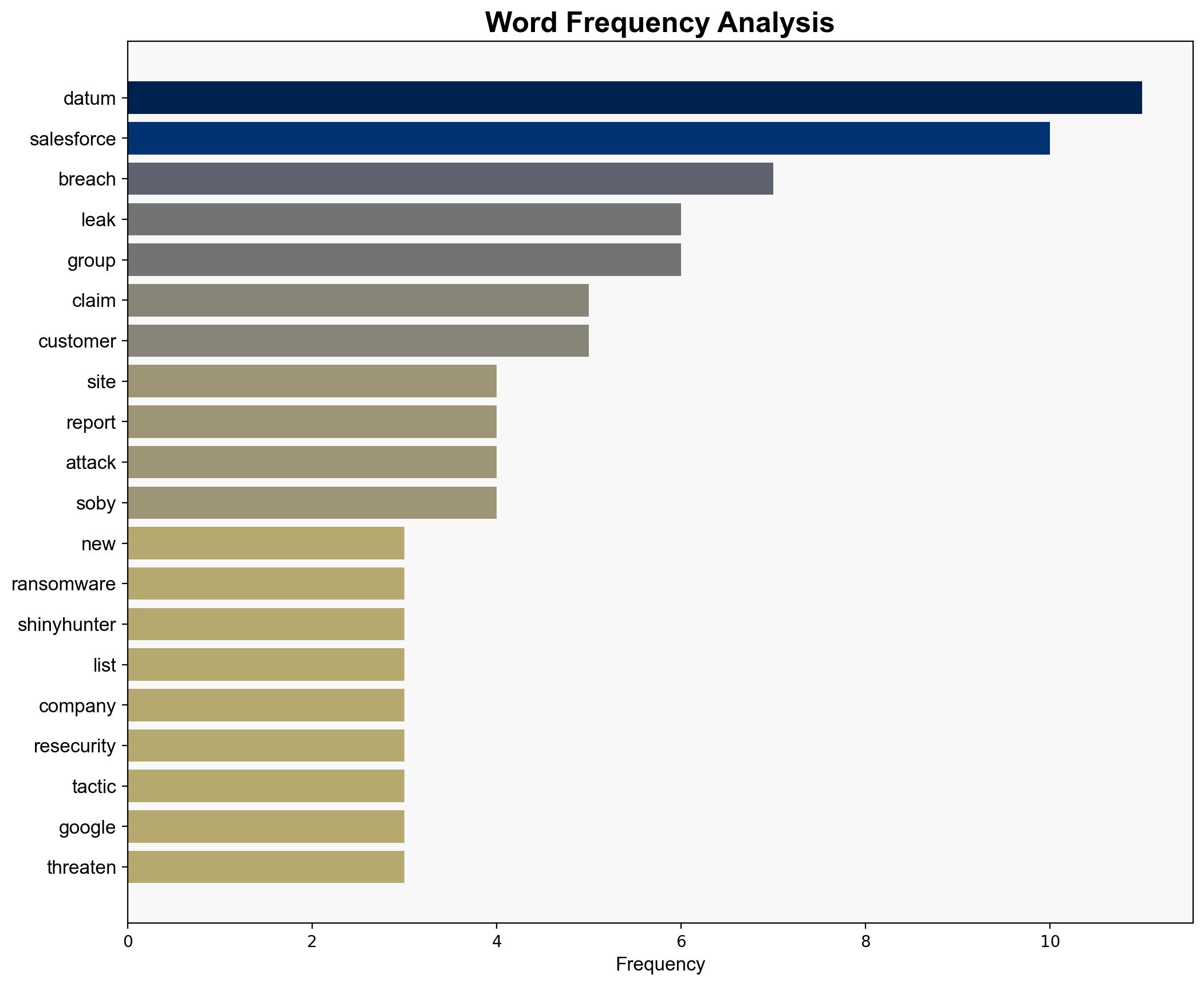
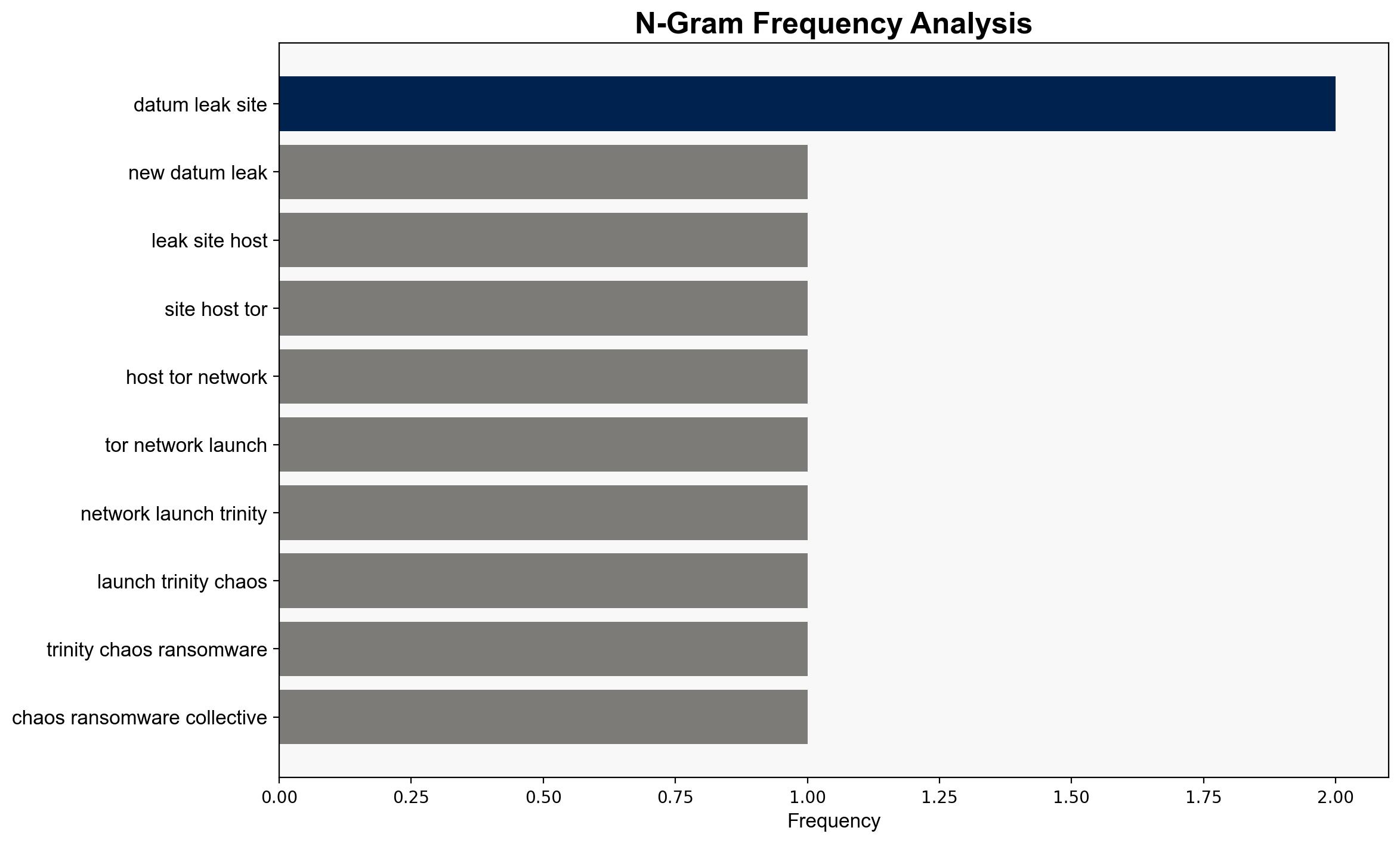
The Trinity of Chaos ransomware group has escalated its operations by launching a data leak site on the Tor network, potentially linked to other known cybercriminal groups. The most supported hypothesis is that this move is a strategic escalation to increase pressure on victim companies, leveraging regulatory threats. Confidence level: Moderate. Recommended action: Enhance cybersecurity measures and prepare for potential regulatory scrutiny.
2. Competing Hypotheses
Hypothesis 1: Trinity of Chaos is primarily focused on financial gain through extortion, using the data leak site as a tool to increase pressure on companies to pay ransoms by threatening regulatory consequences.
Hypothesis 2: The group aims to destabilize targeted companies and industries, potentially serving broader geopolitical or competitive interests, beyond immediate financial gain.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the group’s direct threats to Salesforce and the use of regulatory pressure tactics, which are consistent with financially motivated ransomware operations.
3. Key Assumptions and Red Flags
Assumptions:
– The group has the capability to exploit vulnerabilities and access sensitive data.
– Regulatory threats are effective in coercing companies to comply with ransom demands.
Red Flags:
– Lack of concrete evidence linking Trinity of Chaos to other groups like Lapsus$ or ShinyHunter.
– Potential misinformation or exaggeration of data possession claims.
4. Implications and Strategic Risks
The escalation of ransomware tactics poses significant risks to corporate data integrity and regulatory compliance. The potential for large-scale phishing and identity theft could have widespread economic and reputational impacts. There is also a risk of geopolitical tensions if state actors are involved or if critical infrastructure is targeted.
5. Recommendations and Outlook
- Strengthen cybersecurity defenses, focusing on vulnerability management and incident response capabilities.
- Engage with legal and regulatory experts to prepare for potential compliance challenges.
- Scenario Projections:
- Best Case: Companies successfully thwart attacks and enhance security postures, minimizing impact.
- Worst Case: Widespread data breaches lead to significant financial losses and regulatory penalties.
- Most Likely: Continued ransomware attempts with varying success, prompting increased security investments.
6. Key Individuals and Entities
Brian Soby, noted for his insights on the group’s tactics and the shared responsibility model in cybersecurity.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus