Ransomware groups exploit ISPsystem’s virtual machines for covert malware distribution
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware gang uses ISPsystem VMs for stealthy payload delivery
1. BLUF (Bottom Line Up Front)
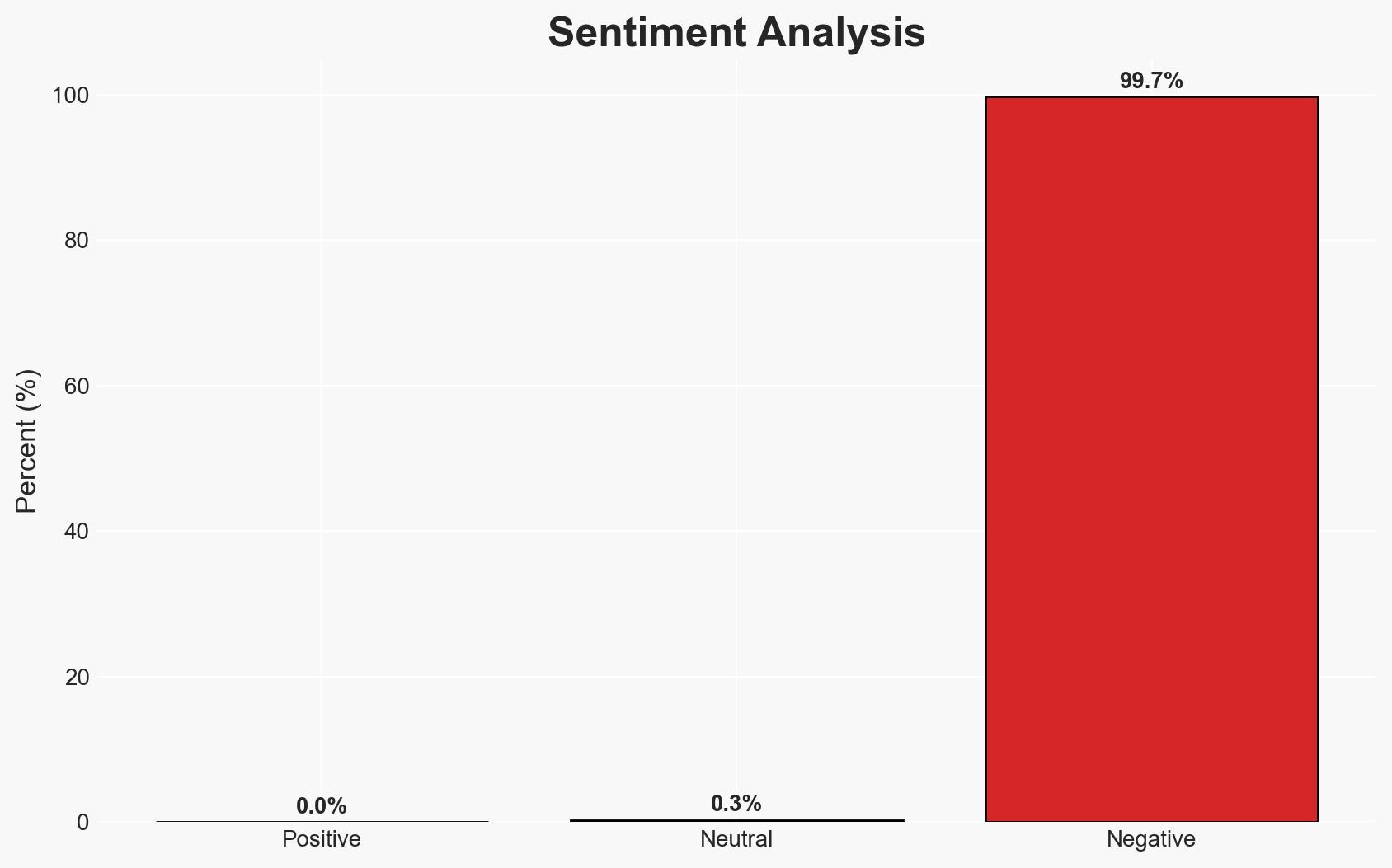
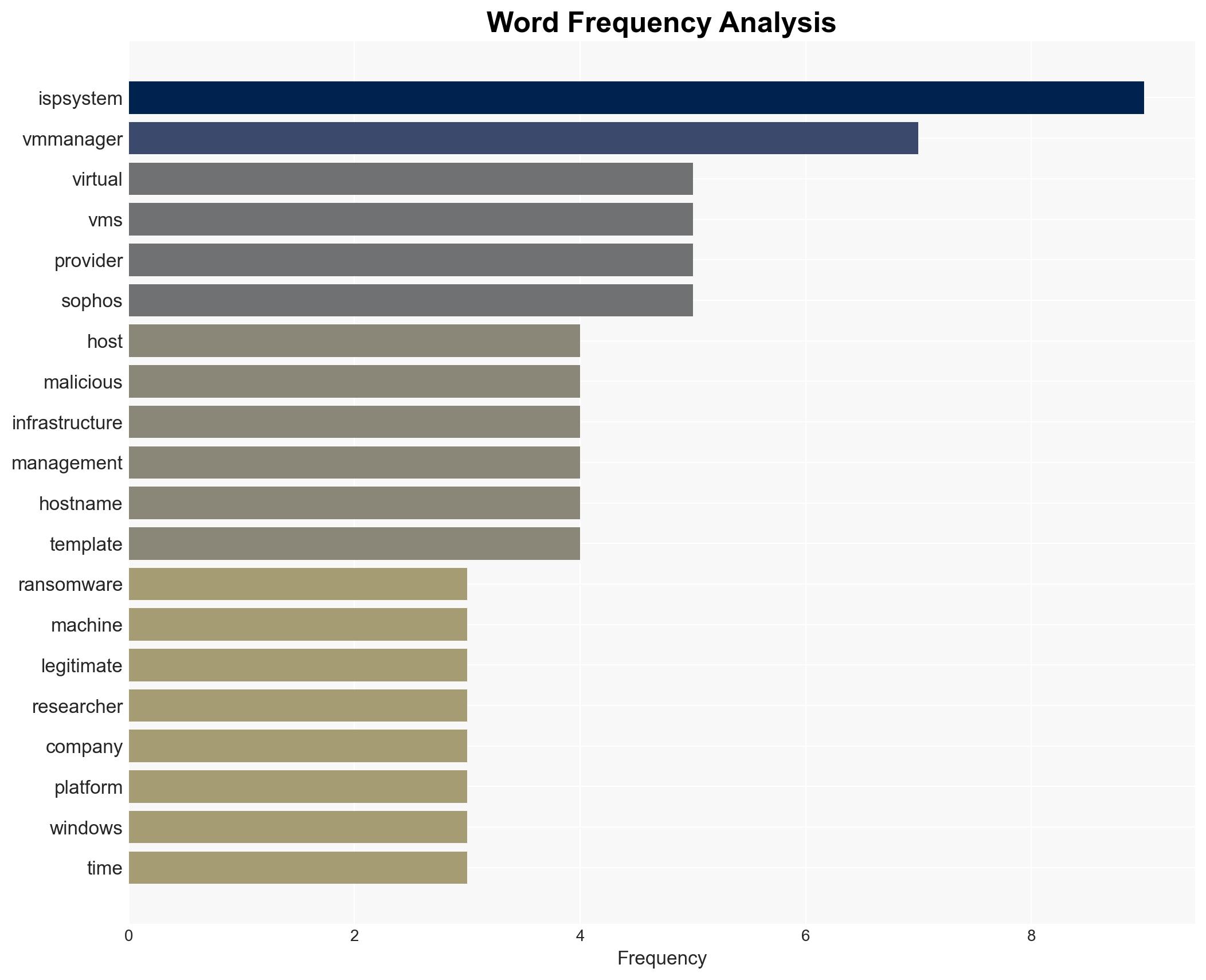
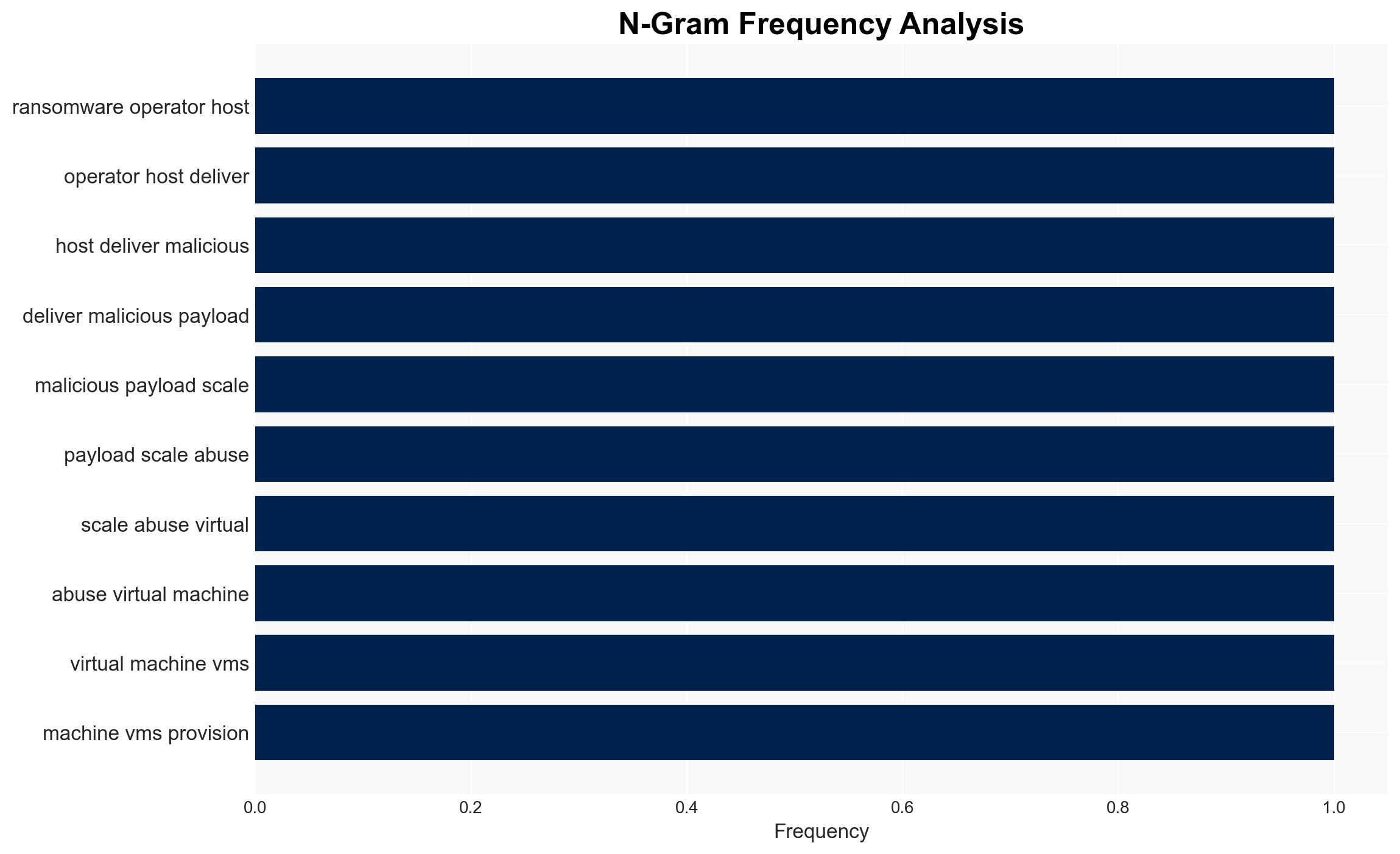
Ransomware operators are exploiting ISPsystem’s VMmanager platform to deploy malicious payloads, complicating attribution and takedown efforts. This tactic is primarily affecting cybersecurity defenses and increasing the operational capabilities of multiple ransomware groups. Overall, there is moderate confidence in the assessment that this exploitation will persist unless mitigated by ISPsystem and hosting providers.
2. Competing Hypotheses
- Hypothesis A: Ransomware groups are deliberately exploiting ISPsystem’s VMmanager due to its low cost and ease of use, leveraging default templates to evade detection. This is supported by the observed use of identical hostnames and system identifiers. However, the extent of ISPsystem’s awareness and response remains uncertain.
- Hypothesis B: The exploitation of ISPsystem’s VMmanager is incidental, with cybercriminals opportunistically using any available platform that offers anonymity and low barriers to entry. This hypothesis is less supported due to the specific evidence of repeated hostname usage and the involvement of known bulletproof hosting providers.
- Assessment: Hypothesis A is currently better supported due to the specific targeting of ISPsystem’s VMmanager by multiple ransomware groups and the observed patterns in VM deployment. Indicators such as changes in ISPsystem’s platform security measures could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Cybercriminals prioritize platforms with low detection risk; ISPsystem is unaware or unable to fully address the exploitation; bulletproof hosting providers will continue to ignore takedown requests.
- Information Gaps: The full extent of ISPsystem’s internal response and any ongoing mitigation strategies; the specific technical details of how VMs are being configured and deployed by cybercriminals.
- Bias & Deception Risks: Potential bias in source reporting from cybersecurity firms with vested interests; possible deception by cybercriminals to mislead attribution efforts.
4. Implications and Strategic Risks
This development could lead to increased sophistication in ransomware operations, complicating international cybersecurity efforts and potentially escalating geopolitical tensions if state actors are implicated.
- Political / Geopolitical: Potential for increased international pressure on countries hosting non-compliant providers.
- Security / Counter-Terrorism: Enhanced capabilities for ransomware groups could lead to more frequent and severe attacks on critical infrastructure.
- Cyber / Information Space: Increased difficulty in attribution and takedown of malicious infrastructure, leading to prolonged cyber threats.
- Economic / Social: Potential economic impacts from disrupted services and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Engage with ISPsystem to understand their mitigation strategies; increase monitoring of known bulletproof hosting providers.
- Medium-Term Posture (1–12 months): Develop partnerships with international cybersecurity agencies to enhance information sharing; invest in advanced detection technologies.
- Scenario Outlook:
- Best: ISPsystem implements effective countermeasures, reducing exploitation (trigger: announcement of new security features).
- Worst: Increased ransomware attacks on critical infrastructure (trigger: significant attack attributed to VMmanager exploitation).
- Most-Likely: Continued exploitation with gradual improvements in detection and response (trigger: ongoing reports of similar incidents).
6. Key Individuals and Entities
- ISPsystem
- Sophos
- Stark Industries Solutions Ltd.
- Zomro B.V.
- First Server Limited
- Partner Hosting LTD
- JSC IOT
- MasterRDP
- LockBit, Qilin, Conti, BlackCat/ALPHV, Ursnif
7. Thematic Tags
cybersecurity, ransomware, virtual machines, bulletproof hosting, cybercrime, ISPsystem, attribution challenges
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us