Ransomware Groups Target VMware ESXi Vulnerability in Ongoing Exploitation Campaign
Published on: 2026-02-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA VMware ESXi flaw now exploited in ransomware attacks
1. BLUF (Bottom Line Up Front)
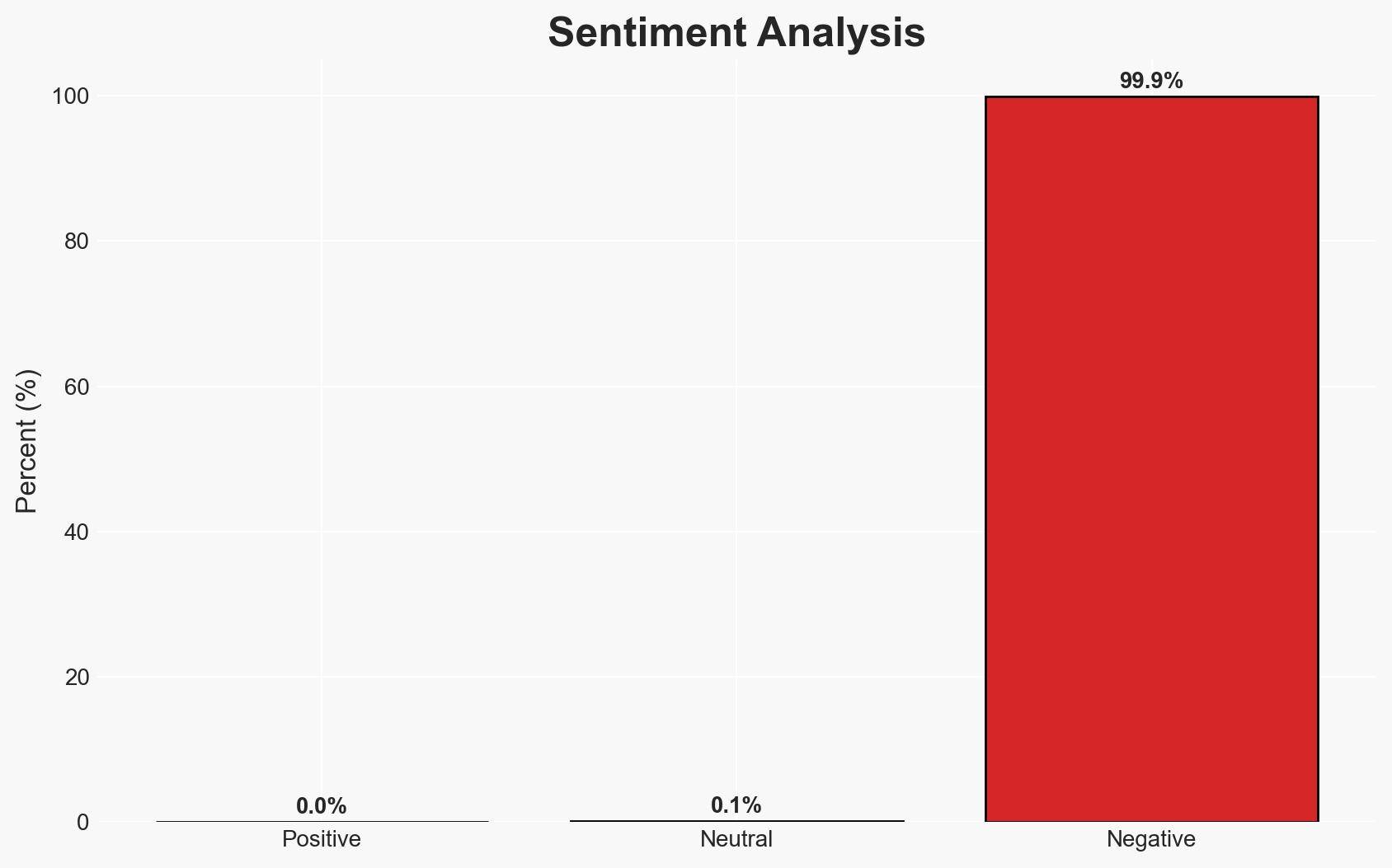
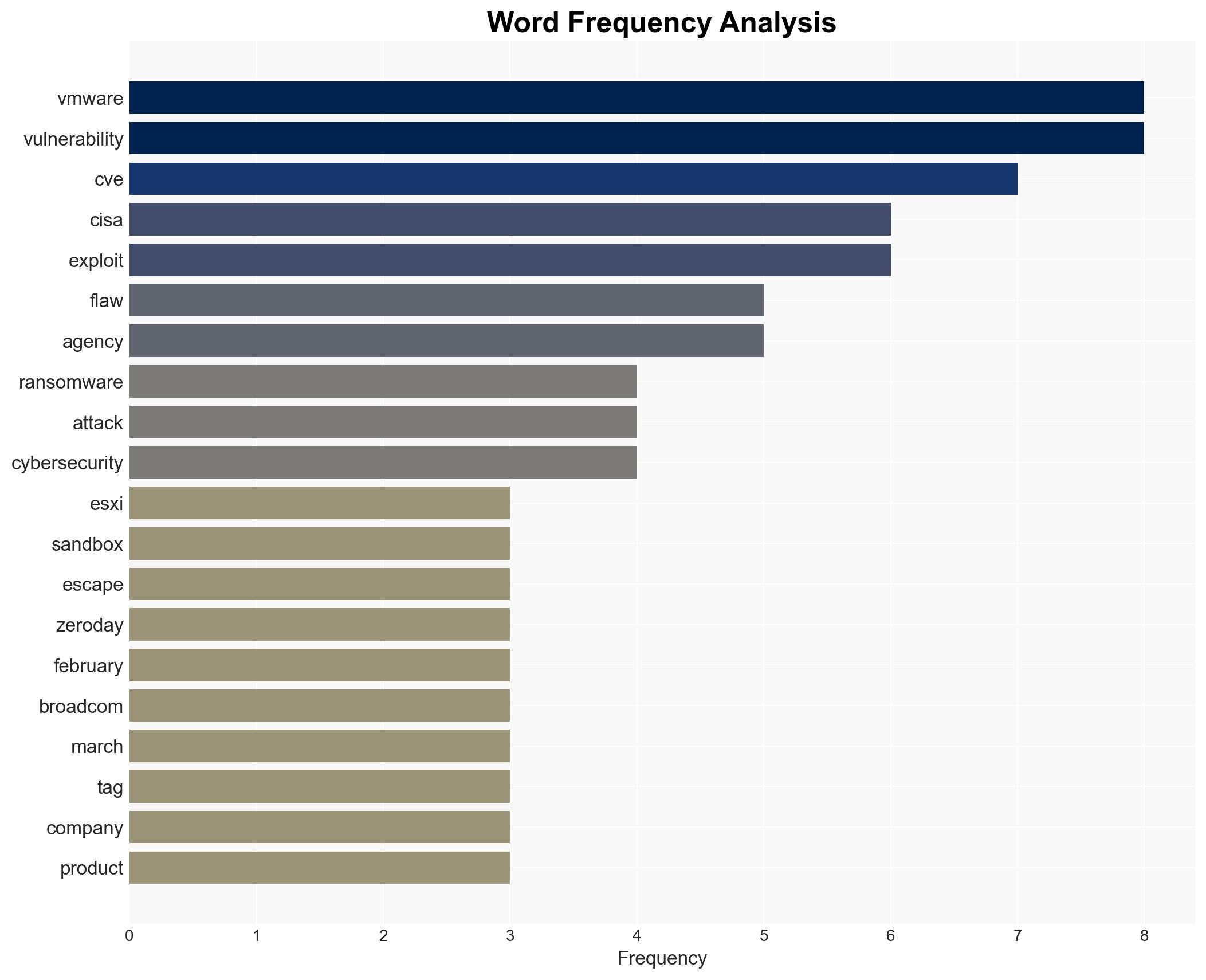
Ransomware gangs are exploiting a high-severity VMware ESXi vulnerability (CVE-2025-22225) in ongoing attacks, posing significant risks to organizations using VMware products. This development highlights persistent threats from both criminal and state-sponsored actors targeting widely deployed enterprise systems. Overall confidence in this assessment is moderate due to limited specific details on the current campaigns.
2. Competing Hypotheses
- Hypothesis A: Ransomware gangs are primarily exploiting the VMware ESXi vulnerability independently of state-sponsored actors. This is supported by the general trend of ransomware groups targeting enterprise vulnerabilities for financial gain. However, the lack of detailed attribution data limits certainty.
- Hypothesis B: State-sponsored actors, potentially from China, are coordinating with ransomware gangs to exploit the VMware ESXi vulnerability for both espionage and financial purposes. This is suggested by historical patterns of Chinese-speaking threat actors exploiting similar vulnerabilities. Contradictory evidence includes the absence of explicit attribution to state actors in current reports.
- Assessment: Hypothesis A is currently better supported due to the typical modus operandi of ransomware gangs focusing on financial exploitation. Key indicators that could shift this judgment include credible attribution to state actors or evidence of coordinated campaigns.
3. Key Assumptions and Red Flags
- Assumptions: VMware products remain widely deployed in enterprise environments; ransomware gangs have the capability to exploit the vulnerability; CISA’s advisories are based on credible threat intelligence.
- Information Gaps: Specific details on the ransomware campaigns exploiting the vulnerability; clear attribution of actors involved; technical specifics on how the vulnerability is being exploited in the wild.
- Bias & Deception Risks: Potential bias in attributing attacks to Chinese-speaking actors without explicit evidence; risk of underestimating the involvement of state-sponsored actors due to lack of public data.
4. Implications and Strategic Risks
The exploitation of the VMware ESXi vulnerability could lead to increased ransomware incidents, impacting critical infrastructure and enterprise operations. This situation may exacerbate geopolitical tensions if state-sponsored involvement is confirmed.
- Political / Geopolitical: Potential strain on international relations if state-sponsored involvement is verified, particularly involving China.
- Security / Counter-Terrorism: Heightened threat environment for organizations using VMware products, necessitating increased cybersecurity measures.
- Cyber / Information Space: Possible escalation in cyber operations targeting enterprise systems, with implications for data integrity and confidentiality.
- Economic / Social: Potential economic disruptions due to ransomware attacks on critical business operations, affecting market stability and consumer confidence.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should apply available patches, follow CISA and vendor mitigation guidelines, and enhance monitoring for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular security audits and incident response planning, and strengthen partnerships with cybersecurity firms for threat intelligence sharing.
- Scenario Outlook: Best: Vulnerability exploitation is contained through effective patching. Worst: Escalation in attacks with confirmed state-sponsored involvement. Most-Likely: Continued ransomware exploitation with sporadic state actor involvement, contingent on geopolitical developments.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, state-sponsored threats, VMware vulnerabilities, enterprise security, CISA advisories, cyber-espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us