Ransomware Threats Shift Focus: Identity Becomes the Central Security Challenge for Organizations
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Identity the new perimeter of ransomware defence
1. BLUF (Bottom Line Up Front)
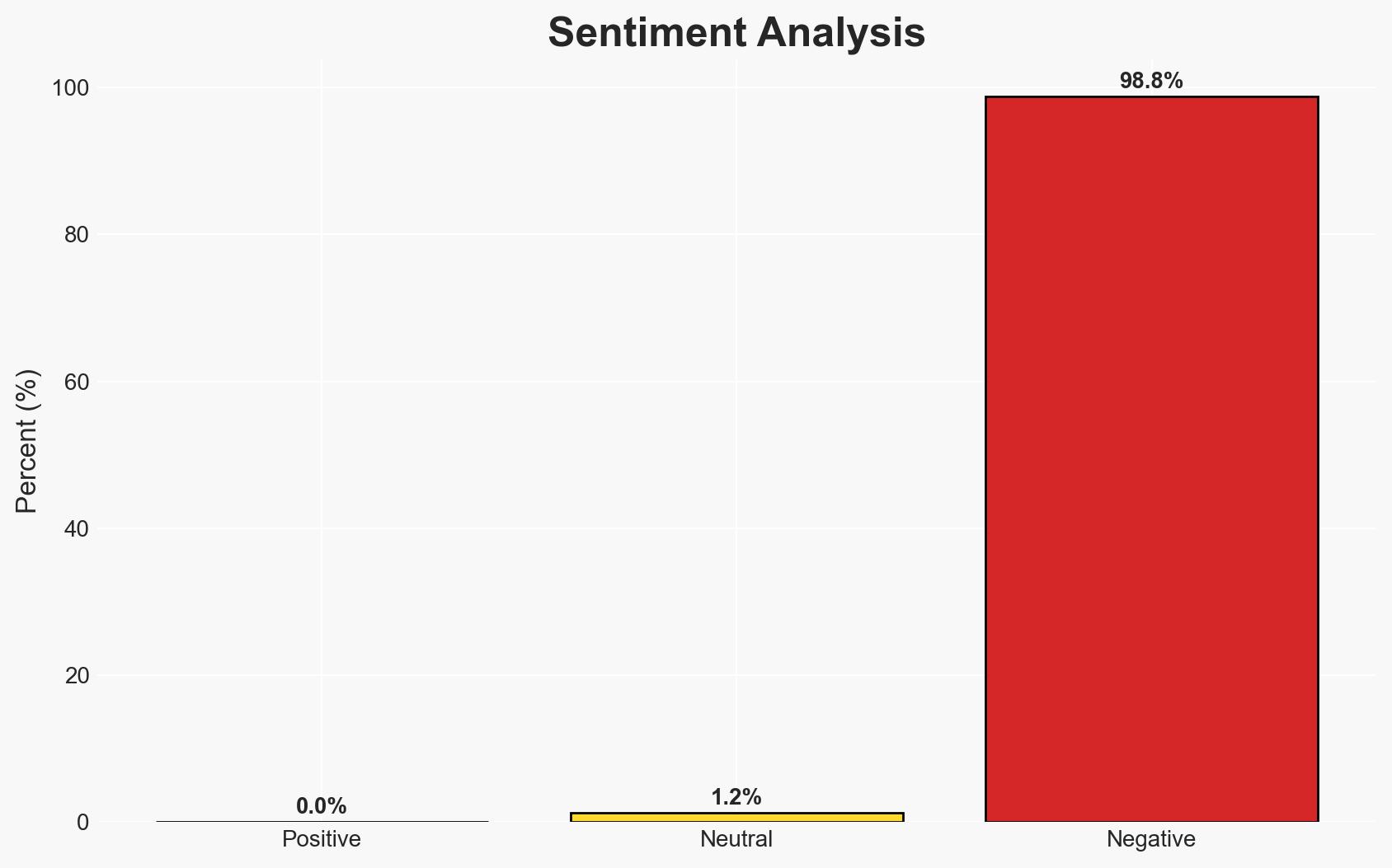
Ransomware attacks have evolved to exploit identity and social engineering, posing significant strategic risks to organizations across multiple sectors. The most likely hypothesis is that identity security will become the primary focus of cybersecurity strategies, requiring board-level oversight and investment. This assessment is made with moderate confidence, given the current evidence and trends.
2. Competing Hypotheses
- Hypothesis A: Ransomware groups will increasingly focus on identity abuse and social engineering as primary attack vectors, bypassing traditional technical defenses. This is supported by the shift in tactics observed in groups like Scattered Spider, which use voice phishing to gain legitimate access to systems. However, the extent of this trend across all ransomware groups remains uncertain.
- Hypothesis B: Ransomware groups will continue to rely on a combination of identity abuse and traditional malware-based attacks. While identity abuse is becoming more prevalent, the continued use of malware and exploits suggests a hybrid approach may persist. Evidence for this includes ongoing reports of malware-based intrusions alongside identity-focused attacks.
- Assessment: Hypothesis A is currently better supported due to the increasing frequency and success of identity-focused attacks, as well as the significant impact on organizations. Key indicators that could shift this judgment include a resurgence in malware-based attacks or new defensive measures effectively countering identity abuse.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will prioritize identity security; Ransomware groups will continue to innovate in social engineering; Boards will recognize the strategic importance of cybersecurity.
- Information Gaps: Detailed data on the prevalence of identity-focused attacks across different sectors; Effectiveness of current defensive measures against these tactics.
- Bias & Deception Risks: Potential over-reliance on reports from sectors heavily impacted by identity abuse; Confirmation bias towards the effectiveness of identity-based defenses.
4. Implications and Strategic Risks
The evolution of ransomware tactics towards identity abuse could reshape cybersecurity priorities and strategies. This development may lead to increased regulatory scrutiny and demand for comprehensive identity management solutions.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity standards and identity protection frameworks.
- Security / Counter-Terrorism: Enhanced focus on insider threats and social engineering as key components of security strategies.
- Cyber / Information Space: Shift towards identity-centric security models and increased investment in identity verification technologies.
- Economic / Social: Potential economic impact due to increased cybersecurity spending and reputational damage from breaches.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Strengthen help desk verification processes, implement phishing-resistant authentication methods, and conduct employee awareness training.
- Medium-Term Posture (1–12 months): Develop a comprehensive identity management strategy, invest in threat intelligence capabilities, and foster cross-organizational cybersecurity collaboration.
- Scenario Outlook:
- Best Case: Effective identity security measures reduce the impact of ransomware attacks.
- Worst Case: Continued identity abuse leads to widespread breaches and significant economic losses.
- Most Likely: Gradual improvement in identity security, with periodic high-profile breaches prompting further investment and policy changes.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
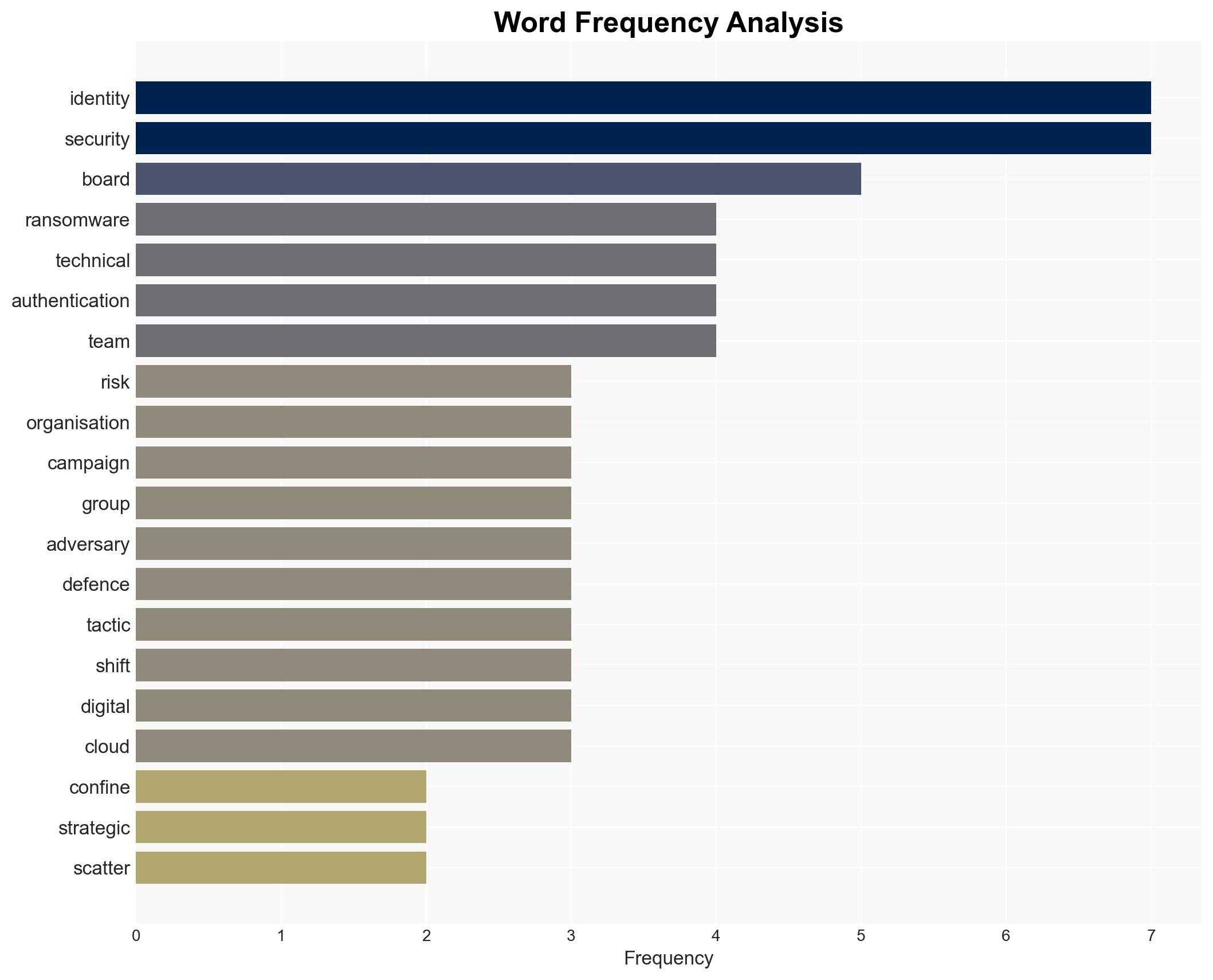
cybersecurity, ransomware, identity security, social engineering, cybersecurity strategy, board oversight, digital transformation, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us