Redis patches 13-Year-Old Lua flaw enabling Remote Code Execution – Securityaffairs.com
Published on: 2025-10-08
Intelligence Report: Redis patches 13-Year-Old Lua flaw enabling Remote Code Execution – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
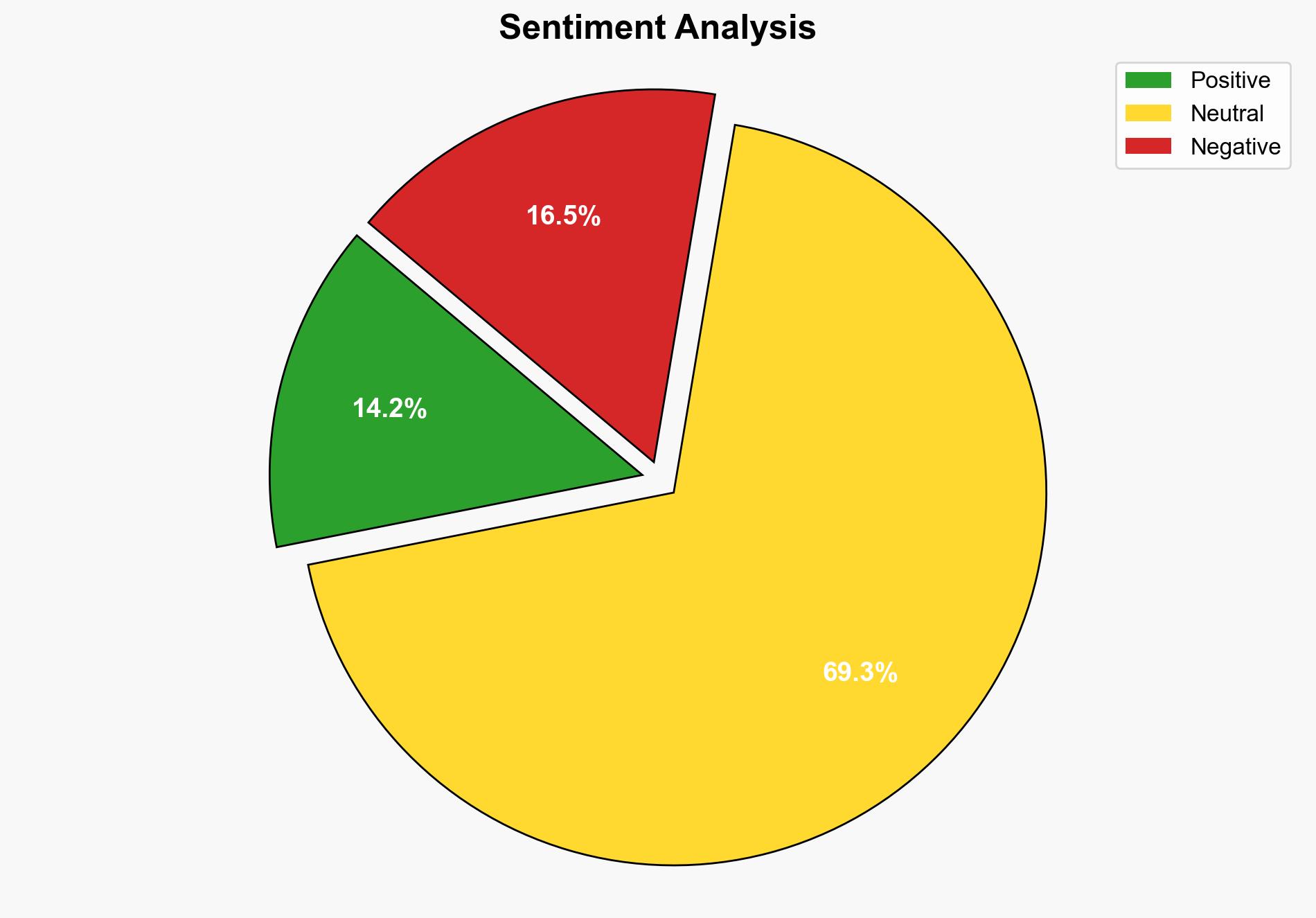
The discovery and patching of a 13-year-old vulnerability in Redis, identified as CVE, presents a critical cybersecurity risk, particularly for cloud environments. The most supported hypothesis is that this vulnerability could be actively exploited by threat actors to gain unauthorized access and execute arbitrary code, leading to potential data breaches and lateral movement within networks. Confidence level: High. Recommended action: Immediate patching of affected Redis instances and implementation of strong authentication measures.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is actively being exploited by cybercriminals to gain unauthorized access to systems, primarily targeting cloud environments due to their extensive exposure and valuable data.
Hypothesis 2: The vulnerability, while critical, is not yet widely exploited due to the requirement of prior authentication, limiting its immediate impact.
Using Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported due to the critical nature of the vulnerability, its potential for remote code execution, and the extensive exposure of Redis instances in cloud environments. The CVSS score and the detailed attack chain described further support the likelihood of active exploitation.
3. Key Assumptions and Red Flags
Assumptions include the belief that threat actors have the capability and intent to exploit this vulnerability. A potential red flag is the reliance on the CVSS score as the sole indicator of threat severity. The assumption that all Redis instances are equally vulnerable may overlook variations in security posture and configurations.
4. Implications and Strategic Risks
The vulnerability poses significant risks, including unauthorized access, data exfiltration, and potential disruption of services. The exploitation of this flaw could lead to broader cyber incidents, affecting economic stability and organizational trust. Geopolitically, state-sponsored actors could leverage this vulnerability for espionage or sabotage.
5. Recommendations and Outlook
- Organizations should immediately apply the Redis patch and ensure strong authentication measures are in place.
- Conduct a thorough audit of exposed Redis instances and restrict unnecessary internet exposure.
- Scenario-based projections:
- Best Case: Rapid patch deployment mitigates risk with minimal exploitation incidents.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most Likely: Targeted attacks occur, primarily affecting organizations with poor security postures.
6. Key Individuals and Entities
Wiz (cybersecurity firm that discovered the vulnerability) is a key entity involved in the identification and reporting of this flaw.
7. Thematic Tags
national security threats, cybersecurity, cloud security, data protection