Researchers at Pwn2Own Automotive Uncover 76 Zero-Day Vulnerabilities, Awarded Over $1 Million in Prizes
Published on: 2026-01-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pwn2Own Researchers Earn 1 Million for 76 Zero-Days
1. BLUF (Bottom Line Up Front)
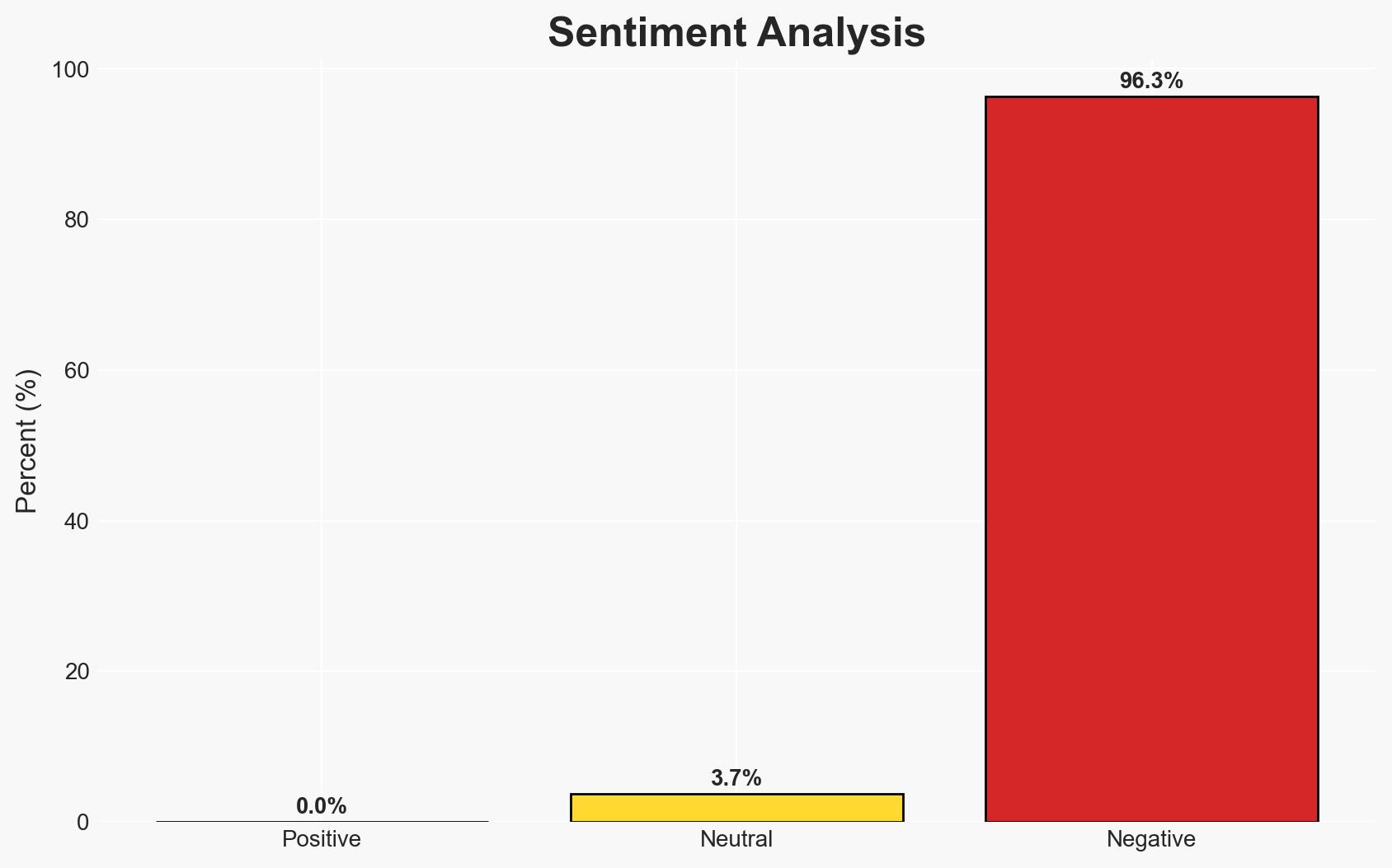
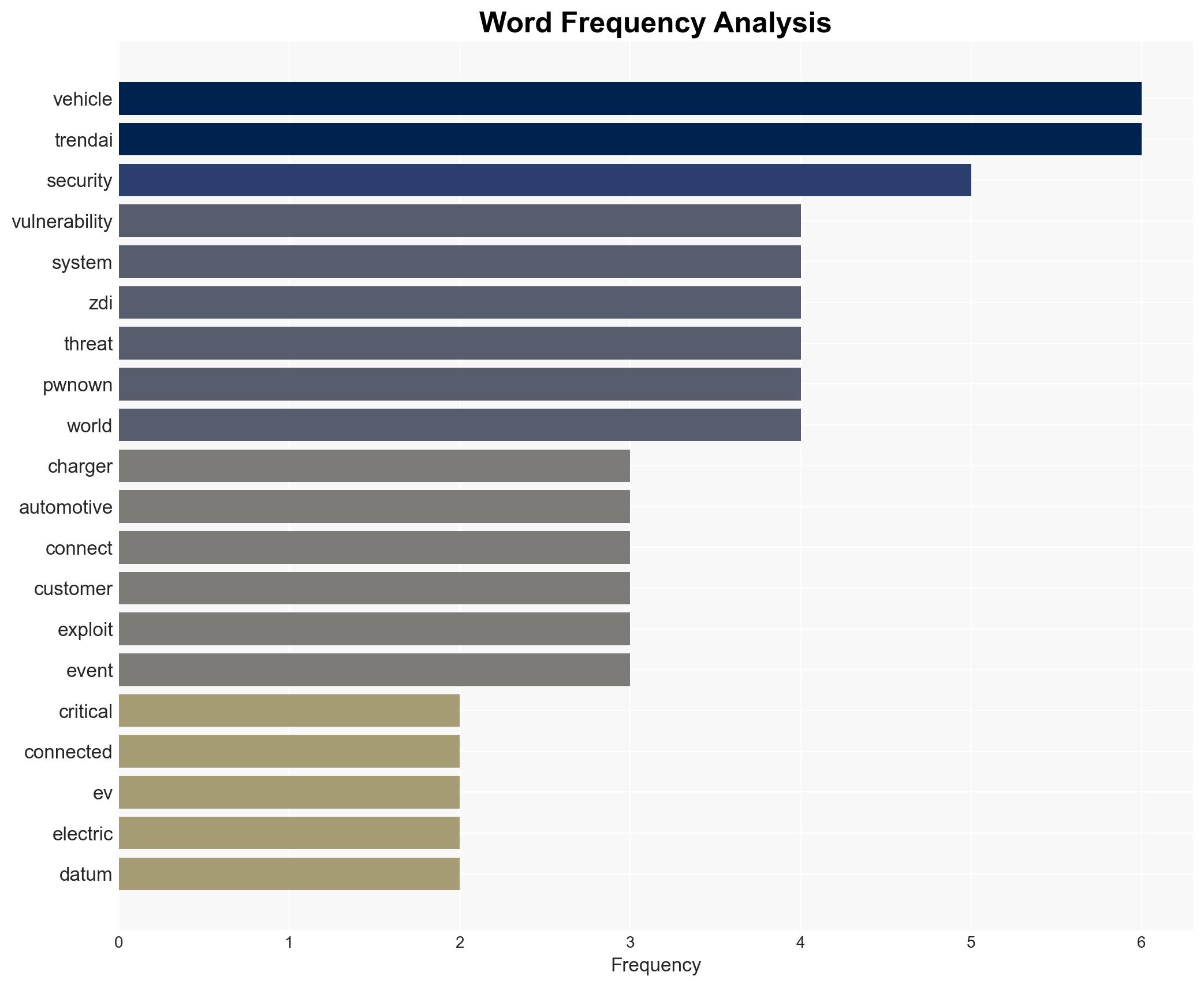
The Pwn2Own Automotive event highlighted significant vulnerabilities in connected vehicle systems, revealing 76 zero-day exploits. This underscores the critical need for enhanced cybersecurity measures in the automotive industry. The event’s findings suggest a growing threat landscape that could impact consumer safety and data privacy. Overall confidence in this assessment is moderate, given the limited scope of the data provided.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities disclosed at Pwn2Own represent a systemic weakness in the automotive cybersecurity posture, necessitating immediate industry-wide reforms. Evidence includes the high number of zero-days discovered and the financial incentives provided to researchers. However, the specific impact on consumer safety remains uncertain.
- Hypothesis B: The vulnerabilities are isolated cases, and the industry’s current cybersecurity measures are generally effective. This hypothesis is supported by the proactive nature of the Pwn2Own event, which aims to identify and address vulnerabilities before they can be exploited. Contradictory evidence includes the sheer number of vulnerabilities found, suggesting broader systemic issues.
- Assessment: Hypothesis A is currently better supported due to the volume and severity of vulnerabilities disclosed. Key indicators that could shift this judgment include future incidents of exploitation or successful mitigation efforts by manufacturers.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities disclosed are representative of broader industry trends; manufacturers will act on disclosed vulnerabilities; the event’s findings are unbiased and comprehensive.
- Information Gaps: Detailed technical analysis of each vulnerability’s potential impact; specific actions taken by manufacturers post-disclosure; long-term trends in automotive cybersecurity incidents.
- Bias & Deception Risks: Potential bias from event sponsors with vested interests in highlighting vulnerabilities; possible overemphasis on vulnerabilities to justify event outcomes.
4. Implications and Strategic Risks
The discovery of numerous vulnerabilities in connected vehicle systems could lead to increased regulatory scrutiny and demand for improved cybersecurity standards. This development may also influence consumer trust and market dynamics in the automotive sector.
- Political / Geopolitical: Potential for increased regulatory actions and international cooperation on automotive cybersecurity standards.
- Security / Counter-Terrorism: Heightened risk of exploitation by malicious actors, including state-sponsored groups, targeting critical infrastructure.
- Cyber / Information Space: Increased focus on securing connected vehicle networks and data privacy measures.
- Economic / Social: Potential economic impact on manufacturers due to increased cybersecurity costs and potential loss of consumer confidence.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage manufacturers to prioritize patching disclosed vulnerabilities; enhance monitoring of connected vehicle networks for potential exploitation attempts.
- Medium-Term Posture (1–12 months): Develop industry-wide cybersecurity standards; foster partnerships between automotive and cybersecurity sectors to improve threat intelligence sharing.
- Scenario Outlook:
- Best: Industry adopts robust cybersecurity measures, reducing vulnerabilities and restoring consumer confidence.
- Worst: Exploitation of vulnerabilities leads to significant breaches, regulatory penalties, and loss of consumer trust.
- Most-Likely: Gradual improvement in cybersecurity practices, with periodic disclosures of vulnerabilities prompting incremental reforms.
6. Key Individuals and Entities
- TrendAI Zero Day Initiative (ZDI)
- Fuzzware.io
- Synacktiv
- VicOne
- Tesla
- Alpitronic
- Open Charge Alliance
- Rachel Jin, Chief Platform and Business Officer at TrendAI
7. Thematic Tags
cybersecurity, automotive industry, zero-day vulnerabilities, connected vehicles, data privacy, threat intelligence, regulatory compliance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us