Resecurity Claims ShinyHunters Targeted a Honeypot, Not Their Actual Systems After Alleged Data Breach
Published on: 2026-01-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Resecurity Says ShinyHunters Fell for Honeypot After Breach Claim
1. BLUF (Bottom Line Up Front)
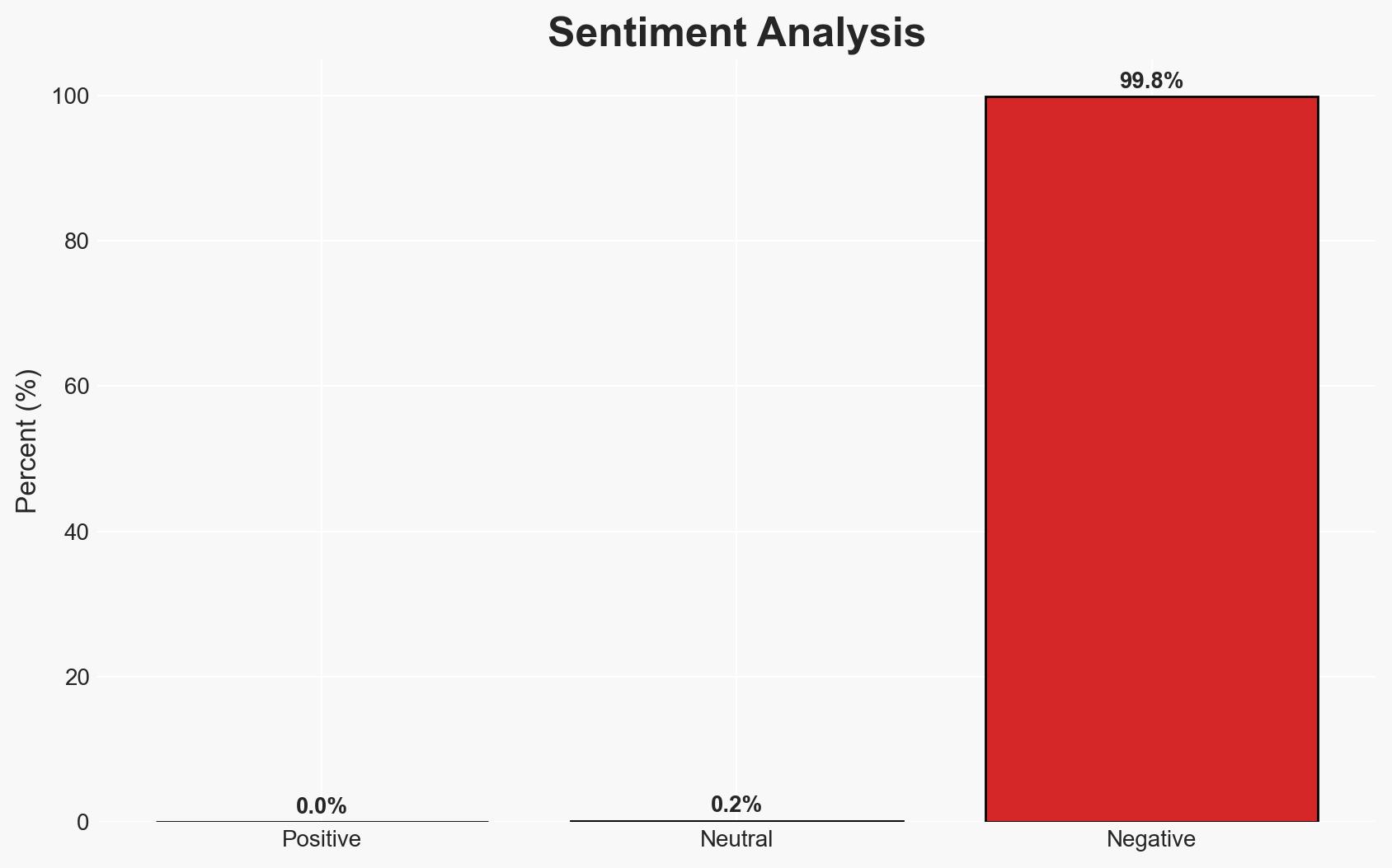
The hacking group ShinyHunters claims to have breached Resecurity’s internal systems, but Resecurity asserts the group interacted with a honeypot. The evidence provided by Resecurity suggests the breach was a controlled deception, aimed at gathering intelligence on the attackers. This assessment is made with moderate confidence, pending further verification of the logs and evidence shared by Resecurity.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters successfully breached Resecurity’s actual systems and accessed sensitive data. Supporting evidence includes the group’s claims and screenshots. Contradicting evidence includes Resecurity’s detailed logs and evidence of a honeypot setup.
- Hypothesis B: ShinyHunters interacted with a honeypot, not the actual systems, as part of Resecurity’s deception strategy. Supporting evidence includes Resecurity’s logs, screenshots of fake accounts, and the isolated nature of the honeypot environment. Contradicting evidence is limited to the claims made by ShinyHunters.
- Assessment: Hypothesis B is currently better supported due to the detailed evidence provided by Resecurity, including logs and the strategic use of synthetic data. Indicators that could shift this judgment include independent verification of the logs or new evidence from ShinyHunters.
3. Key Assumptions and Red Flags
- Assumptions: Resecurity’s logs and evidence are authentic; ShinyHunters’ claims are not independently verified; the honeypot was effectively isolated from real systems.
- Information Gaps: Independent verification of the logs and evidence; detailed technical analysis of the screenshots provided by ShinyHunters.
- Bias & Deception Risks: Potential bias in Resecurity’s reporting to protect its reputation; ShinyHunters may exaggerate claims for notoriety; manipulation of evidence by either party.
4. Implications and Strategic Risks
This development highlights the ongoing cat-and-mouse dynamics between cybersecurity firms and hacking groups. It may influence how companies deploy deception tactics and how threat actors adapt their strategies.
- Political / Geopolitical: Increased scrutiny on cybersecurity practices could lead to regulatory changes.
- Security / Counter-Terrorism: Enhanced threat actor profiling and intelligence gathering through deception techniques.
- Cyber / Information Space: Potential escalation in cyber operations and countermeasures; increased use of honeypots.
- Economic / Social: Potential reputational impact on Resecurity; broader implications for trust in cybersecurity solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Verify Resecurity’s logs through independent cybersecurity experts; monitor ShinyHunters’ communications for further claims or evidence.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms for intelligence sharing; develop advanced deception capabilities.
- Scenario Outlook: Best: Resecurity’s claims are verified, enhancing its reputation. Worst: ShinyHunters’ claims are substantiated, leading to reputational damage. Most-Likely: Continued ambiguity with no definitive proof from either side.
6. Key Individuals and Entities
- Resecurity (Cybersecurity firm)
- ShinyHunters (Hacking group)
- Hackread.com (Media outlet)
7. Thematic Tags
cybersecurity, cyber-deception, hacking, honeypot, threat intelligence, cyber-espionage, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us