Resecurity Denies Breach Claims by Scattered Lapsus$ Hunters, Calls Access a Honeypot Operation
Published on: 2026-01-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ShinyHunters claims Resecurity hack firm says its a honeypot
1. BLUF (Bottom Line Up Front)
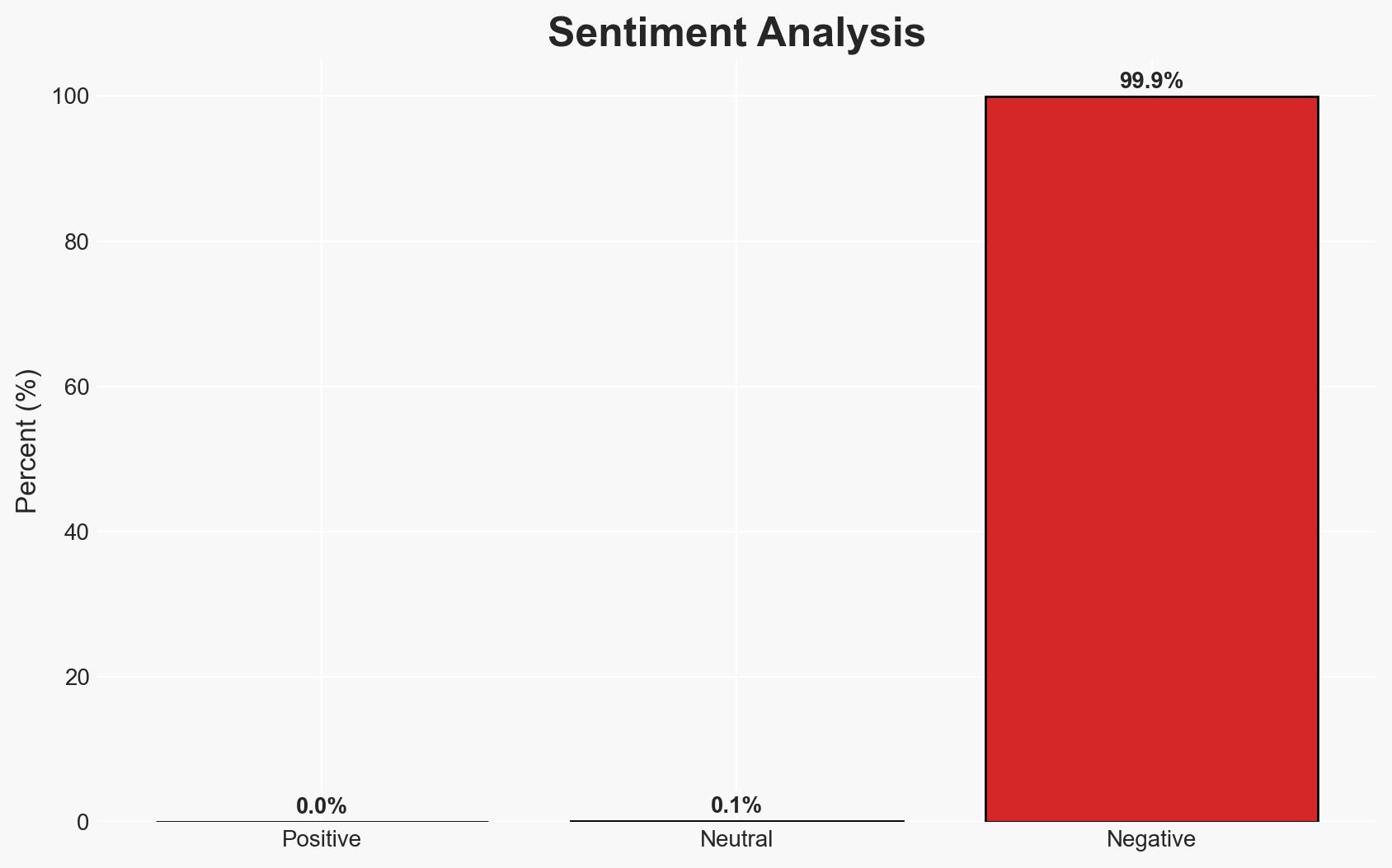
The incident involving the alleged breach of Resecurity by the Scattered Lapsus$ Hunters is currently assessed as a likely honeypot operation by Resecurity, designed to monitor threat actor activities. This assessment is based on Resecurity’s claims and the lack of concrete evidence from the threat actors. The situation affects cybersecurity stakeholders, with a moderate confidence level in this judgment.
2. Competing Hypotheses
- Hypothesis A: The breach of Resecurity’s systems by Scattered Lapsus$ Hunters was genuine, resulting in the theft of sensitive data. Supporting evidence includes screenshots published by the threat actors. Contradicting evidence includes Resecurity’s claim that the systems accessed were honeypots.
- Hypothesis B: The breach was a controlled honeypot operation by Resecurity to monitor and gather intelligence on threat actors. Supporting evidence includes Resecurity’s detailed explanation of the honeypot setup and lack of corroborating evidence from independent sources. Contradicting evidence is the threat actors’ claims and screenshots.
- Assessment: Hypothesis B is currently better supported due to Resecurity’s proactive disclosure and detailed explanation of the honeypot setup. Indicators that could shift this judgment include independent verification of the breach or credible evidence of data compromise.
3. Key Assumptions and Red Flags
- Assumptions: Resecurity’s systems are capable of deploying effective honeypots; the threat actors’ claims are not independently verified; screenshots alone are insufficient proof of a breach.
- Information Gaps: Lack of independent verification of the breach; absence of technical details on the alleged data exfiltration.
- Bias & Deception Risks: Potential bias from Resecurity in portraying the incident as a honeypot; threat actors may exaggerate claims to enhance their reputation.
4. Implications and Strategic Risks
This development could influence the cybersecurity landscape by affecting trust in cybersecurity firms and their ability to protect sensitive data. The incident may also impact threat actor tactics and strategies.
- Political / Geopolitical: Potential diplomatic tensions if state actors are suspected of involvement or support.
- Security / Counter-Terrorism: Increased scrutiny on cybersecurity firms’ defenses and threat actor capabilities.
- Cyber / Information Space: Possible increase in honeypot deployments and threat actor countermeasures.
- Economic / Social: Potential impact on client trust and business operations for Resecurity and similar firms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Verify the authenticity of the breach claims; enhance monitoring of threat actor communications for further insights.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms for intelligence sharing; invest in advanced honeypot technologies.
- Scenario Outlook: Best: Incident is confirmed as a honeypot with no real data loss. Worst: Genuine breach with significant data compromise. Most-Likely: Continued ambiguity with no conclusive evidence of a genuine breach.
6. Key Individuals and Entities
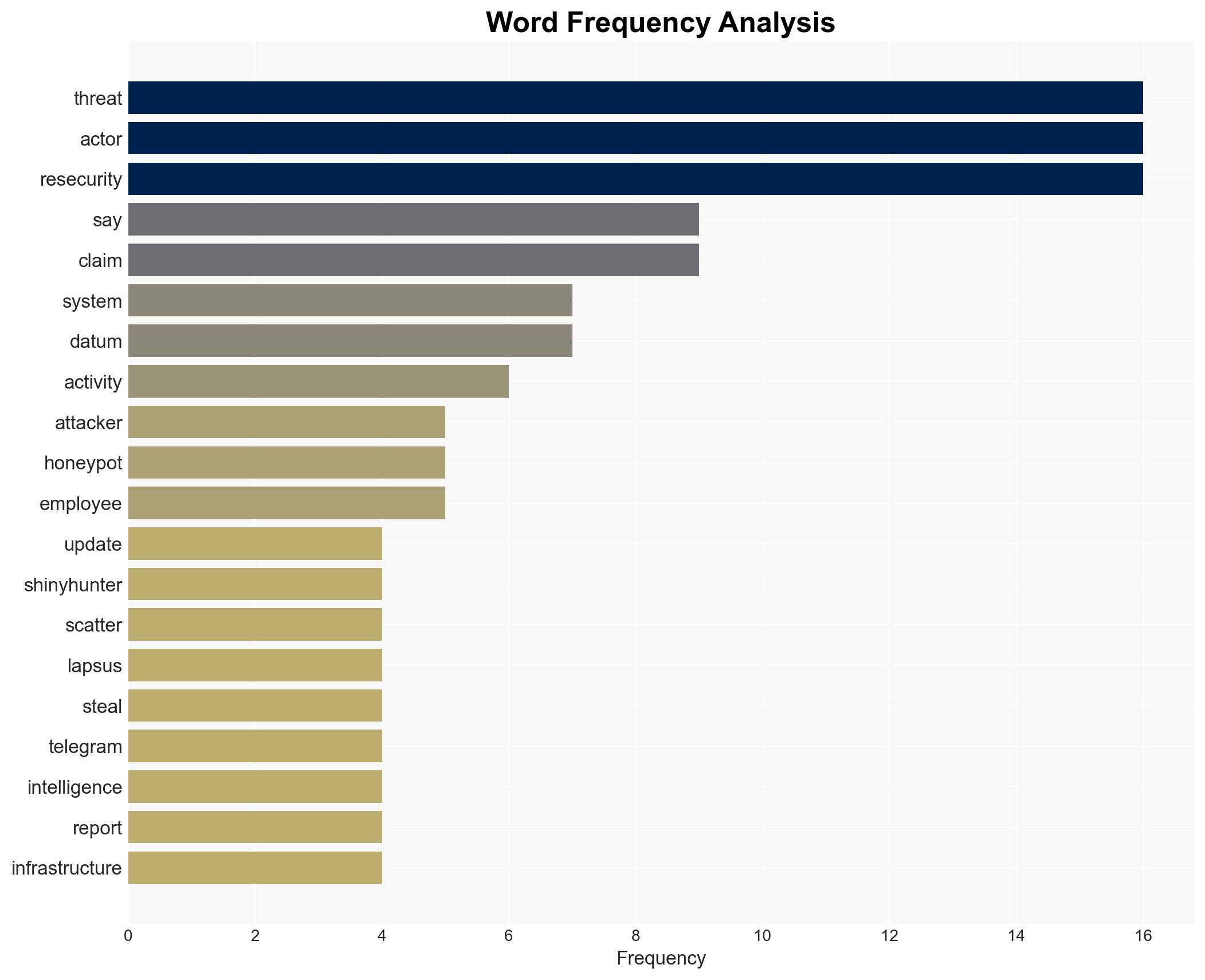
- Scattered Lapsus$ Hunters
- Resecurity
- ShinyHunters
- Lapsus$
- Scattered Spider
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, honeypot, cyber-espionage, threat actors, data breach, information security, intelligence gathering
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us