Resecurity Unveils 105 Pages of Data on John Erin Binns, Revealing Key Insights into His Online Activities
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cyber Counterintelligence CCI Resecurity releases data on John Erin Binns IRDev
1. BLUF (Bottom Line Up Front)
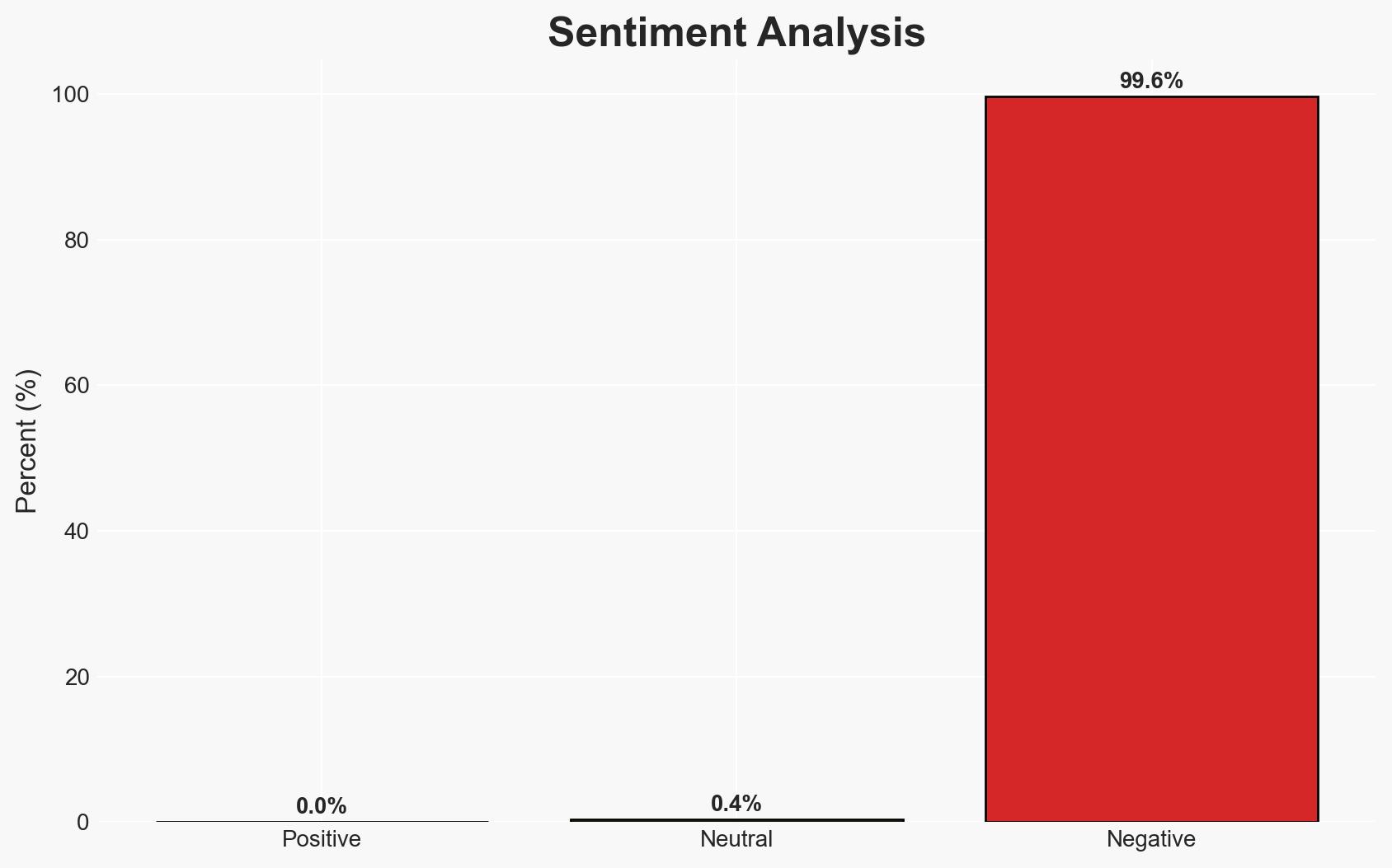
Resecurity’s release of data on John Erin Binns, a known hacker, highlights ongoing cyber threats against U.S. government entities. The evidence suggests Binns remains active in cyber operations potentially aligned with adversarial interests. The non-extradition stance by Turkey complicates legal actions. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
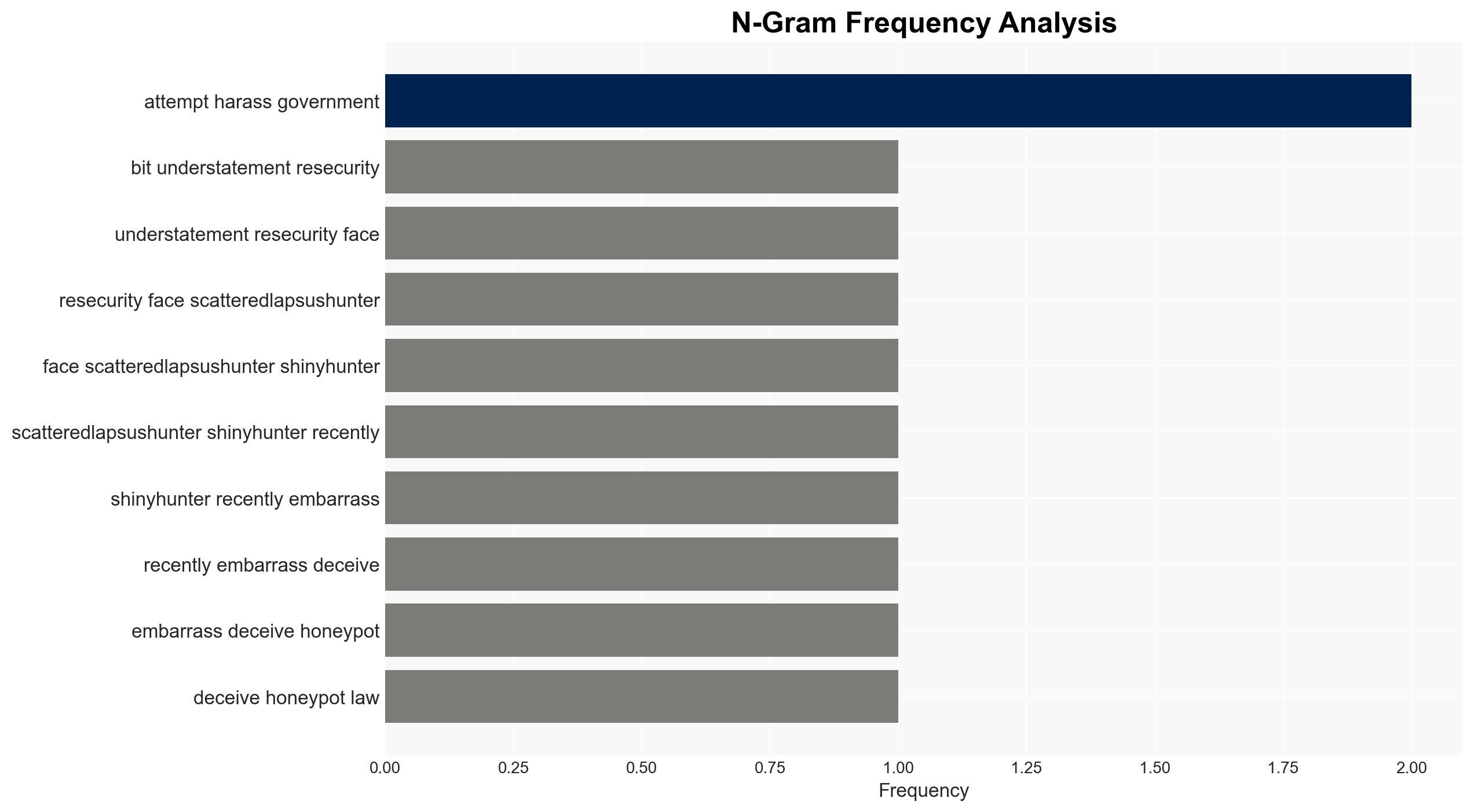
- Hypothesis A: John Erin Binns is actively engaged in cyber activities targeting U.S. interests, potentially on behalf of hostile entities. This is supported by Resecurity’s data release and Binns’ history of harassment against U.S. officials. However, the lack of direct message content limits full verification.
- Hypothesis B: Binns’ activities are primarily self-motivated for personal gain and notoriety, rather than state-sponsored. This is supported by the common motive among hackers for fame and financial gain. The absence of direct state ties in the data release supports this view.
- Assessment: Hypothesis A is currently better supported due to the pattern of targeting U.S. government officials and the potential alignment with adversarial interests. Indicators such as increased sophistication or direct links to state actors could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The data provided by Resecurity is authentic and accurately reflects Binns’ activities. Turkey’s non-extradition stance is consistent and will not change in the near term. Binns’ motivations include both personal and potentially state-aligned interests.
- Information Gaps: The specific contents of the messages and any direct evidence of state sponsorship are missing. Details on Binns’ current operational capabilities and network are unclear.
- Bias & Deception Risks: Resecurity’s potential bias as a private entity seeking to demonstrate its capabilities. The possibility of manipulated or selectively released data to influence perceptions.
4. Implications and Strategic Risks
This development could exacerbate tensions between the U.S. and Turkey, complicate cyber defense strategies, and influence hacker community dynamics.
- Political / Geopolitical: Potential diplomatic strain with Turkey over non-extradition and perceived harboring of cybercriminals.
- Security / Counter-Terrorism: Increased threat to U.S. government personnel and infrastructure from cyber harassment and espionage.
- Cyber / Information Space: Enhanced focus on counterintelligence measures and cyber defense strategies against similar threat actors.
- Economic / Social: Potential impacts on U.S. businesses targeted by hackers seeking financial gain and notoriety.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Binns’ known aliases and networks, engage with Turkish counterparts on legal cooperation, and strengthen cyber defenses for targeted U.S. entities.
- Medium-Term Posture (1–12 months): Develop partnerships with private cybersecurity firms for intelligence sharing, and invest in counterintelligence capabilities to detect and disrupt similar threats.
- Scenario Outlook: Best: Binns is apprehended or ceases activities. Worst: Escalation of cyber attacks on critical U.S. infrastructure. Most-Likely: Continued low-level harassment and cyber operations with periodic spikes in activity.
6. Key Individuals and Entities
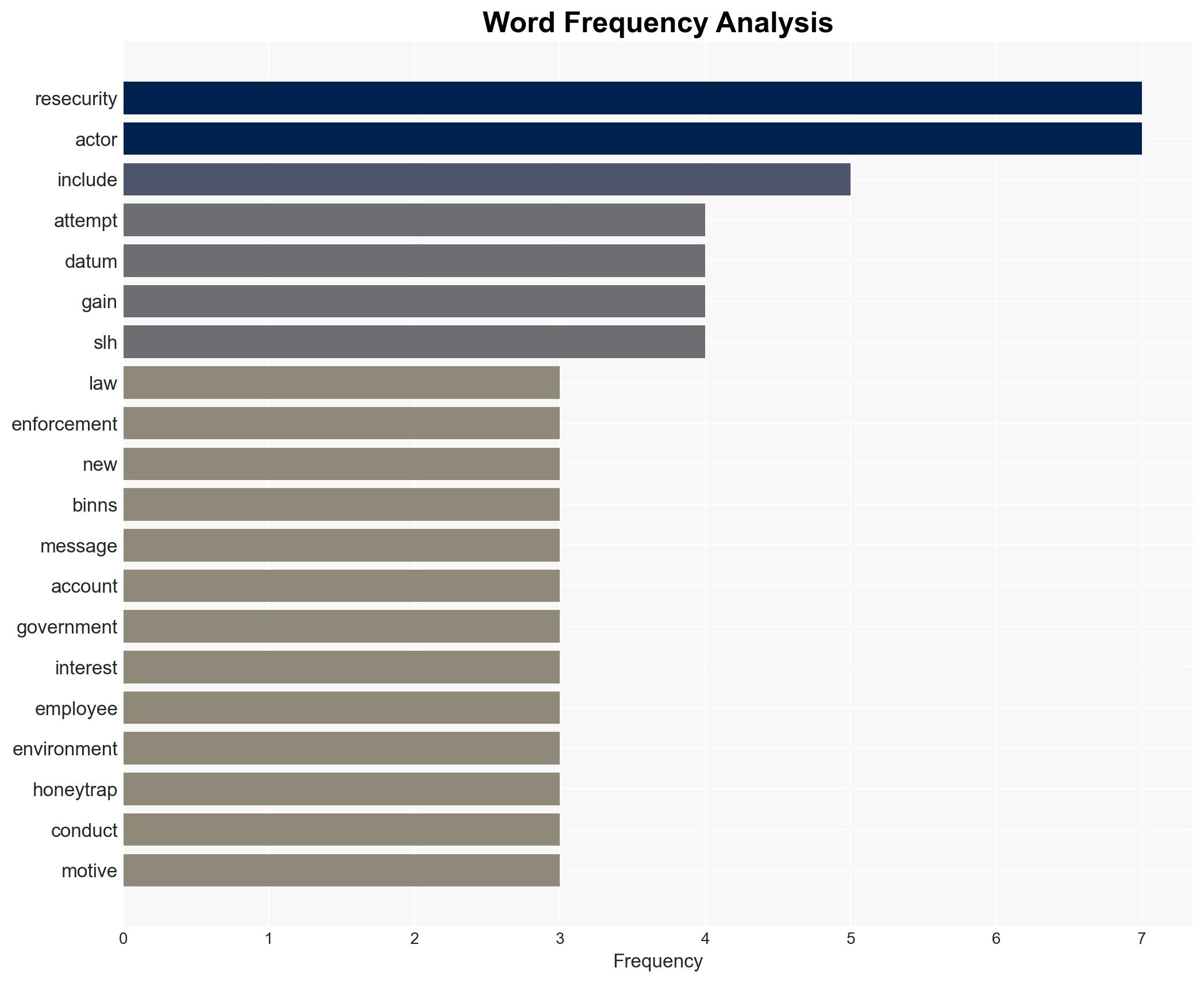
- John Erin Binns (“IRDev,” “IntelSecrets”)
- Resecurity
- ScatteredLapsus$Hunters
- ShinyHunters
- Connor Riley Moucka (“Waifu,” “Judische,” “Ellyel8”)
- Cameron John Wagenius (“Kiberphant0m”)
7. Thematic Tags
cybersecurity, counterintelligence, cyber-espionage, U.S.-Turkey relations, hacker motivations, cyber defense, information operations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us