Rising Risk of Social Engineering Attacks Targeting Hotel Front Desk Operations
Published on: 2026-01-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Social Engineering at the Front Desk A Growing Threat for Hotels
1. BLUF (Bottom Line Up Front)
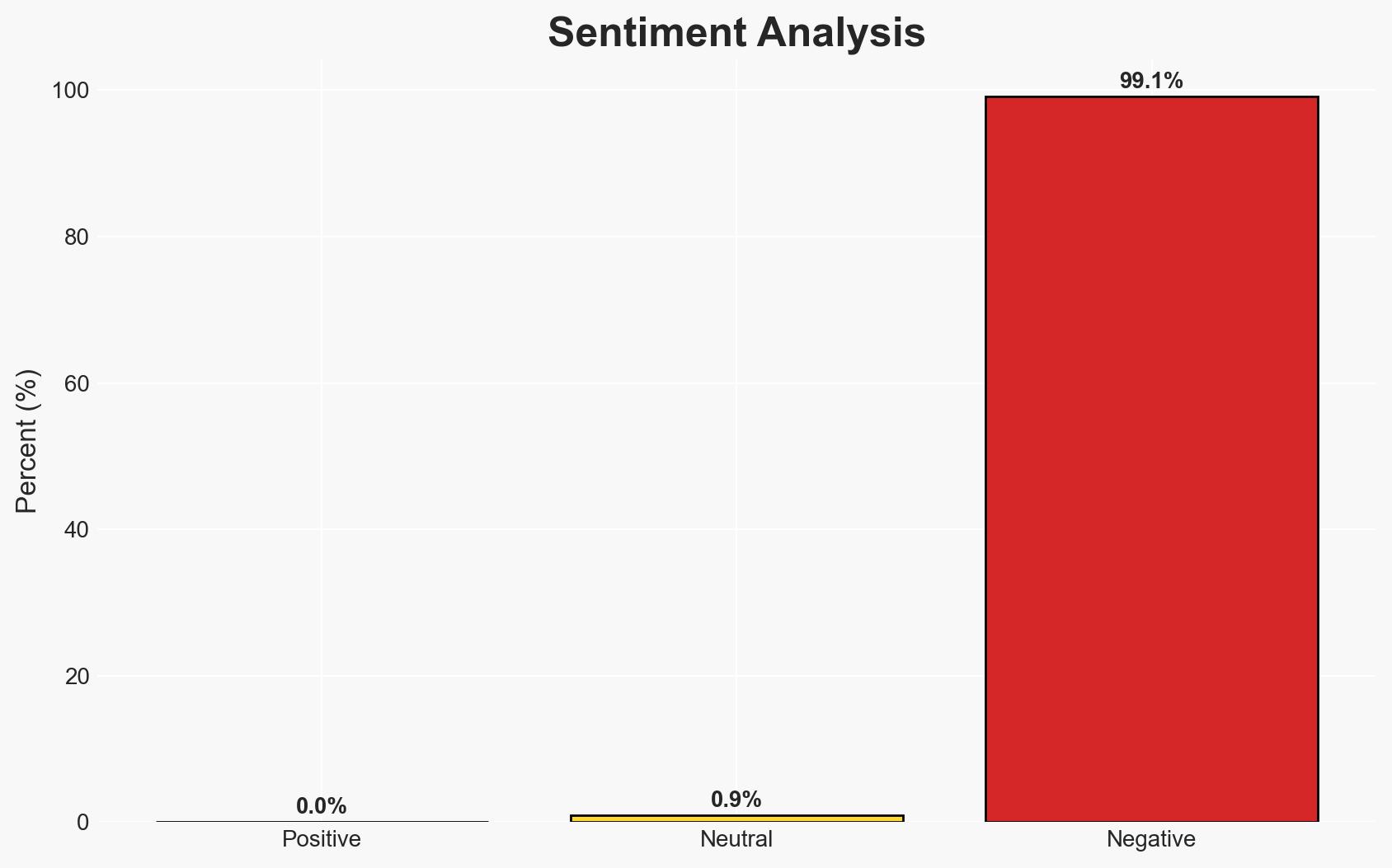
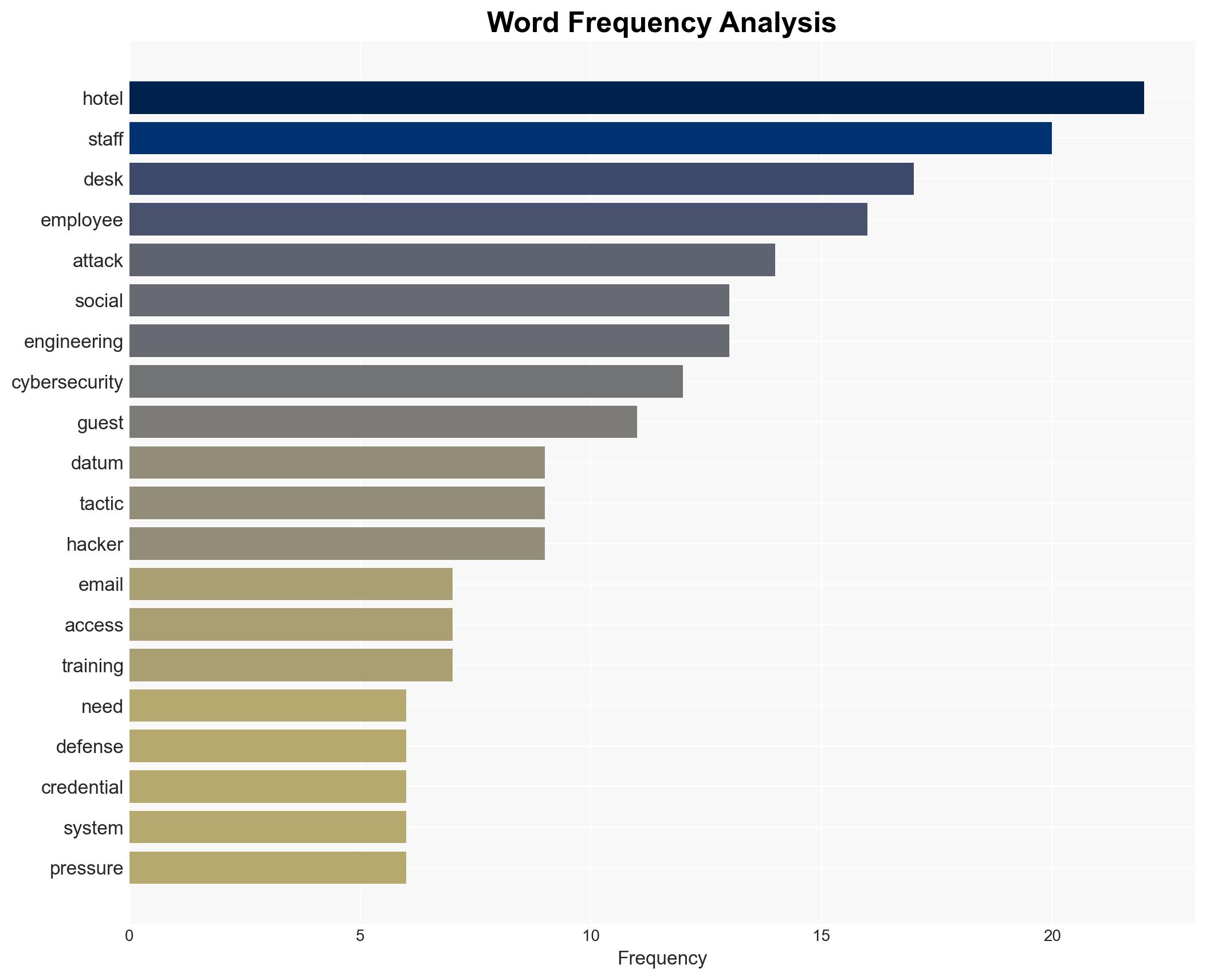
Social engineering attacks targeting hotel front desk staff pose a significant cybersecurity threat, exploiting the industry’s inherent culture of trust. The most likely hypothesis is that these attacks will increase in frequency and sophistication, affecting both hotel operations and guest data security. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
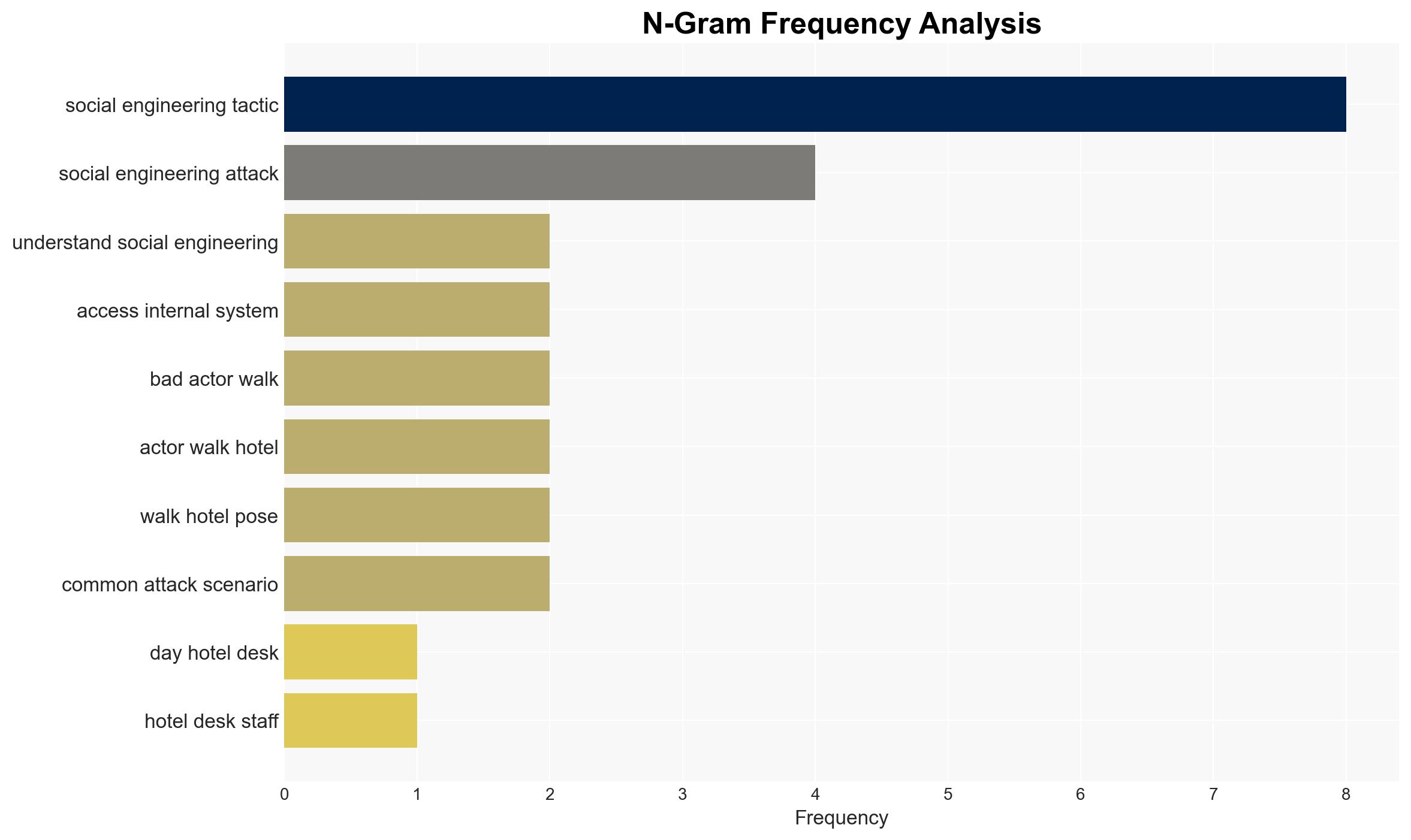
- Hypothesis A: Social engineering attacks on hotel front desks will increase due to the high value of personal identifiable information (PII) and the industry’s trust-based culture. Supporting evidence includes the inherent vulnerability of human factors and the reported prevalence of password-based identity attacks. Key uncertainties involve the extent of hotel staff training and awareness.
- Hypothesis B: Hotels will successfully mitigate social engineering threats through enhanced training and cybersecurity measures. This is supported by the potential for increased awareness and investment in cybersecurity defenses. However, this is contradicted by the persistent nature of human error and manipulation tactics.
- Assessment: Hypothesis A is currently better supported due to the ongoing sophistication of social engineering tactics and the industry’s reliance on human interaction. Indicators that could shift this judgment include significant improvements in staff training and adoption of advanced cybersecurity technologies.
3. Key Assumptions and Red Flags
- Assumptions: Hotels will continue to prioritize guest service over cybersecurity; social engineering tactics will evolve faster than defensive measures; front desk staff have limited cybersecurity training; attackers perceive hotels as lucrative targets for PII.
- Information Gaps: Specific data on the frequency and success rate of social engineering attacks in the hotel industry; effectiveness of current training programs; detailed incident reports from affected hotels.
- Bias & Deception Risks: Overreliance on anecdotal evidence; potential underreporting of incidents due to reputational concerns; manipulation of threat data by cybersecurity vendors.
4. Implications and Strategic Risks
The increase in social engineering attacks could lead to significant data breaches, affecting guest trust and hotel reputations. Over time, this may necessitate regulatory changes and increased cybersecurity investments.
- Political / Geopolitical: Potential for increased regulatory scrutiny and international cooperation on data protection standards.
- Security / Counter-Terrorism: Enhanced threat environment as attackers may leverage compromised data for broader criminal or terrorist activities.
- Cyber / Information Space: Escalation in cyber threats targeting the hospitality sector, with potential spillover into other industries reliant on PII.
- Economic / Social: Potential economic impact on the hospitality industry due to loss of consumer confidence and increased operational costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive cybersecurity audits; implement mandatory social engineering awareness training for all front desk staff; establish incident response protocols.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in advanced threat detection technologies; enhance data encryption and access controls.
- Scenario Outlook:
- Best: Hotels successfully implement robust defenses, reducing attack success rates.
- Worst: A major data breach occurs, leading to significant financial and reputational damage.
- Most-Likely: Incremental improvements in defenses, but attacks continue to evolve, maintaining a persistent threat.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, social engineering, hospitality industry, data breaches, human factors, phishing, vishing
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us