Risks Associated with Kerberos Credentials Cache Type FILE in MITHeimdal Implementations
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Re MITHeimdal Kerberos credentials cache type FILE risks
1. BLUF (Bottom Line Up Front)
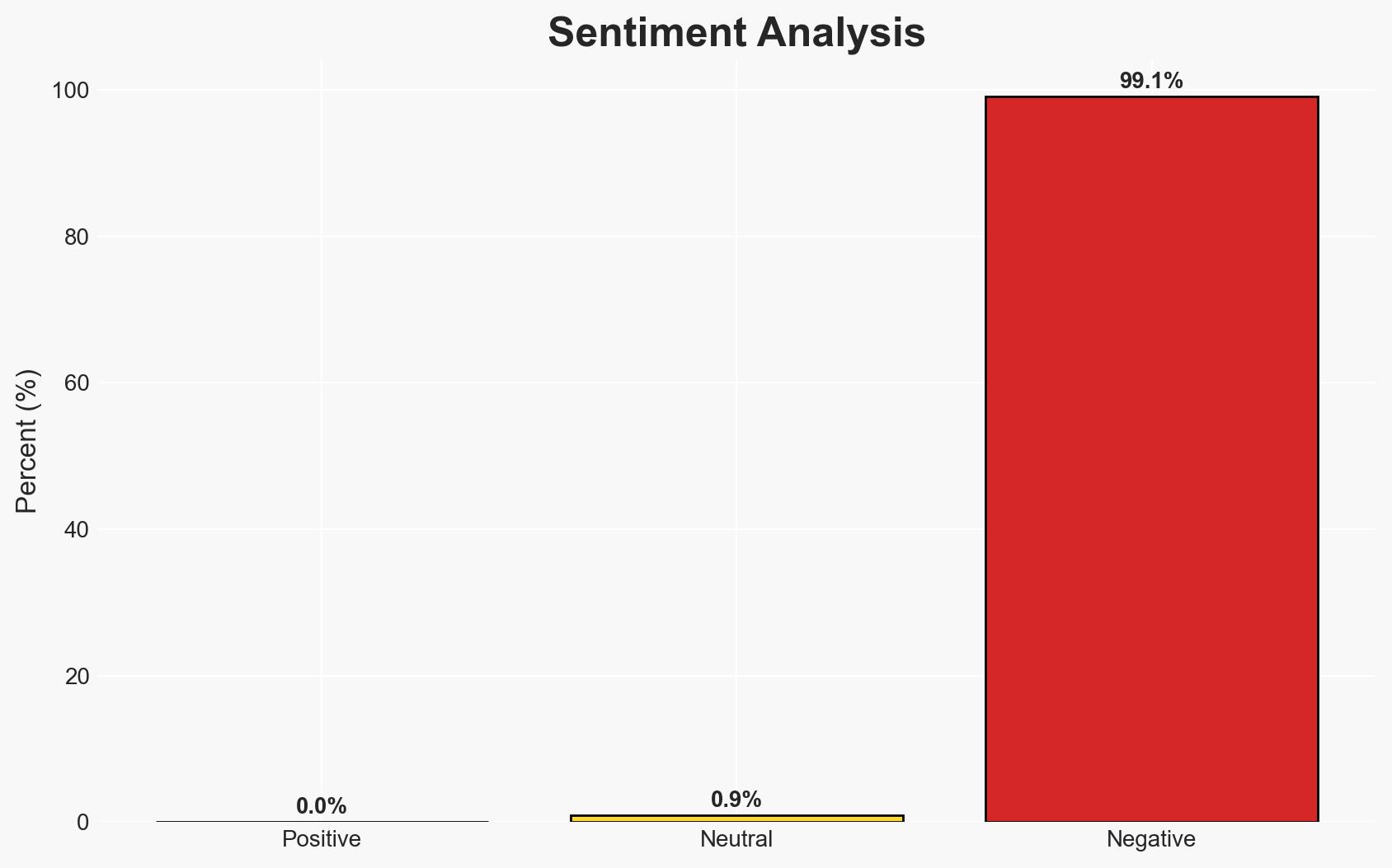
The risk associated with Kerberos credentials cache type FILE, particularly in MIT and Heimdal implementations, poses a potential security vulnerability in systems using these services. The most likely hypothesis is that improper management of ticket caches could lead to unauthorized access. This issue primarily affects organizations using Kerberos for authentication, with moderate confidence in this assessment due to identified information gaps and assumptions.
2. Competing Hypotheses
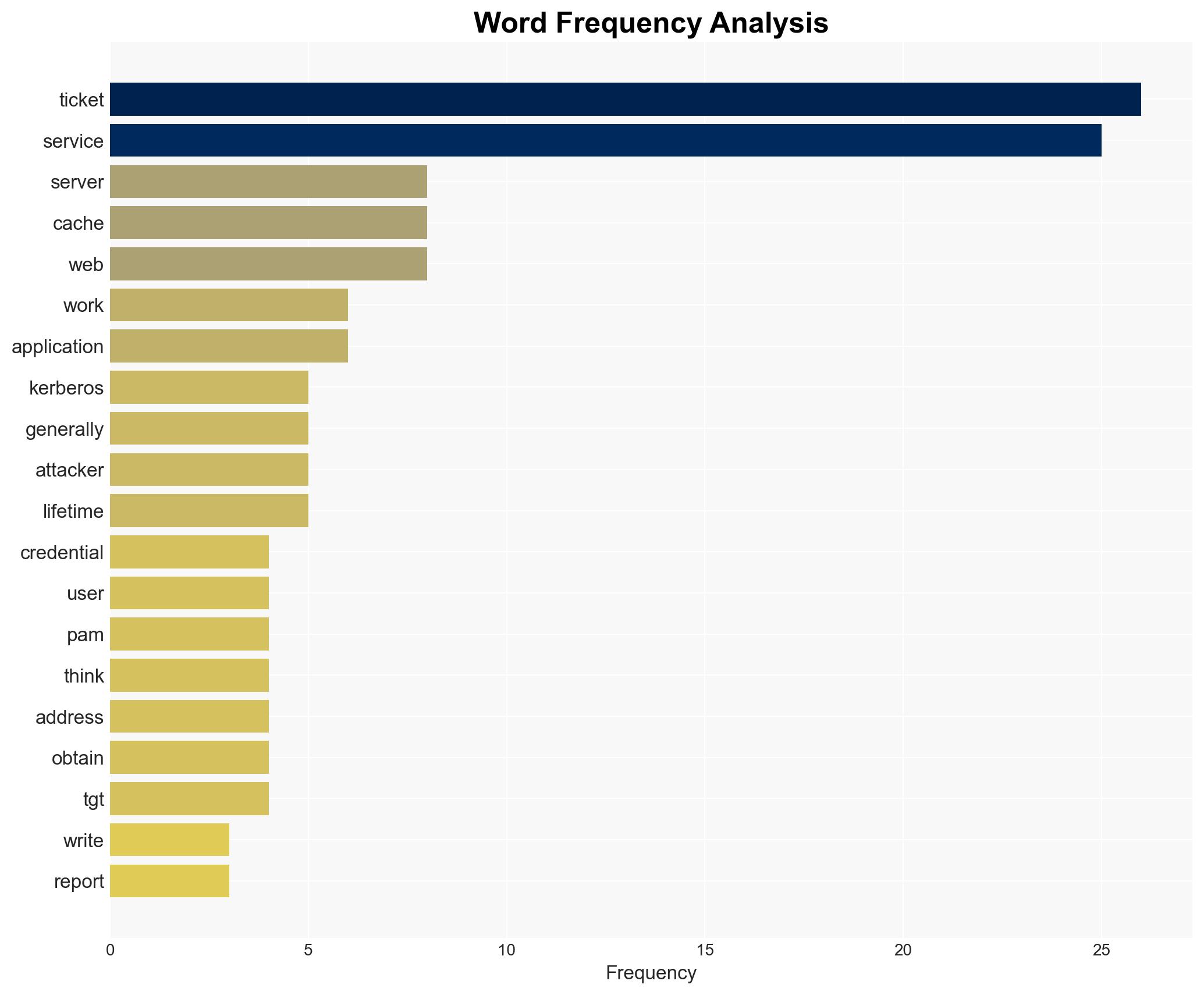
- Hypothesis A: The primary risk is from improper cleanup of Kerberos ticket caches, which could allow attackers to hijack user accounts. Evidence includes the potential for tickets to be stored in /tmp and not properly discarded. Key uncertainties include the extent of adoption of best practices in ticket management.
- Hypothesis B: The risk is overstated, as most systems have adequate measures to prevent ticket misuse, and vulnerabilities are limited to specific implementations or configurations. This hypothesis is supported by the notion that Kerberos tickets should not be “keys to the kingdom” and that detection mechanisms exist, albeit inconsistently applied.
- Assessment: Hypothesis A is currently better supported due to the commonality of improper ticket management practices and the potential for exploitation. Indicators that could shift this judgment include evidence of widespread adoption of best practices or improved detection capabilities.
3. Key Assumptions and Red Flags
- Assumptions: Organizations using Kerberos are not uniformly applying best practices; Kerberos ticket caches are often left unsecured; Administrators may not be fully aware of the risks.
- Information Gaps: Lack of data on the prevalence of ticket cache mismanagement and the effectiveness of existing detection mechanisms.
- Bias & Deception Risks: Potential bias in underestimating the capability of organizations to manage Kerberos credentials; risk of deception from adversaries exploiting known vulnerabilities.
4. Implications and Strategic Risks
The development of vulnerabilities in Kerberos ticket management could lead to increased cyber threats and exploitation by adversaries, affecting organizational security and operational integrity.
- Political / Geopolitical: Potential for state-sponsored actors to exploit these vulnerabilities for espionage or disruption.
- Security / Counter-Terrorism: Increased risk of unauthorized access to sensitive systems, potentially impacting national security.
- Cyber / Information Space: Heightened threat landscape with potential for increased cyber-attacks targeting Kerberos implementations.
- Economic / Social: Possible economic impact due to data breaches and loss of trust in affected organizations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct audits of Kerberos implementations to ensure proper ticket management; enhance monitoring for unauthorized access attempts.
- Medium-Term Posture (1–12 months): Develop and implement comprehensive training programs for administrators on best practices; invest in improved detection and response capabilities.
- Scenario Outlook:
- Best: Organizations adopt best practices, significantly reducing vulnerabilities.
- Worst: Exploitation of vulnerabilities leads to major breaches and operational disruptions.
- Most-Likely: Incremental improvements in security posture with occasional breaches due to lagging implementations.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, Kerberos, authentication, vulnerability management, information security, network security, risk assessment
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us