Risky Business 795 — How The Com is hacking Salesforce tenants – Risky.biz
Published on: 2025-06-11
Intelligence Report: Risky Business 795 — How The Com is hacking Salesforce tenants – Risky.biz
1. BLUF (Bottom Line Up Front)
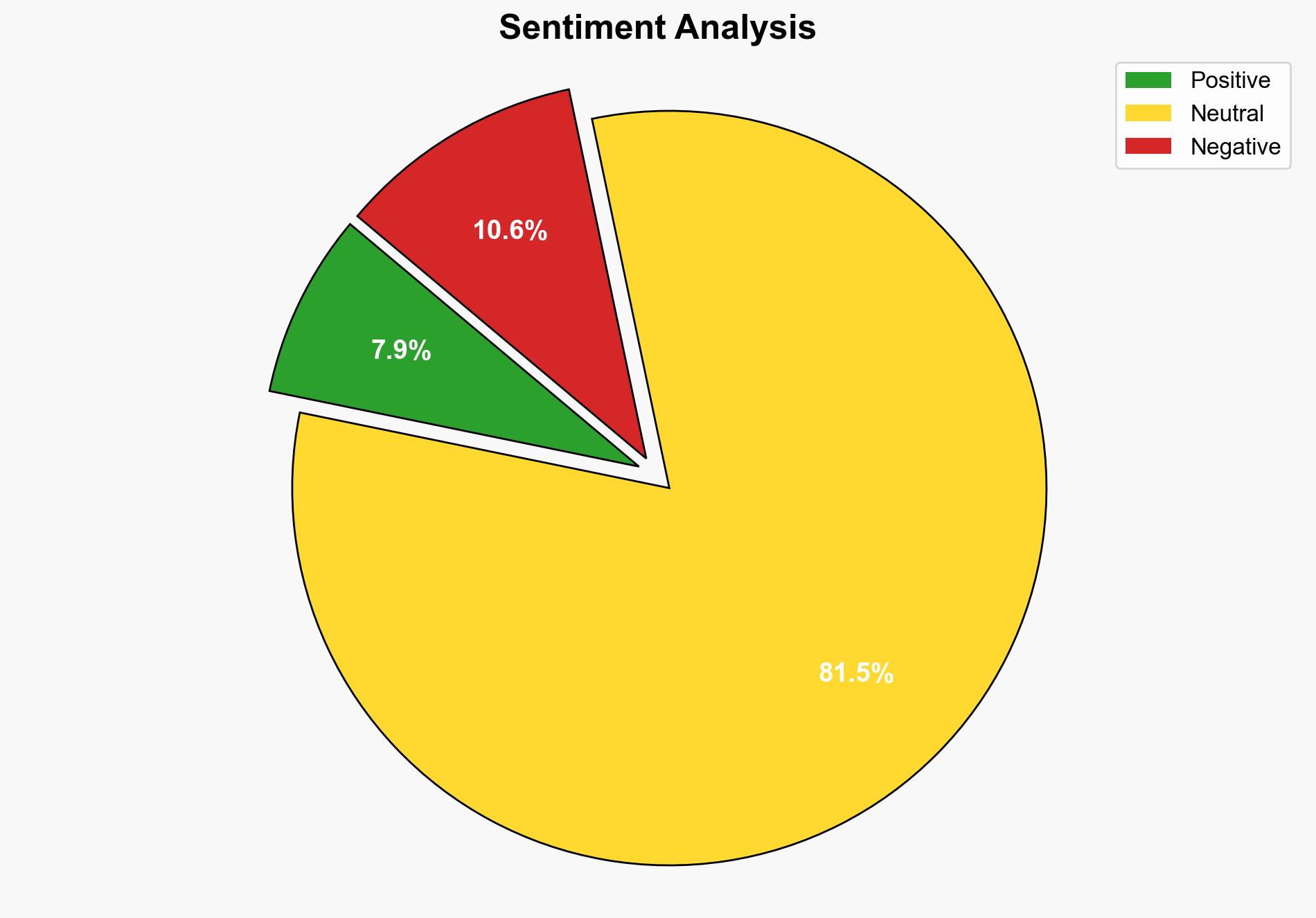
The report identifies a significant cybersecurity threat involving the exploitation of Salesforce tenants through social engineering and unauthorized app access. Key findings suggest a coordinated effort to leverage these vulnerabilities for data theft and extortion. Recommendations include enhancing authentication protocols and increasing user awareness to mitigate these risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that adversaries are likely using social engineering tactics to gain unauthorized access to Salesforce applications, posing a risk to tenant data security.
Indicators Development
Monitoring has revealed anomalies in user behavior and app authorization processes, suggesting potential exploitation attempts.
Bayesian Scenario Modeling
Probabilistic models predict a high likelihood of continued attacks targeting Salesforce tenants, with potential for increased sophistication.
3. Implications and Strategic Risks
The exploitation of Salesforce tenants represents a broader cybersecurity threat, with potential repercussions for data privacy and business continuity. The systemic vulnerability could lead to cascading effects, impacting other sectors reliant on cloud-based solutions.
4. Recommendations and Outlook
- Enhance multi-factor authentication and conduct regular security audits to identify and address vulnerabilities.
- Implement user training programs to recognize and report social engineering attempts.
- Scenario-based projections:
- Best Case: Improved security measures prevent further breaches, maintaining data integrity.
- Worst Case: Continued exploitation leads to significant data breaches and financial losses.
- Most Likely: Incremental improvements in security reduce but do not eliminate threat activity.
5. Key Individuals and Entities
Patrick Gray, Adam Boileau, Alex Tilley, Harris Walz
6. Thematic Tags
national security threats, cybersecurity, data protection, cloud security