Risky Business 810 — Data extortion attacks have a silver lining – Risky.biz
Published on: 2025-10-15
Intelligence Report: Risky Business 810 — Data extortion attacks have a silver lining – Risky.biz
1. BLUF (Bottom Line Up Front)
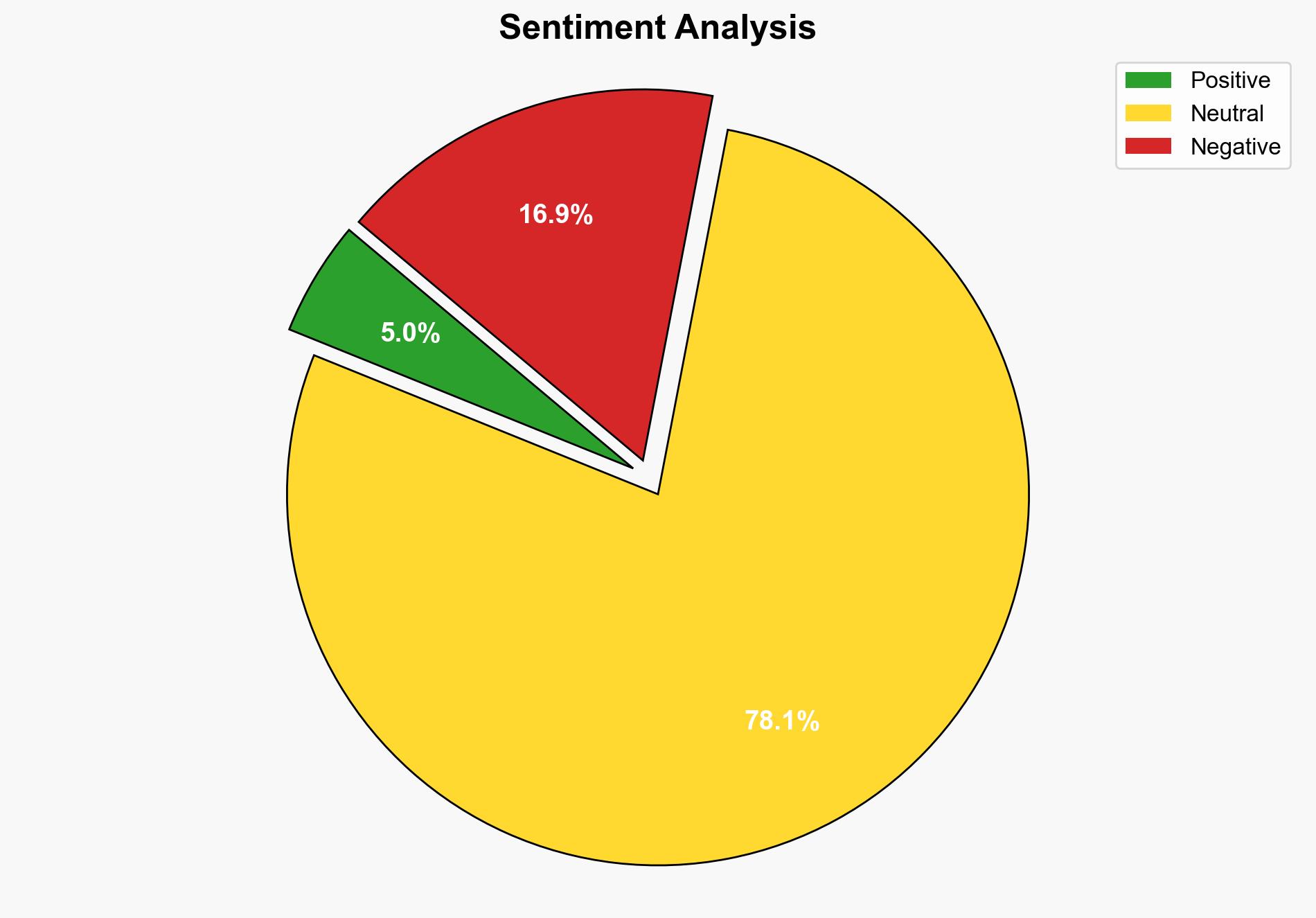
The analysis suggests that data extortion attacks, while posing significant cybersecurity threats, may inadvertently drive advancements in cybersecurity practices and technologies. The better-supported hypothesis is that these attacks will lead to increased investment in cybersecurity infrastructure and innovation. Confidence level: Moderate. Recommended action: Encourage proactive cybersecurity measures and investments in emerging technologies to mitigate risks.
2. Competing Hypotheses
1. **Hypothesis A**: Data extortion attacks primarily serve as a catalyst for improved cybersecurity measures and technological advancements, as organizations are forced to adapt and innovate in response to threats.
2. **Hypothesis B**: Data extortion attacks primarily result in increased financial and reputational damage to organizations, with minimal long-term benefits in terms of cybersecurity improvements.
Using Analysis of Competing Hypotheses (ACH 2.0), Hypothesis A is better supported by the observed increase in cybersecurity investments and innovations following high-profile attacks. Hypothesis B is less supported due to the lack of evidence showing long-term stagnation in cybersecurity post-attacks.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Organizations have the resources and willingness to invest in cybersecurity following an attack.
– Technological advancements are effectively implemented and reduce future risks.
– **Red Flags**:
– Potential overestimation of the positive impact of attacks on cybersecurity innovation.
– Lack of comprehensive data on long-term impacts of extortion attacks on organizational resilience.
4. Implications and Strategic Risks
– **Economic**: Increased costs for organizations to enhance cybersecurity measures.
– **Cyber**: Potential for more sophisticated attacks as cybercriminals adapt.
– **Geopolitical**: Nations may leverage cybersecurity advancements for strategic advantages.
– **Psychological**: Heightened awareness and fear of cyber threats may drive policy changes and public demand for stronger cybersecurity measures.
5. Recommendations and Outlook
- Encourage investment in cybersecurity research and development to stay ahead of evolving threats.
- Promote public-private partnerships to enhance information sharing and collaborative defense strategies.
- Scenario-based projections:
- Best: Significant reduction in successful extortion attacks due to advanced cybersecurity measures.
- Worst: Escalation of attacks leading to widespread economic and reputational damage.
- Most Likely: Gradual improvement in cybersecurity practices with intermittent successful attacks.
6. Key Individuals and Entities
– Patrick Gray
– Adam Boileau
– Mike Wiacek
– Entities: FBI, NSA, Cybercom, Clop, Oracle, NSO Group, Microsoft, Apple, Wiz, SonicWall, CrowdStrike
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus