RomCom Exploits SocGholish Fake Updates to Deploy Mythic Agent Malware on U.S. Civil Engineering Firm
Published on: 2025-11-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
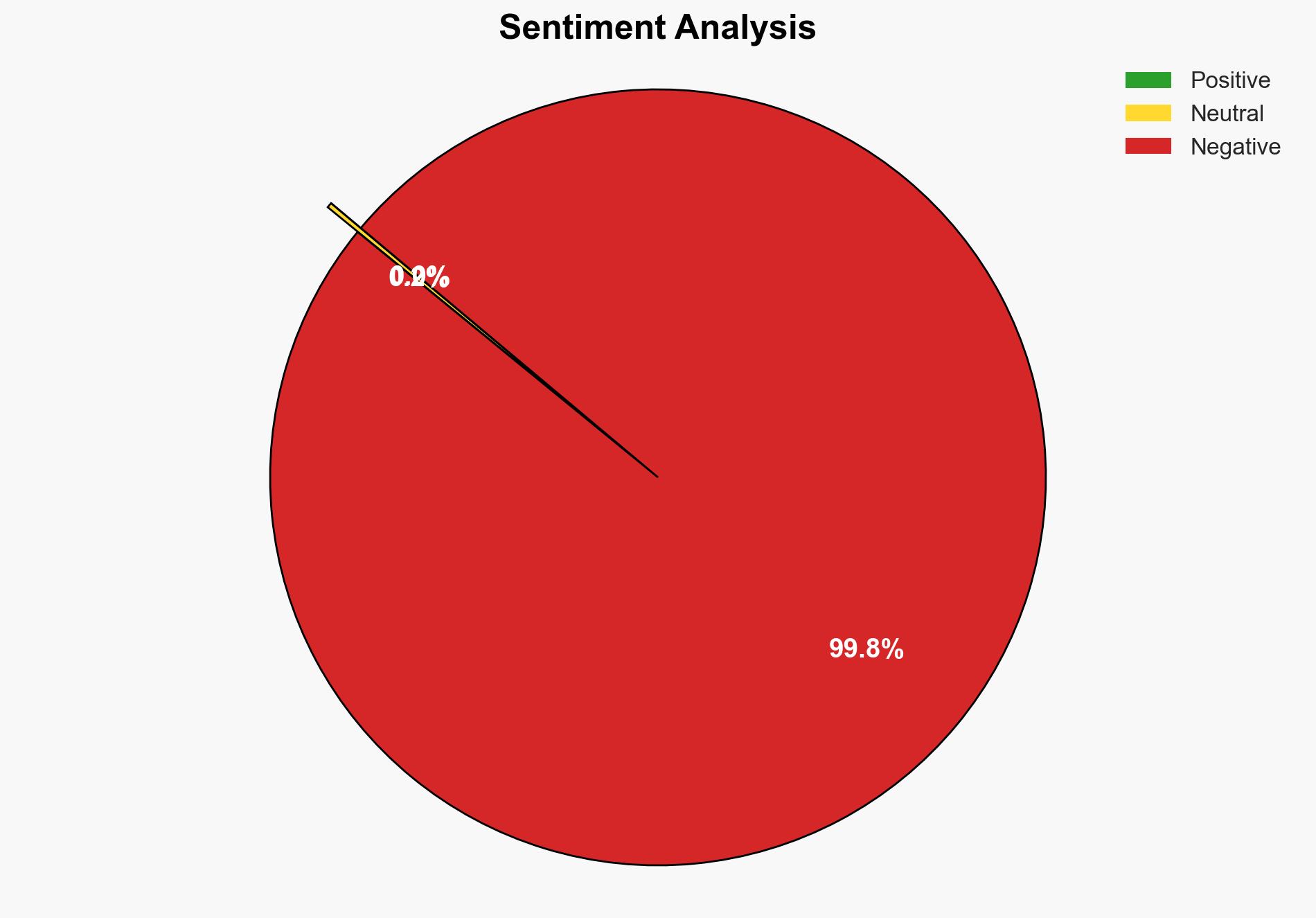
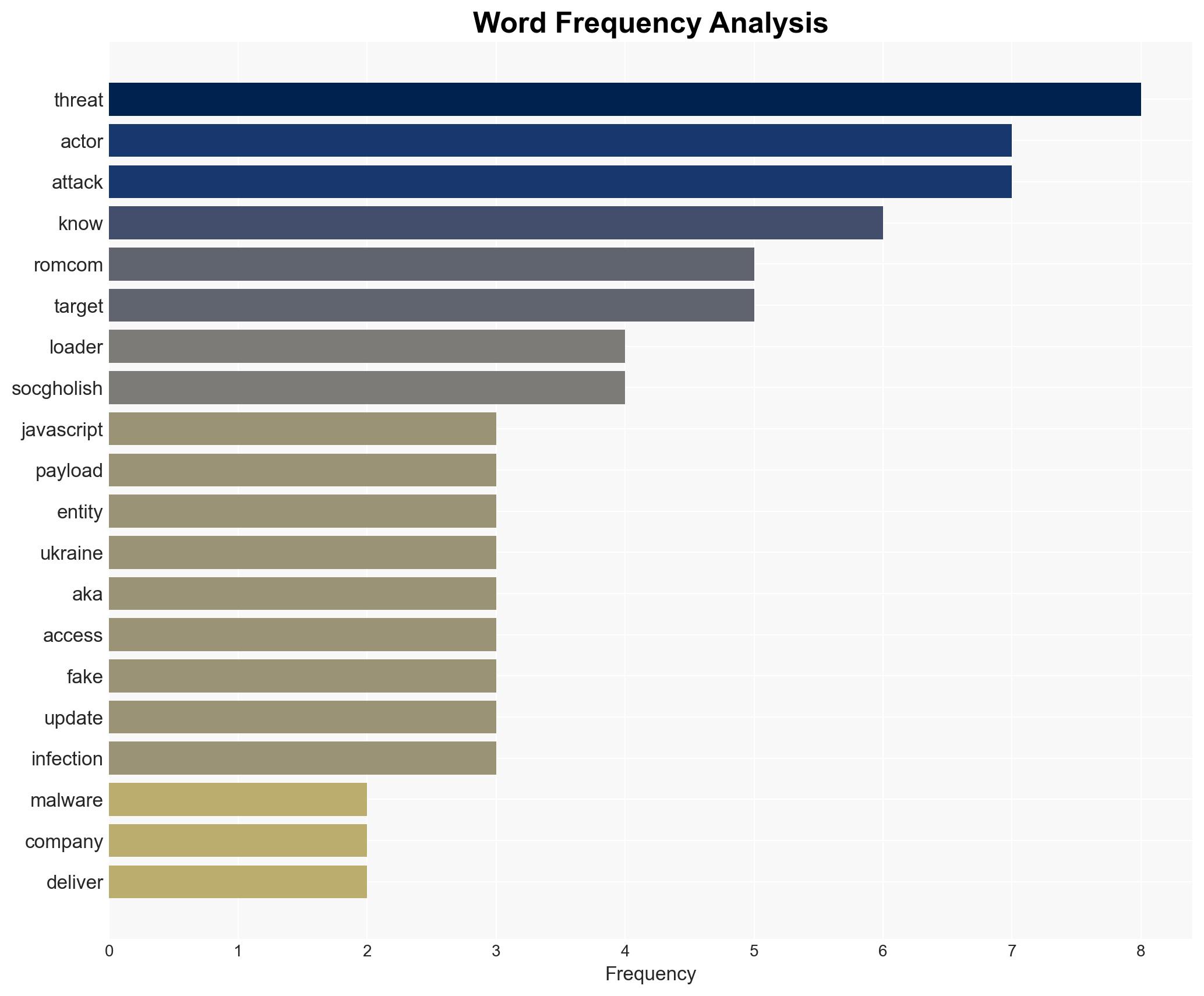
With medium-to-high confidence, it is assessed that the RomCom threat actor, potentially linked to Russia’s GRU, is leveraging SocGholish fake update attacks to target entities with ties to Ukraine. The strategic recommendation is to enhance cybersecurity measures for organizations with geopolitical ties to Ukraine and to monitor for SocGholish-related activities.
2. Competing Hypotheses
Hypothesis 1: RomCom is a state-sponsored actor linked to Russia’s GRU, using SocGholish attacks to target Ukrainian-aligned entities for espionage purposes.
Hypothesis 2: RomCom is an independent cybercriminal group using SocGholish attacks for financial gain, with no direct state sponsorship, but opportunistically targeting entities with geopolitical significance.
Hypothesis 1 is more likely given the historical context of Russian cyber operations targeting Ukraine and the involvement of sophisticated tactics indicative of state-level resources.
3. Key Assumptions and Red Flags
Assumptions: The attribution to Russia’s GRU is based on past patterns and medium-to-high confidence assessments by cybersecurity firms. The assumption that RomCom’s targets are primarily geopolitical is based on the nature of the entities attacked.
Red Flags: The potential for misattribution due to the complex nature of cyber operations and the use of shared tools among different threat actors. The rapid progression of attacks could indicate a well-resourced adversary or a coordinated campaign.
4. Implications and Strategic Risks
The use of SocGholish attacks presents a significant cyber risk to organizations with ties to Ukraine, potentially leading to data breaches, espionage, and disruption of critical infrastructure. Politically, these activities could escalate tensions between Russia and Western nations, particularly if state sponsorship is confirmed. Economically, affected companies may face financial losses and reputational damage.
5. Recommendations and Outlook
- Enhance monitoring and incident response capabilities for organizations with geopolitical ties to Ukraine.
- Implement robust cybersecurity training to recognize and mitigate phishing and fake update attacks.
- Best-case scenario: Increased awareness and preventive measures reduce the impact of attacks.
- Worst-case scenario: Escalation of cyber operations leads to broader geopolitical tensions and economic disruptions.
- Most-likely scenario: Continued targeted attacks with periodic successes, necessitating ongoing vigilance and adaptation of cybersecurity strategies.
6. Key Individuals and Entities
Jacob Fair (Arctic Wolf Labs researcher), RomCom (threat actor), SocGholish (malware family), GRU (Russia’s Directorate General Staff of the Armed Forces).
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us