RondoDox Botnet Exploits React2Shell Flaw to Compromise Over 90,000 Unsecured Devices Worldwide
Published on: 2026-01-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: RondoDox Botnet is Using React2Shell to Hijack Thousands of Unpatched Devices
1. BLUF (Bottom Line Up Front)
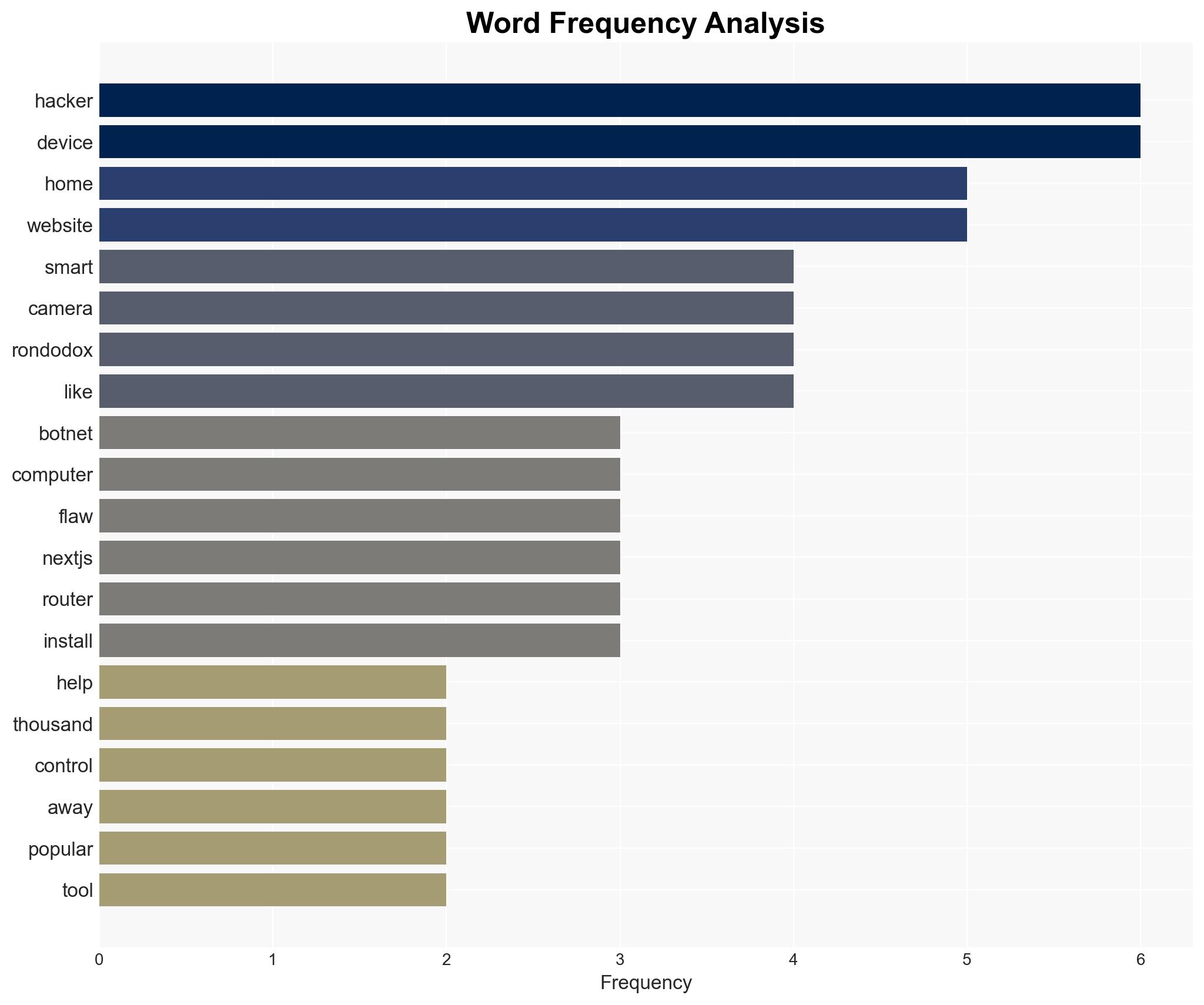
The RondoDox botnet is exploiting the React2Shell vulnerability to hijack over 90,000 devices, primarily in the US, Germany, France, and India. The botnet targets devices using Next.js, WordPress, and various home routers, posing a significant cyber threat. The most likely hypothesis is that this is a coordinated cybercriminal operation aimed at expanding botnet capabilities for financial gain. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The RondoDox botnet is primarily a financially motivated cybercriminal operation aiming to exploit hijacked devices for cryptocurrency mining and other illicit activities. This is supported by the use of malware components designed for resource exploitation and the widespread targeting of vulnerable devices.
- Hypothesis B: The botnet may be a state-sponsored operation intended to create a large-scale network for potential cyber warfare or espionage activities. This is less supported due to the lack of direct evidence linking the operation to state actors and the focus on financial exploitation tools.
- Assessment: Hypothesis A is currently better supported due to the operational focus on cryptocurrency mining and the absence of indicators of state-level strategic objectives. Key indicators that could shift this judgment include evidence of data exfiltration or targeting of critical infrastructure.
3. Key Assumptions and Red Flags
- Assumptions: The RondoDox group is primarily financially motivated; the React2Shell vulnerability remains unpatched in a significant number of devices; the botnet’s growth is driven by automated exploitation techniques.
- Information Gaps: Specific identities and affiliations of the RondoDox operators; detailed technical analysis of the malware variants used; comprehensive impact assessment on affected networks.
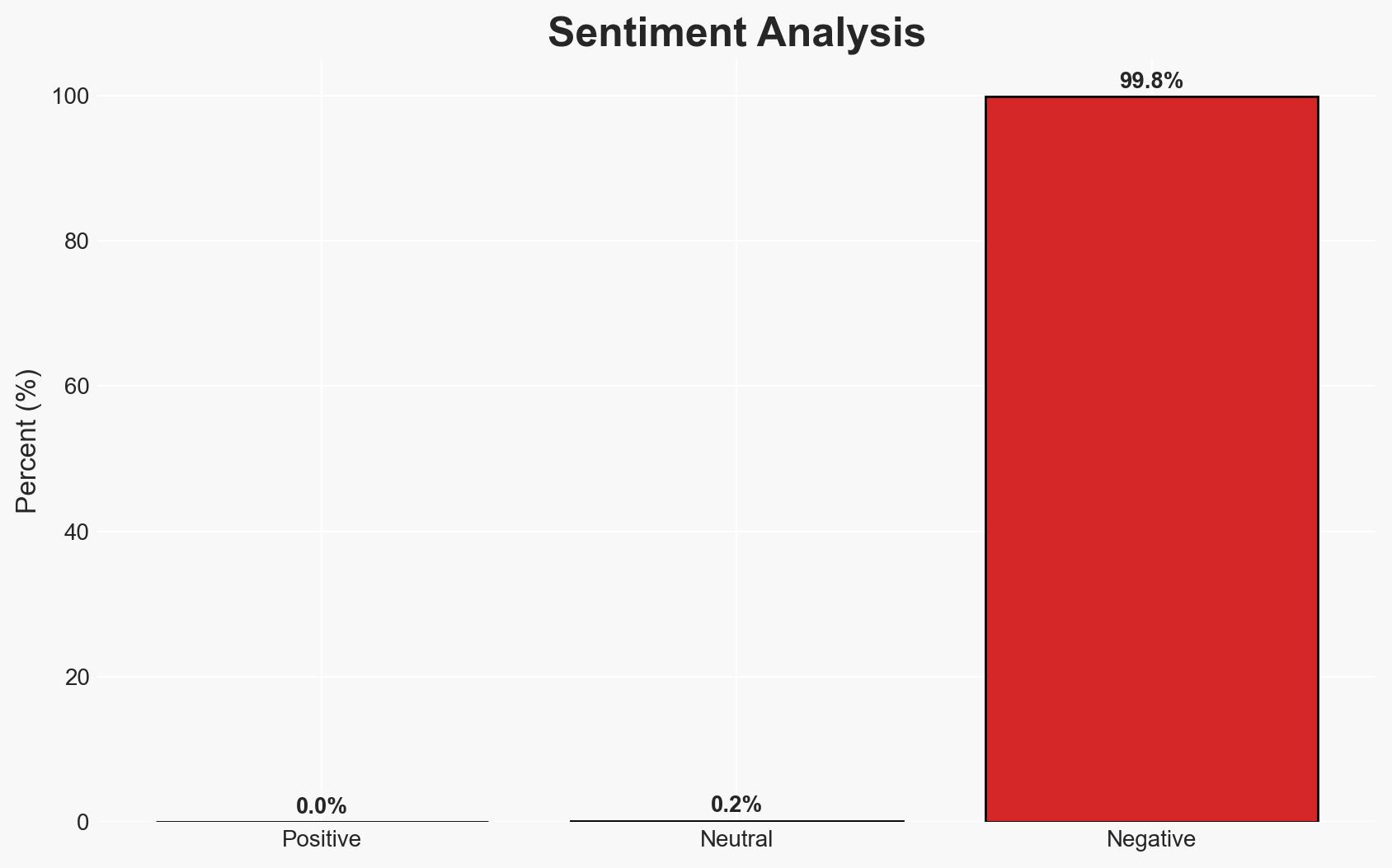
- Bias & Deception Risks: Potential bias in attributing motivations without direct evidence; deception risk from the attackers using false flags to mask true intentions.
4. Implications and Strategic Risks
This development could lead to increased cybercrime activities and strain on cybersecurity resources. If unaddressed, it may encourage similar operations by other groups.
- Political / Geopolitical: Potential diplomatic tensions if state-sponsored involvement is suspected or confirmed.
- Security / Counter-Terrorism: Increased cyber threat landscape complexity, requiring enhanced defensive measures.
- Cyber / Information Space: Escalation in cybercrime sophistication and automation, challenging existing cybersecurity frameworks.
- Economic / Social: Potential economic impact from disrupted services and increased cybersecurity costs for businesses and individuals.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgent patching of vulnerable systems, increased monitoring of affected networks, and public awareness campaigns on cybersecurity hygiene.
- Medium-Term Posture (1–12 months): Strengthen international collaboration on cyber threat intelligence sharing, invest in advanced threat detection technologies, and enhance regulatory frameworks for cybersecurity compliance.
- Scenario Outlook:
- Best: Rapid patch deployment and international cooperation mitigate the threat, reducing botnet impact.
- Worst: Botnet expands, leading to significant disruptions and financial losses.
- Most-Likely: Continued exploitation with periodic disruptions, necessitating ongoing defensive efforts.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, botnet, cybercrime, vulnerability exploitation, financial crime, malware, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us