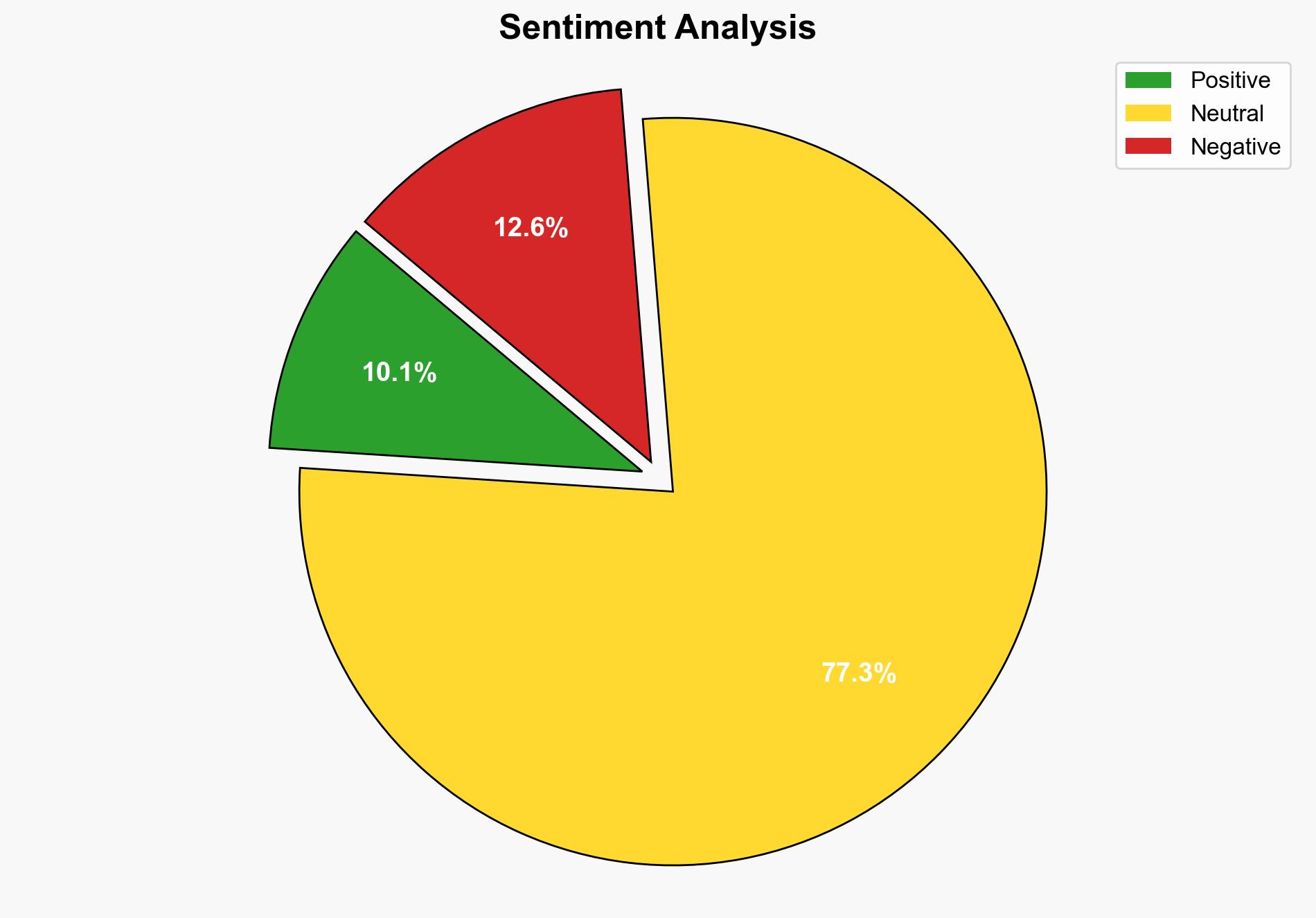
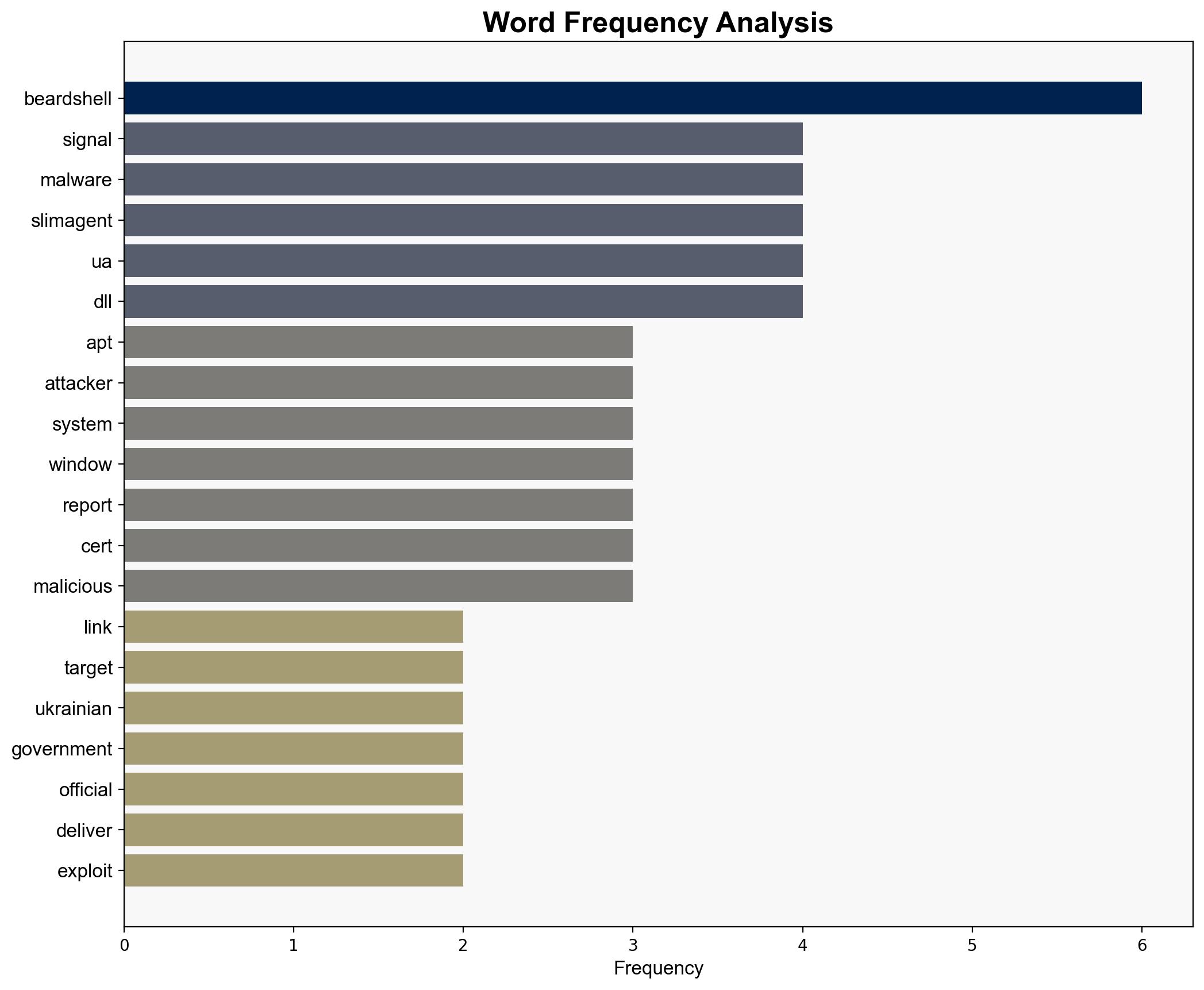
Russia-linked APT28 use Signal chats to target Ukraine official with malware – Securityaffairs.com
Published on: 2025-06-24
Intelligence Report: Russia-linked APT28 use Signal chats to target Ukraine official with malware – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
APT28, a Russia-linked cyberespionage group, has exploited Signal chats to deliver advanced malware, Beardshell and SlimAgent, targeting a Ukrainian government official. The attack leverages Signal’s popularity for secure communication, using phishing tactics to distribute malware. Key recommendations include enhancing monitoring of network traffic and strengthening defenses against phishing attempts.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated actions of APT28 reveal vulnerabilities in communication systems, emphasizing the need for improved resilience strategies.
Indicators Development
Identified anomalies include unauthorized access to email accounts and the use of legitimate cloud services for covert operations.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of similar future attacks, necessitating proactive defense measures.
Network Influence Mapping
Mapped relationships indicate APT28’s significant impact on regional cybersecurity dynamics.
3. Implications and Strategic Risks
The use of legitimate communication platforms like Signal for malware delivery represents a growing threat vector. This tactic could lead to increased distrust in secure communication tools, impacting political and military communication channels. The potential for cascading effects across cybersecurity and national security domains is significant.
4. Recommendations and Outlook
- Enhance network monitoring to detect unusual traffic patterns associated with cloud services like Icedrive and Koofr.
- Implement robust phishing awareness and training programs to reduce susceptibility to social engineering attacks.
- Scenario-based projections:
- Best Case: Strengthened defenses prevent further breaches, maintaining trust in secure communication tools.
- Worst Case: Continued exploitation leads to widespread distrust in secure platforms, compromising sensitive communications.
- Most Likely: Incremental improvements in cybersecurity posture mitigate some risks, but persistent threats remain.
5. Key Individuals and Entities
Specific individuals involved in the attack remain unidentified. APT28 is the primary entity of concern.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus