Russian-aligned hacktivist groups intensify cyber attacks on UK entities and critical infrastructure
Published on: 2026-01-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pro-Russian hacktivist campaigns continue against UK organizations
1. BLUF (Bottom Line Up Front)
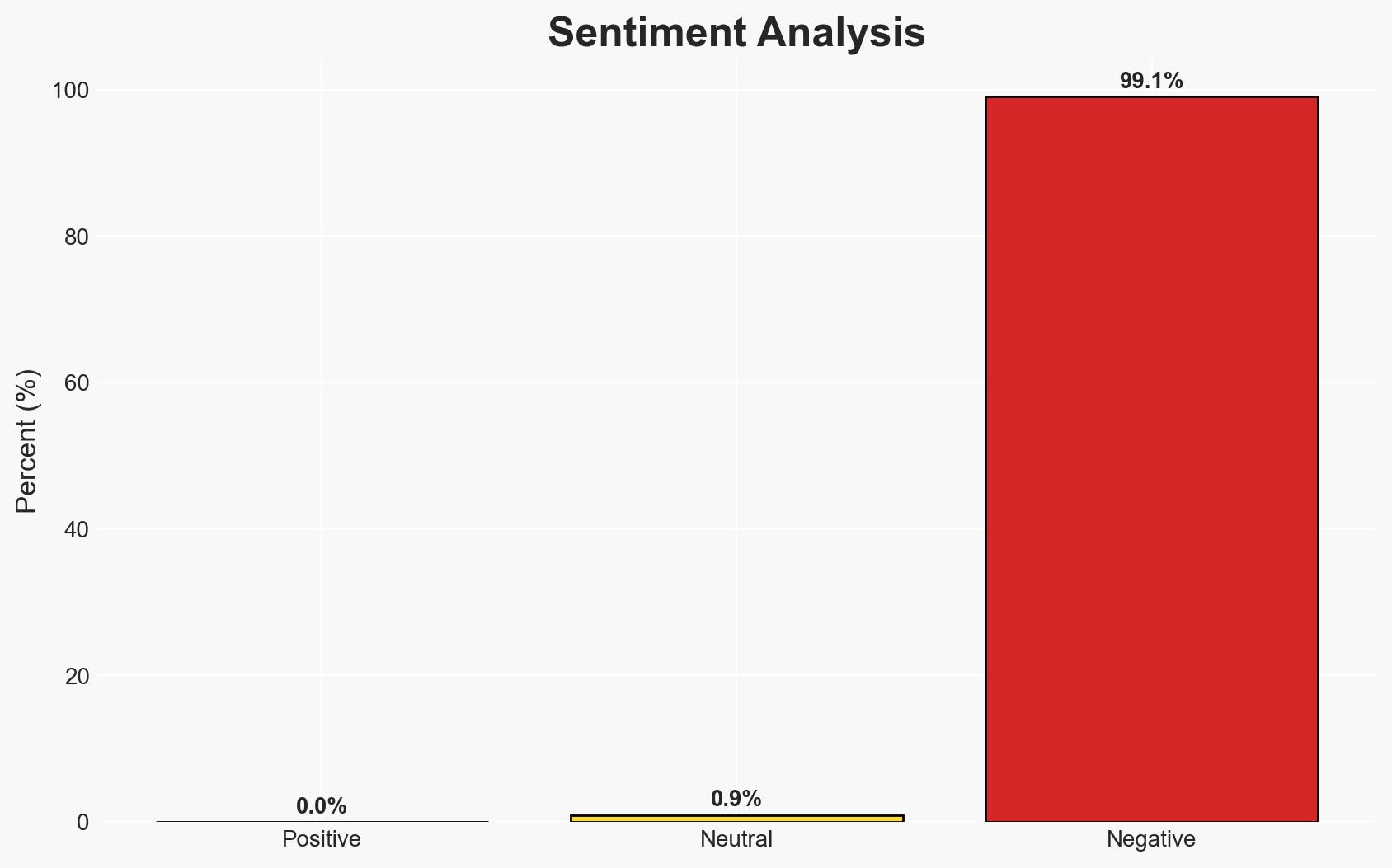
Pro-Russian hacktivist groups, notably NoName057(16), are actively targeting UK organizations, including local government bodies, primarily through DDoS attacks. This activity aligns with broader Russian geopolitical interests and poses a strategic concern due to its potential to disrupt critical infrastructure. The UK is responding with enhanced cybersecurity measures. Overall, there is moderate confidence in the assessment that these campaigns will intensify in frequency and impact throughout 2026.
2. Competing Hypotheses
- Hypothesis A: The hacktivist campaigns are primarily driven by state-aligned objectives to disrupt and destabilize UK infrastructure as part of a broader geopolitical strategy. This is supported by the alignment with Russian interests and the targeting of NATO member states. However, the degree of direct state control remains uncertain.
- Hypothesis B: The campaigns are largely independent actions by hacktivist groups seeking notoriety and influence, with only indirect alignment with state narratives. This is suggested by the use of public platforms like Telegram for coordination, which may indicate a decentralized structure.
- Assessment: Hypothesis A is currently better supported due to the strategic nature of the targets and the alignment with Russian geopolitical objectives. Indicators such as increased sophistication or direct links to state actors could further support this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: Hacktivist groups have the capability to sustain and escalate attacks; Russian geopolitical interests align with these cyber activities; UK defenses are currently insufficient to fully mitigate these threats.
- Information Gaps: The extent of direct Russian state involvement or support; detailed motivations and internal dynamics of the hacktivist groups; specific vulnerabilities exploited in UK infrastructure.
- Bias & Deception Risks: Potential bias in attributing attacks to state-aligned actors without conclusive evidence; risk of overestimating the threat based on publicized incidents; possible misinformation from hacktivist communications.
4. Implications and Strategic Risks
The continuation and potential escalation of hacktivist campaigns against UK entities could have significant implications across multiple domains.
- Political / Geopolitical: Increased tensions between the UK and Russia, potential for retaliatory measures or diplomatic fallout.
- Security / Counter-Terrorism: Heightened threat environment, necessitating increased cybersecurity measures and potential military or intelligence responses.
- Cyber / Information Space: Escalation in cyber warfare tactics, potential for more sophisticated attacks on critical infrastructure.
- Economic / Social: Disruption of public services, potential economic impact from sustained cyberattacks, erosion of public trust in digital services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of hacktivist communications, strengthen DDoS defenses, and conduct vulnerability assessments of critical infrastructure.
- Medium-Term Posture (1–12 months): Develop public-private partnerships for cybersecurity, invest in advanced threat detection technologies, and enhance international cooperation for cyber defense.
- Scenario Outlook:
- Best Case: Successful mitigation of attacks with minimal disruption, leading to decreased hacktivist activity.
- Worst Case: Significant disruption to critical infrastructure, leading to economic and social instability.
- Most-Likely: Continued sporadic attacks with moderate disruption, necessitating ongoing cybersecurity enhancements.
6. Key Individuals and Entities
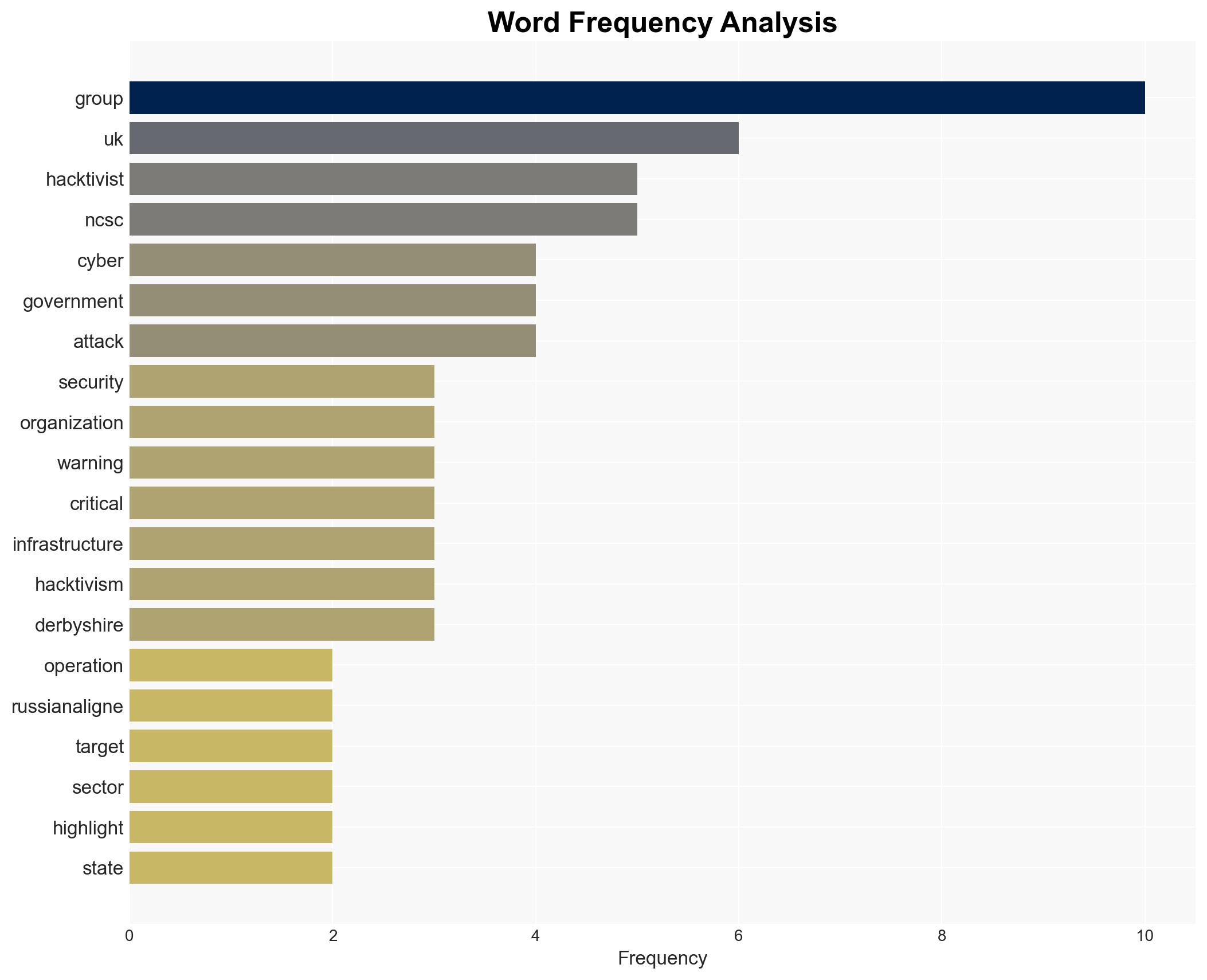
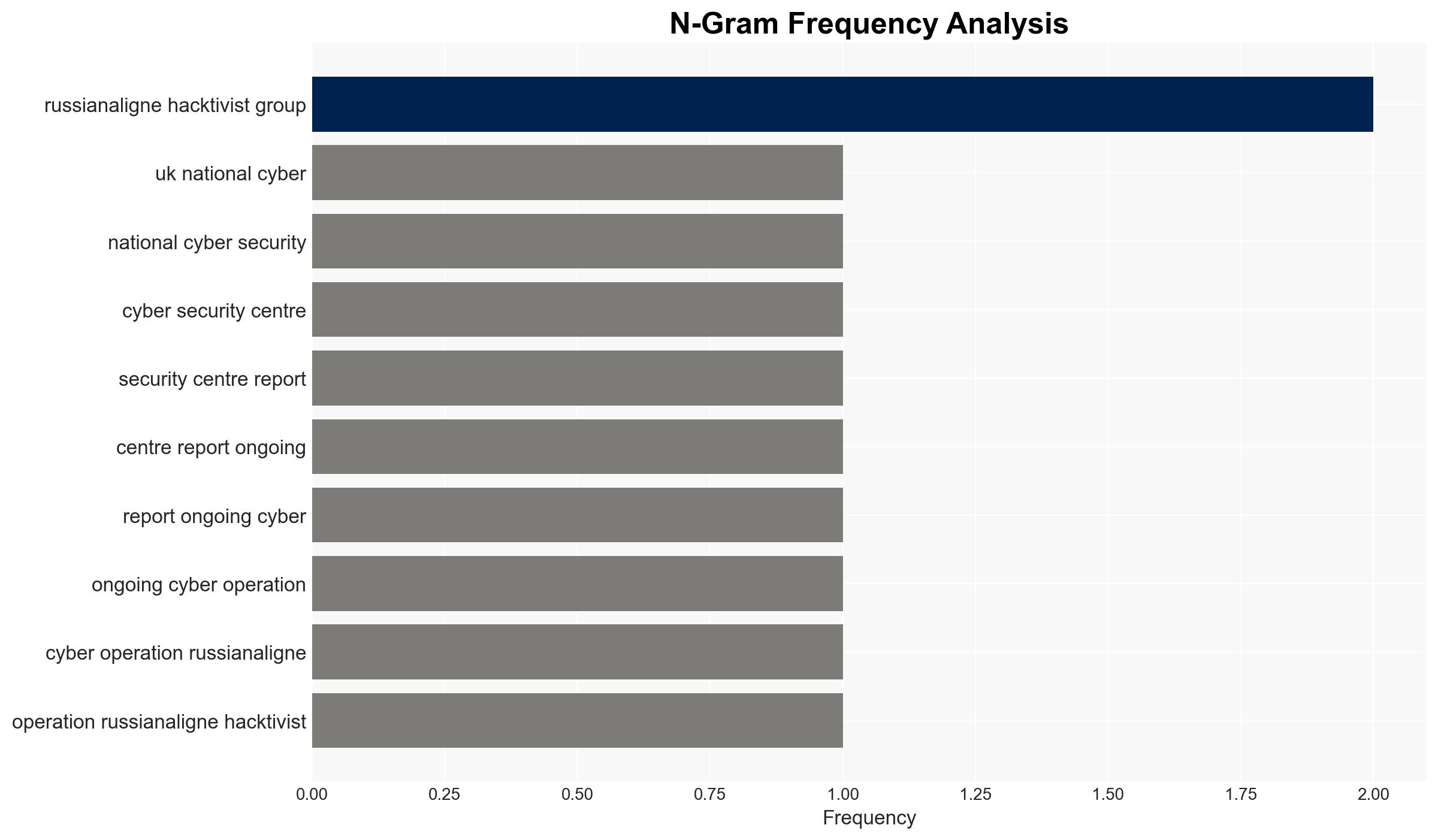
- NoName057(16) – Pro-Russian hacktivist group
- UK National Cyber Security Centre (NCSC) – UK cybersecurity authority
- Dr. Ric Derbyshire – Principal Security Researcher, Orange Cyberdefense
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, cybersecurity, hacktivism, Russian geopolitical strategy, critical infrastructure, DDoS attacks, UK national security, cyber defense
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us