Russian GRU Hackers Shift Tactics to Exploit Misconfigured Devices in Critical Infrastructure Attacks
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Amazon Russian GRU hackers favor misconfigured devices over vulnerabilities
1. BLUF (Bottom Line Up Front)
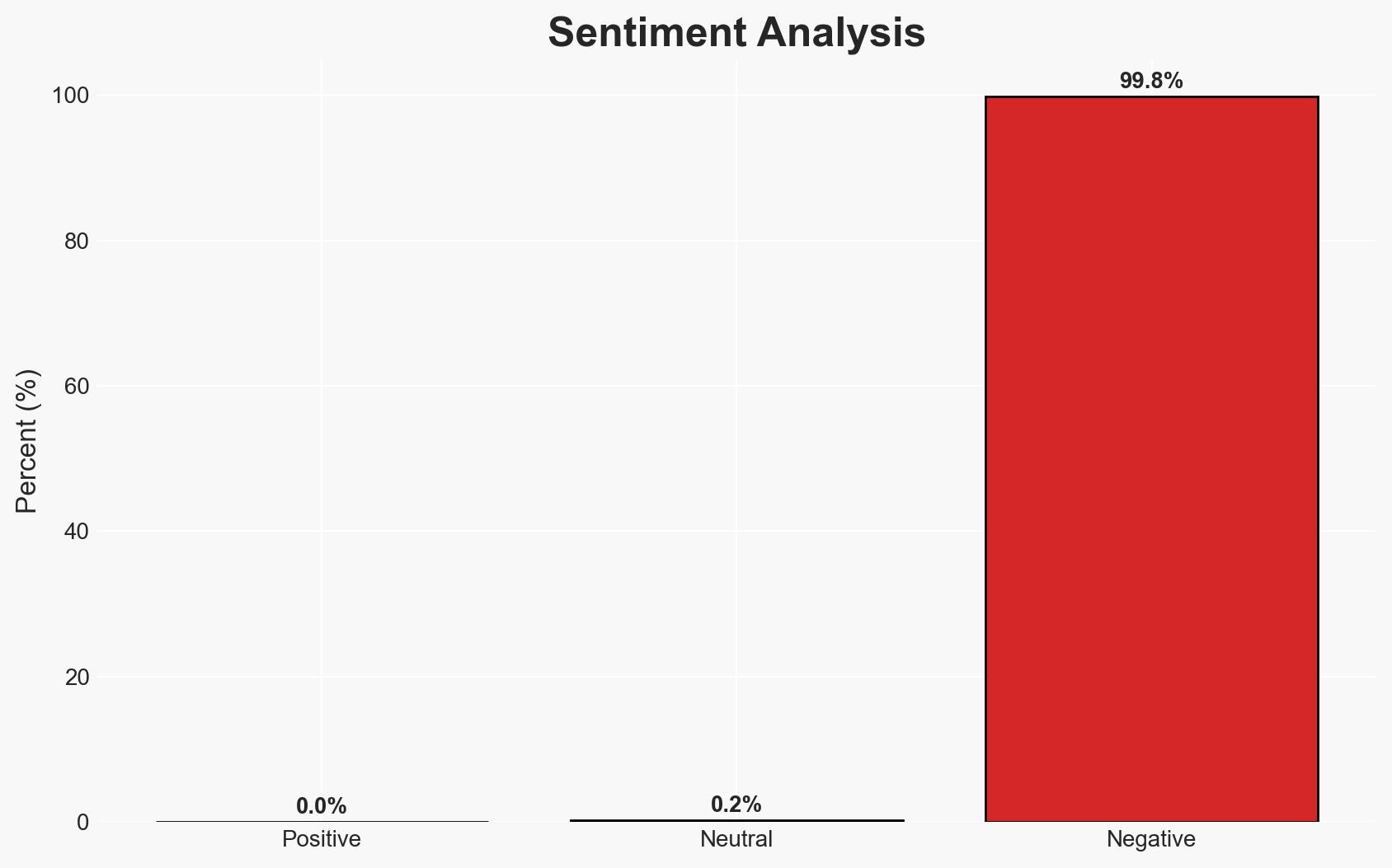
Russian GRU-linked threat actors, specifically the Sandworm group, are increasingly exploiting misconfigured network devices to breach critical infrastructure, particularly in the energy sector across North America and Europe. This shift from exploiting software vulnerabilities to targeting configuration errors represents a strategic adaptation to evade detection. The assessment is made with moderate confidence due to the reliance on open-source intelligence and potential gaps in data.
2. Competing Hypotheses
- Hypothesis A: The GRU-linked actors have shifted their tactics to exploit misconfigured devices due to increased effectiveness and lower risk of detection. This is supported by observed declines in vulnerability exploitation and increased targeting of network edge devices.
- Hypothesis B: The observed shift is a temporary adaptation due to recent improvements in software patching and vulnerability management, forcing actors to seek alternative access methods. This is less supported as it does not account for the sustained nature of the campaign.
- Assessment: Hypothesis A is currently better supported due to consistent patterns of activity and the strategic advantage of targeting misconfigurations. Indicators such as changes in patch management effectiveness or new vulnerability disclosures could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: GRU actors have the capability to exploit misconfigurations; energy sector remains a primary target; misconfigured devices are prevalent in cloud environments.
- Information Gaps: Specific details on the scale of misconfigured devices; full scope of compromised infrastructure; potential undisclosed vulnerabilities.
- Bias & Deception Risks: Potential bias in attributing activity solely to GRU; reliance on vendor-specific threat intelligence; risk of adversary deception in masking true objectives.
4. Implications and Strategic Risks
The exploitation of misconfigured devices by GRU-linked actors could lead to increased vulnerabilities in critical infrastructure, potentially disrupting essential services and causing geopolitical tensions.
- Political / Geopolitical: Potential for increased tensions between Russia and affected nations, leading to diplomatic confrontations or sanctions.
- Security / Counter-Terrorism: Heightened threat to critical infrastructure security, necessitating enhanced defensive measures.
- Cyber / Information Space: Increased focus on securing network configurations and identity management; potential for misinformation campaigns leveraging compromised systems.
- Economic / Social: Disruptions in energy supply chains could impact economic stability and social cohesion, particularly in affected regions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct audits of network configurations in critical infrastructure; enhance monitoring for misconfiguration exploitation; engage with cloud service providers for security posture assessments.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on misconfiguration threats; invest in training for secure configuration management; strengthen identity and access management protocols.
- Scenario Outlook:
- Best: Rapid mitigation of misconfigurations leads to decreased breach incidents.
- Worst: Continued exploitation results in significant infrastructure disruptions.
- Most-Likely: Gradual improvement in security posture reduces but does not eliminate threat activity.
6. Key Individuals and Entities
- Sandworm (APT44, Seashell Blizzard)
- Curly COMrades
- CJ Moses, CISO of Amazon
- Chrissa Constantine, Senior Cybersecurity Solution Architect at Black Duck
- Shane Barney, Chief Information Security Officer at Keeper Security
7. Thematic Tags
cybersecurity, cyber-espionage, critical infrastructure, GRU, misconfiguration exploitation, energy sector, network security, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us