SaaS Security Essentials Reducing Risks in Cloud Applications – HackRead
Published on: 2025-04-11
Intelligence Report: SaaS Security Essentials Reducing Risks in Cloud Applications – HackRead
1. BLUF (Bottom Line Up Front)
The increasing reliance on SaaS applications necessitates robust security measures to protect sensitive data, user access, and cloud infrastructure. Key findings indicate that a multi-layered security approach is essential, incorporating identity and access management, data protection, secure development practices, network security, and incident response planning. Recommendations focus on enhancing encryption, access controls, and secure configurations to mitigate risks.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The reliance on SaaS applications exposes organizations to various cybersecurity threats. A secure SaaS architecture requires prioritizing key security components, including Identity and Access Management (IAM) with multi-factor authentication and single sign-on to prevent identity-based threats. Data protection through encryption and data loss prevention policies is critical to safeguarding sensitive information. Secure development practices, such as code reviews and automated security scanning, help identify vulnerabilities early in the development lifecycle. Network security measures, including firewalls and network segmentation, reduce the attack surface. An effective incident response plan ensures preparedness for potential security incidents.
3. Implications and Strategic Risks
The failure to implement comprehensive SaaS security measures poses significant risks to national security, regional stability, and economic interests. Unauthorized access, data breaches, and misconfigurations can lead to the compromise of sensitive information and disrupt operations. The growing trend of third-party vulnerabilities further exacerbates these risks, highlighting the need for continuous monitoring and management of SaaS applications.
4. Recommendations and Outlook
Recommendations:
- Enhance data encryption both at rest and in transit, ensuring secure management of encryption keys.
- Implement role-based access controls and regularly audit permissions to enforce the principle of least privilege.
- Regularly review and harden cloud configurations using tools like AWS Config, Azure Security Center, and GCP Security Command Center.
- Conduct regular incident response drills to ensure staff preparedness and effective incident management.
Outlook:
In the best-case scenario, organizations adopting comprehensive SaaS security measures will experience reduced incidents of data breaches and unauthorized access. In the worst-case scenario, failure to implement these measures could lead to significant data loss and operational disruptions. The most likely outcome involves a gradual improvement in security posture as organizations adopt recommended practices and technologies.
5. Key Individuals and Entities
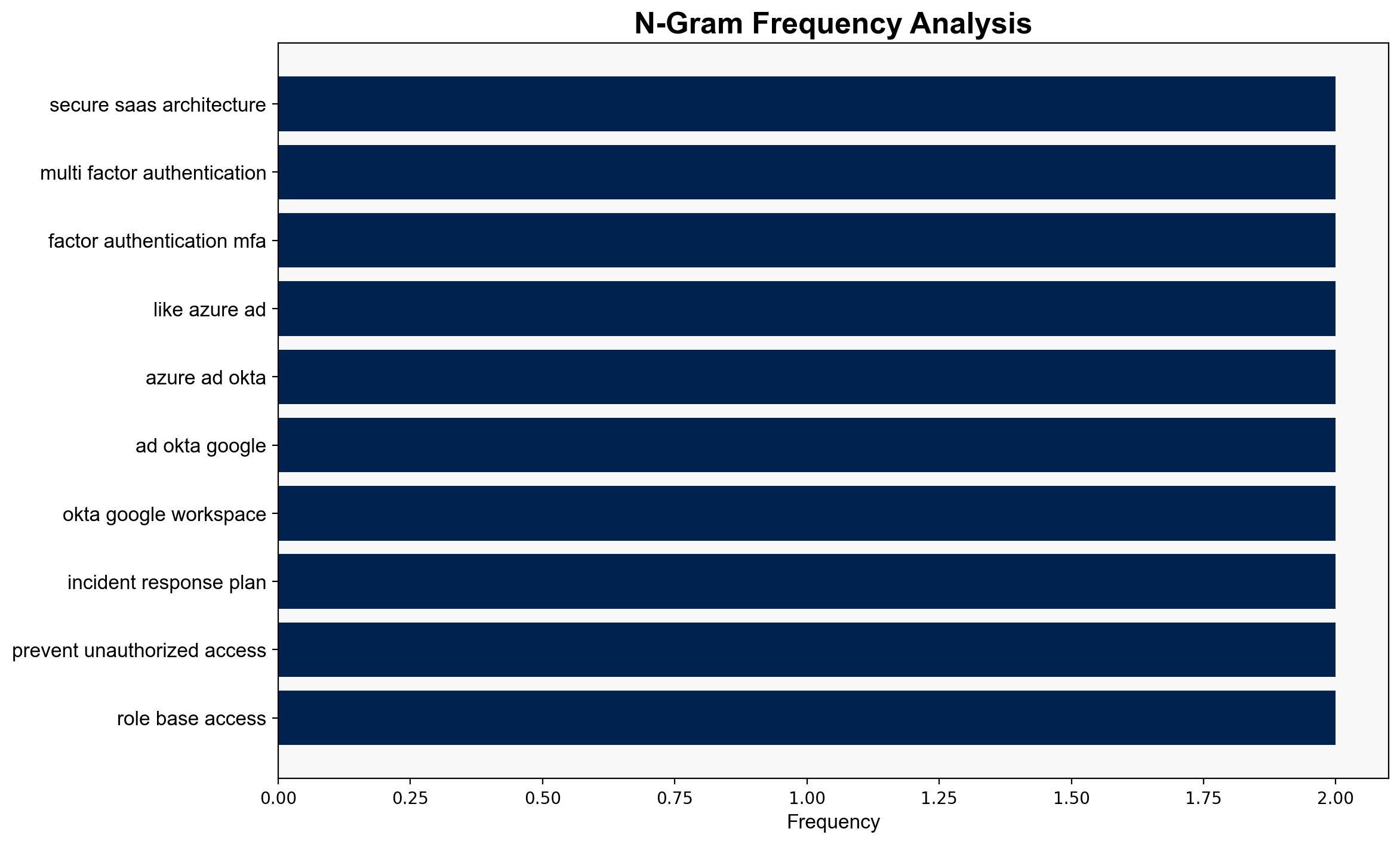
The report does not mention specific individuals or organizations by name. However, it emphasizes the importance of integrating identity providers such as Azure AD, Okta, and Google Workspace for centralized user authentication and authorization.