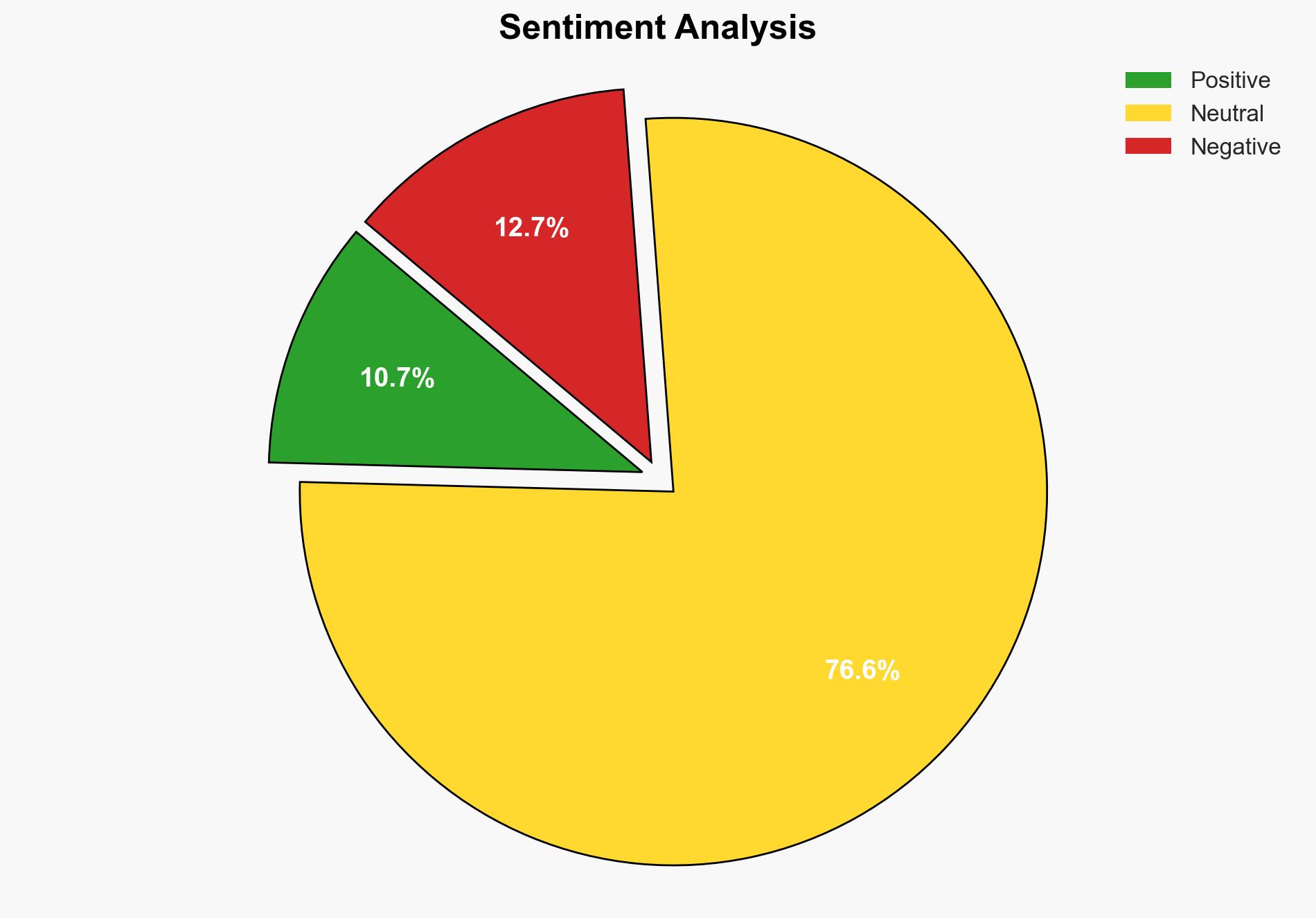
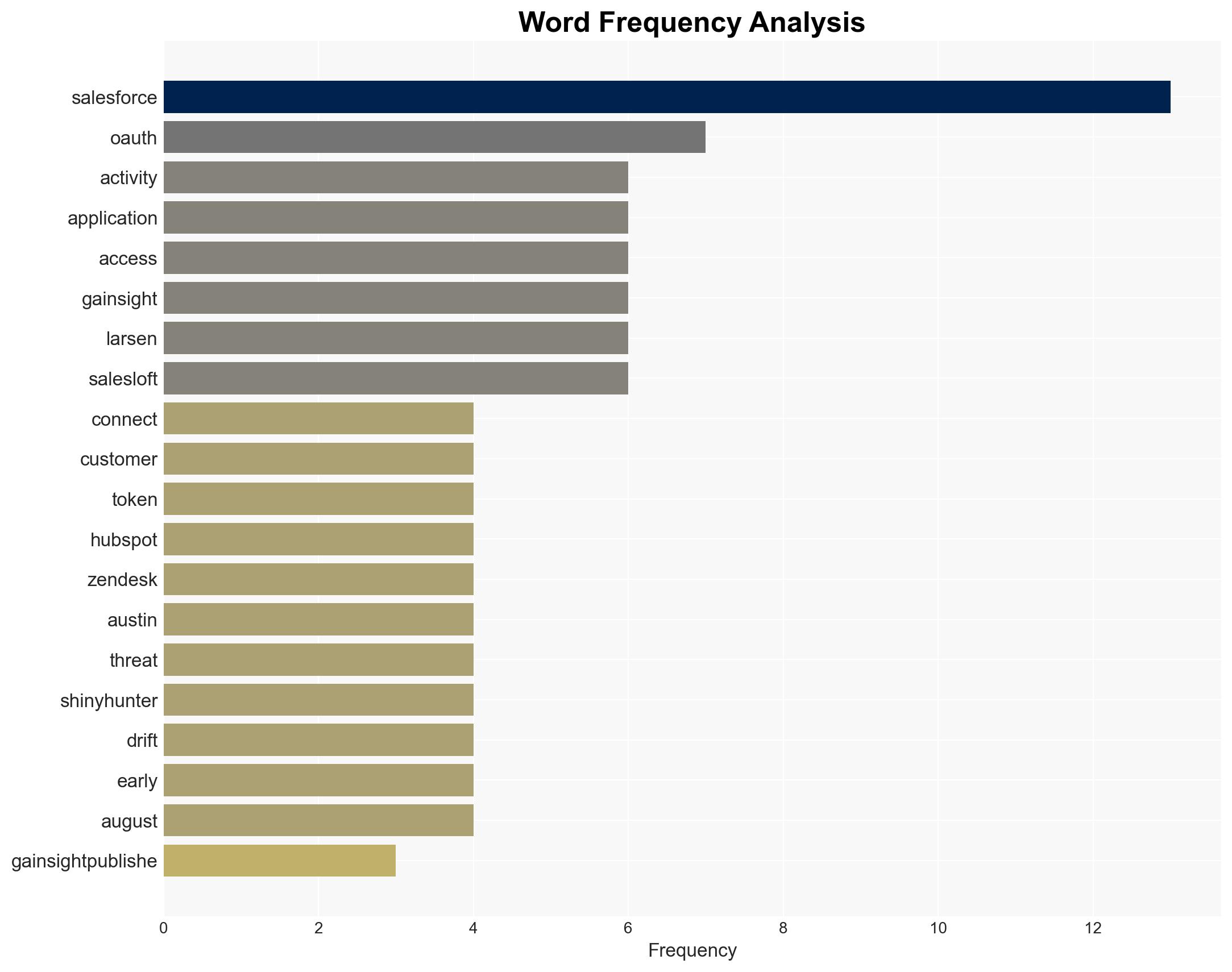
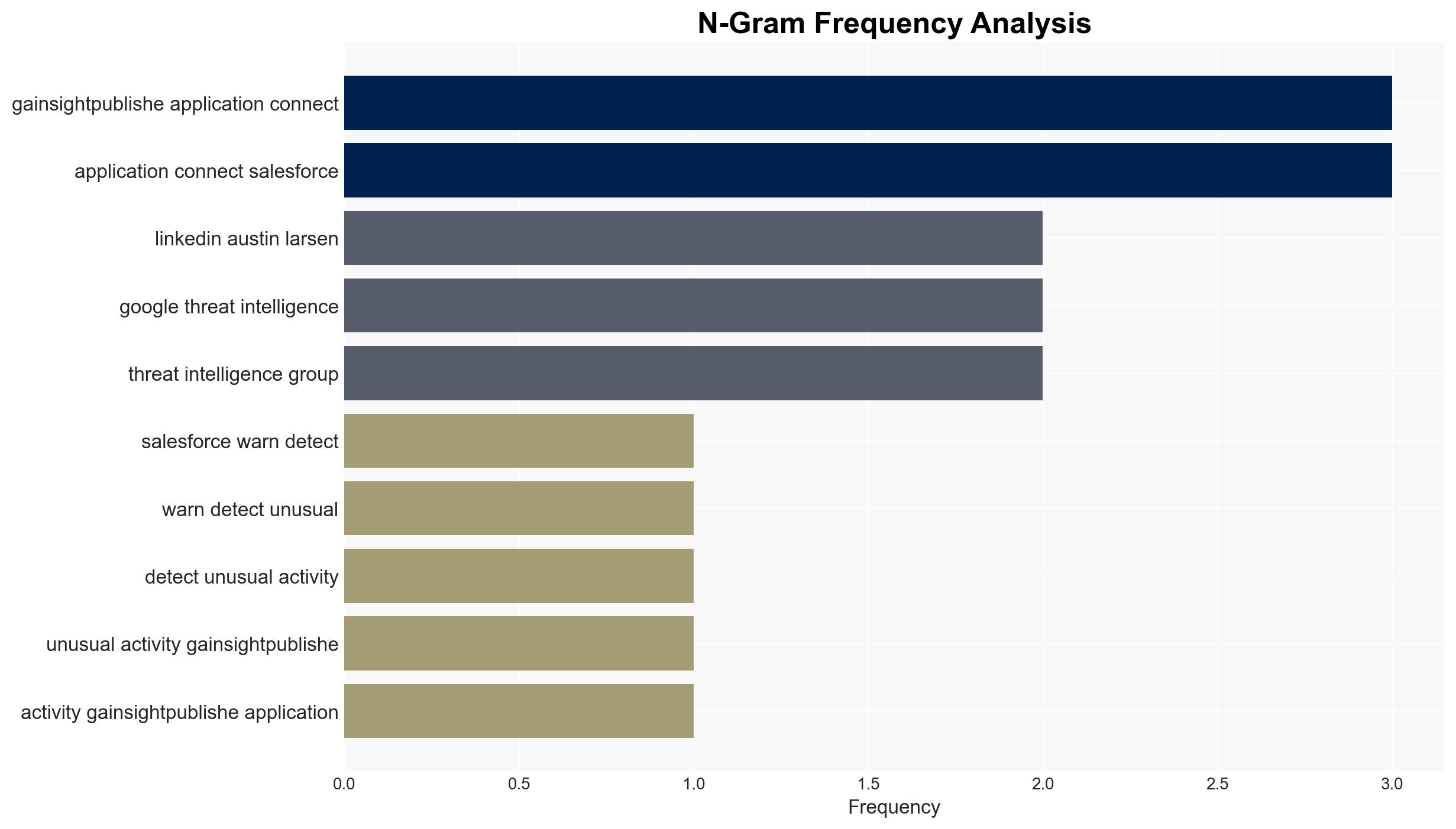
Salesforce Flags Unauthorized Data Access via Gainsight-Linked OAuth Activity – Internet
Published on: 2025-11-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
There is a moderate confidence level that the unauthorized data access via Gainsight-linked OAuth activity is part of a broader campaign by the ShinyHunters group, targeting third-party SaaS integrations to exploit OAuth tokens. Immediate action is recommended to revoke and rotate OAuth tokens, enhance monitoring, and conduct a comprehensive review of third-party applications connected to Salesforce.
2. Competing Hypotheses
Hypothesis 1: The incident is an isolated breach specifically targeting Gainsight’s integration with Salesforce, possibly due to a vulnerability in the Gainsight application itself.
Hypothesis 2: The incident is part of a coordinated campaign by the ShinyHunters group, leveraging OAuth token vulnerabilities across multiple platforms, including Salesforce, to gain unauthorized access to sensitive data.
Assessment: Hypothesis 2 is more likely given the pattern of similar attacks on Salesloft and Drift, and the known tactics of ShinyHunters. The involvement of multiple platforms and the strategic targeting of OAuth tokens suggest a broader campaign rather than an isolated incident.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the OAuth token vulnerabilities are the primary vector for unauthorized access. It is also assumed that ShinyHunters are the actors behind this campaign based on historical patterns.
Red Flags: The rapid removal of the Gainsight application from AppExchange and the advisory to revoke access tokens indicate a significant threat level. The lack of detailed disclosure on the specific vulnerability exploited is a concern.
Deception Indicators: Potential misinformation could arise if ShinyHunters or other actors attempt to obfuscate their involvement or the true extent of the breach.
4. Implications and Strategic Risks
The unauthorized access poses significant risks to customer data integrity and privacy, potentially leading to reputational damage for Salesforce and affected third-party applications. There is a risk of cascading cyber threats if OAuth token vulnerabilities are not addressed, potentially impacting other SaaS platforms and their customers. Economically, affected companies may face costs related to breach mitigation and potential legal actions.
5. Recommendations and Outlook
- Conduct a comprehensive audit of all third-party applications connected to Salesforce to identify and mitigate vulnerabilities.
- Enhance monitoring for suspicious OAuth activity and implement stricter access controls.
- Communicate transparently with affected customers and stakeholders to manage reputational risks.
- Best-case scenario: The breach is contained quickly, with minimal data exposure and strengthened security measures preventing future incidents.
- Worst-case scenario: The breach expands to other platforms, leading to widespread data exposure and significant financial and reputational damage.
- Most-likely scenario: The breach is part of a broader campaign, but swift action mitigates further damage, leading to improved security protocols across affected platforms.
6. Key Individuals and Entities
Austin Larsen – Principal Threat Analyst, Google Threat Intelligence Group
ShinyHunters – Cyber threat actor group
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us