Scammers are once again abusing PDFs to trick victims into calling fake support numbers – TechRadar
Published on: 2025-07-03
Intelligence Report: Scammers are once again abusing PDFs to trick victims into calling fake support numbers – TechRadar
1. BLUF (Bottom Line Up Front)
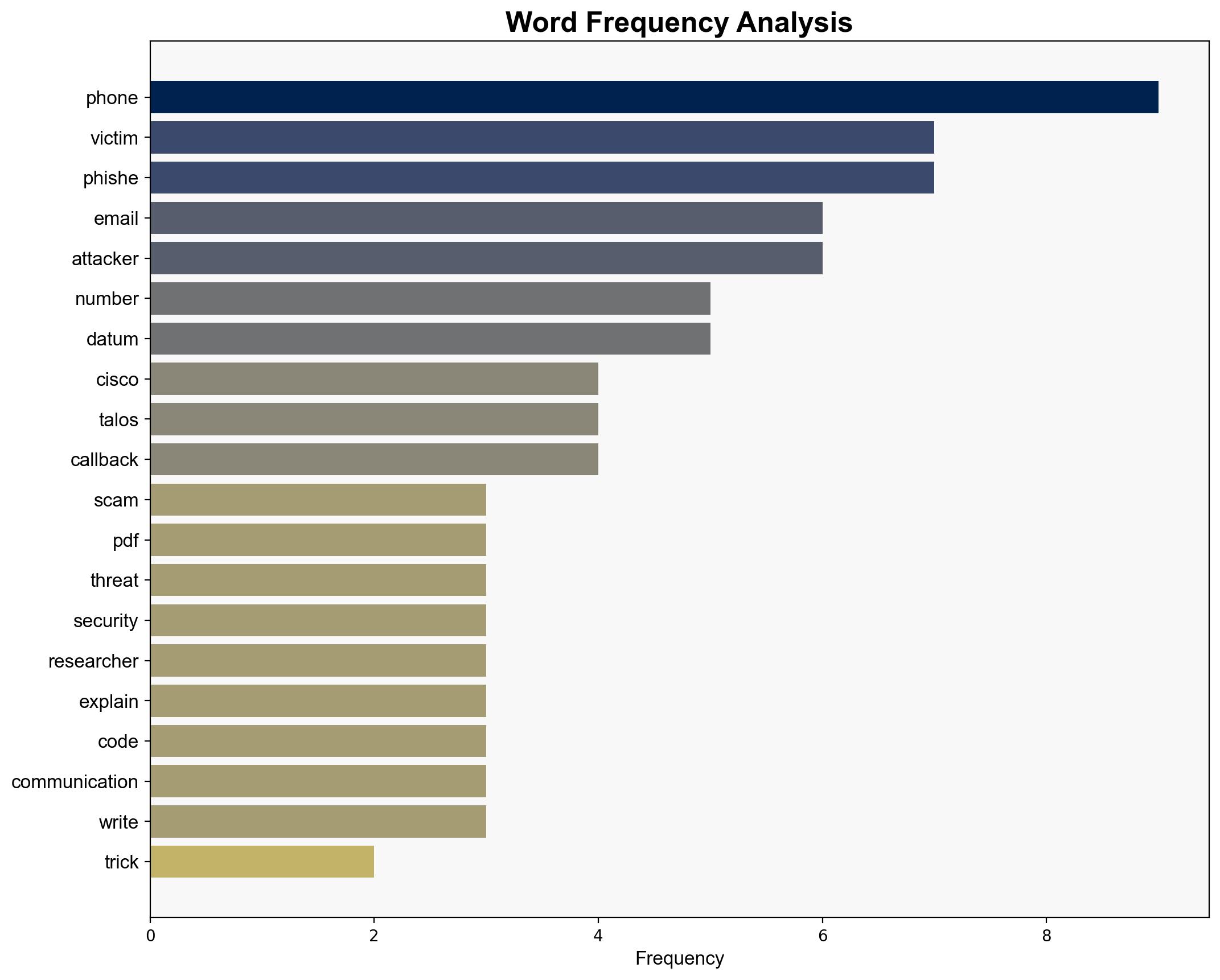
Recent reports indicate a resurgence in phishing scams utilizing PDF attachments to deceive victims into calling fraudulent support numbers. These scams exploit the perceived security of phone communications, posing significant risks to personal and organizational data security. Immediate countermeasures are recommended to enhance email filtering and user awareness.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Scammers are simulating legitimate customer service interactions by embedding phone numbers in PDF attachments, bypassing traditional email security measures. This tactic exploits users’ trust in phone communications.
Indicators Development
Key indicators include unexpected PDF attachments in emails, requests for phone communication, and the inclusion of QR codes. Monitoring these can aid in early detection of phishing attempts.
Bayesian Scenario Modeling
Probabilistic models suggest an increased likelihood of these scams evolving to incorporate more sophisticated social engineering tactics, potentially targeting larger organizations.
3. Implications and Strategic Risks
The rise in PDF-based phishing scams highlights vulnerabilities in email security systems and user awareness. This trend could lead to increased data breaches and financial losses, affecting both individuals and businesses. The cross-domain risk includes potential impacts on national security if sensitive information is compromised.
4. Recommendations and Outlook
- Enhance email filtering systems to detect and block suspicious PDF attachments.
- Conduct regular user training to recognize phishing attempts and understand the risks of unsolicited phone communications.
- Implement multi-factor authentication to safeguard sensitive data.
- Scenario-based projections suggest that without intervention, these scams will likely increase in sophistication and frequency.
5. Key Individuals and Entities
Cisco Talos researchers have been instrumental in identifying and analyzing these phishing campaigns. Their findings are crucial for developing effective countermeasures.
6. Thematic Tags
national security threats, cybersecurity, phishing scams, PDF-based attacks, social engineering