Scammers Use Fake Invitations to Covertly Install Remote Access Software on Victims’ Computers
Published on: 2026-02-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: How fake party invitations are being used to install remote access tools
1. BLUF (Bottom Line Up Front)
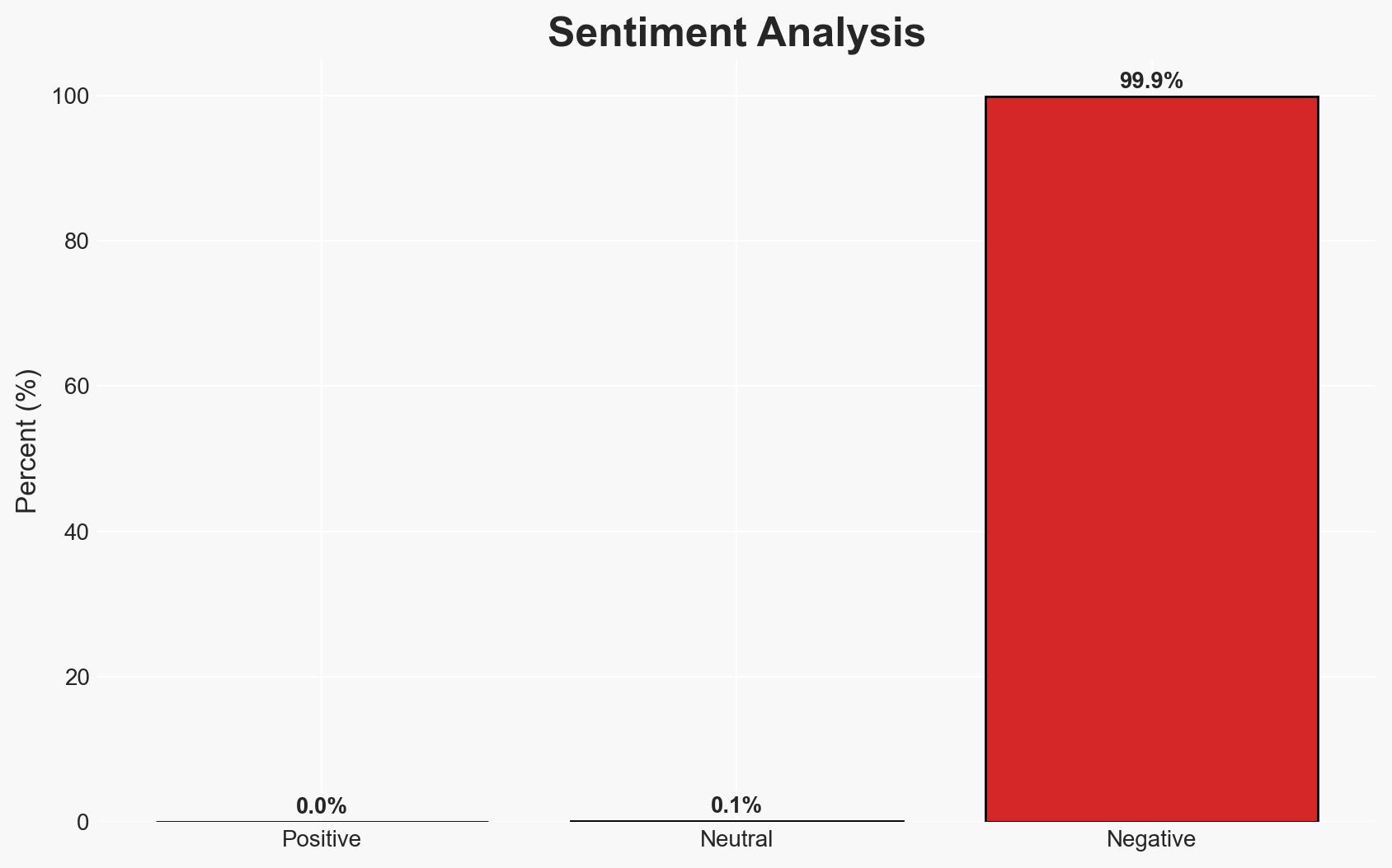
The use of fake party invitations to install remote access tools represents a sophisticated social engineering attack primarily affecting individuals in the UK, with potential for broader geographic spread. The campaign exploits trust in personal communications to gain unauthorized access to victims’ systems. The most likely hypothesis is that this operation is a financially motivated cybercrime campaign. Overall confidence in this assessment is moderate due to limited geographic scope and lack of attribution to specific threat actors.
2. Competing Hypotheses
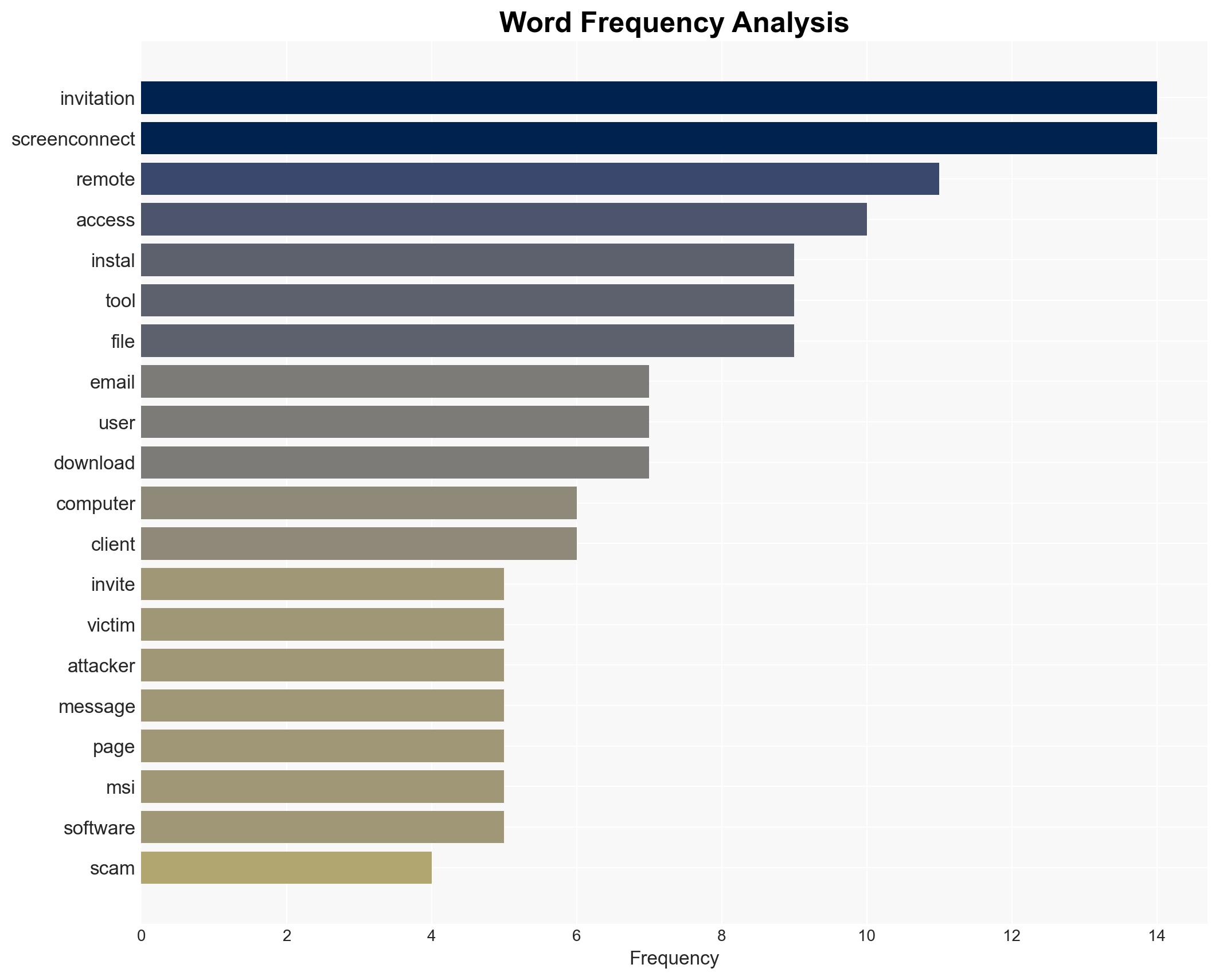
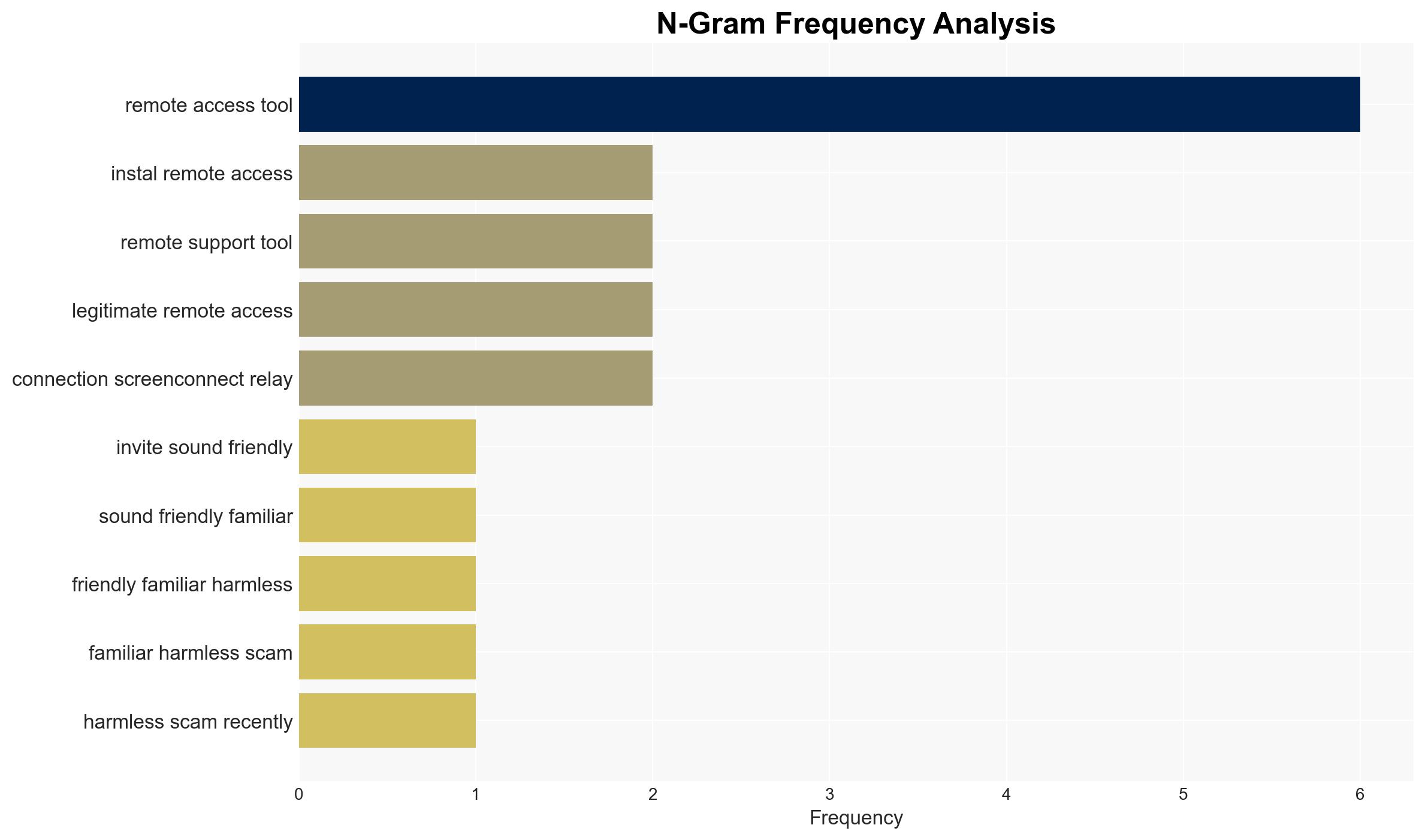
- Hypothesis A: The campaign is a financially motivated cybercrime operation targeting individuals to gain access to sensitive personal data for fraud. This is supported by the use of legitimate software (ScreenConnect) and the focus on personal email accounts. Key uncertainties include the identity of the attackers and their ultimate objectives.
- Hypothesis B: The operation is an intelligence-gathering effort by a state-sponsored actor aiming to infiltrate systems for espionage purposes. This is less supported due to the lack of sophisticated targeting and the use of a broad, non-discriminatory approach.
- Assessment: Hypothesis A is currently better supported due to the nature of the attack and its execution, which aligns with typical cybercrime tactics. Indicators that could shift this judgment include evidence of targeted attacks on high-value individuals or organizations.
3. Key Assumptions and Red Flags
- Assumptions: The attackers are primarily motivated by financial gain; the campaign is currently limited to the UK; the use of ScreenConnect is a deliberate choice for its legitimacy.
- Information Gaps: The identity and location of the attackers; the full scope of the campaign’s reach beyond the UK; potential links to other cybercrime activities.
- Bias & Deception Risks: Confirmation bias in attributing the campaign to cybercriminals without considering espionage; potential manipulation of open-source information by the attackers to obscure their true intent.
4. Implications and Strategic Risks
This development could evolve into a larger-scale campaign if not mitigated, potentially affecting a wider range of targets and regions. The use of social engineering tactics highlights vulnerabilities in personal and organizational cybersecurity practices.
- Political / Geopolitical: Minimal direct impact, though widespread exploitation could strain international cybercrime cooperation efforts.
- Security / Counter-Terrorism: Increased risk of unauthorized access to sensitive systems, potentially leading to data breaches.
- Cyber / Information Space: Highlights the need for enhanced cybersecurity awareness and training to counter social engineering threats.
- Economic / Social: Potential financial losses for individuals and businesses; erosion of trust in digital communications.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of similar phishing campaigns; educate users on identifying and avoiding social engineering attacks; engage with cybersecurity firms for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop partnerships with international law enforcement to track and disrupt cybercrime networks; invest in cybersecurity resilience measures for individuals and organizations.
- Scenario Outlook:
- Best: Campaign is contained with minimal spread, leading to increased awareness and improved defenses.
- Worst: Attackers expand operations globally, causing significant financial and data losses.
- Most-Likely: Continued targeting of individuals with gradual geographic expansion, prompting ongoing mitigation efforts.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cybercrime, social engineering, remote access tools, phishing, cybersecurity awareness, information security, UK
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us